A recently released report by information security threat intelligence project DIFR detailed how a ransomware infection could take only 29 hours to fully compromise the targeted networks. Apparently the operators of this attack employed a variant of the Ryuk ransomware, allegedly linked to Russian hacking groups.
Apparently it all started with a malicious email that included a link capable of redirecting users to a website to download the Bazar/Kegtap loader, injected into various processes, as well as performing a recognition step on the infected system using preloaded utilities on Windows systems.
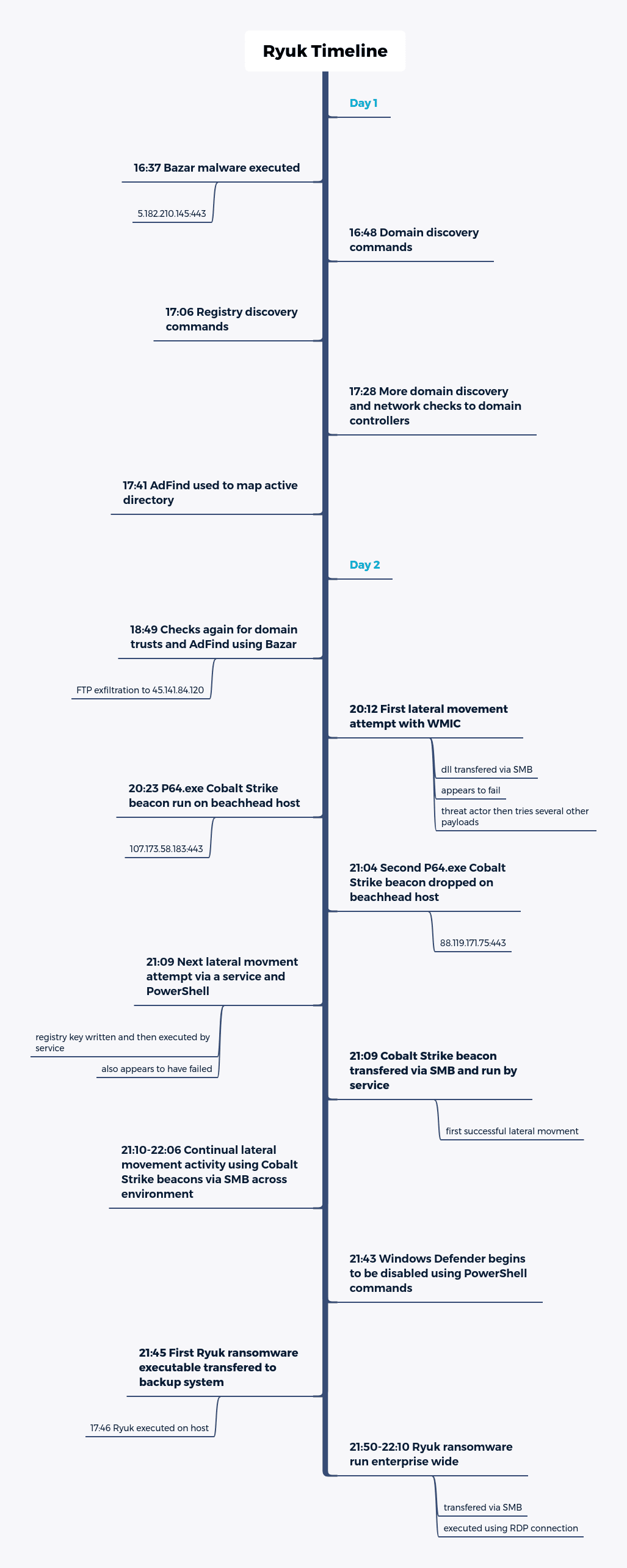
Once installed on the infected network, Ryuk remained inactive for about a day and then began a second stage of system recognition using the Rubeus tool. The data was leaked to a remote server and threat actors began a lateral movement; eventually, threat actors used remote service execution attacks with PowerShell to maintain the attack.
It should be noted that Ryuk operators also disabled Windows Defender and ran the ransomware one minute after being transferred via SMB from the pivot, going on to store the encrypted backups. The ransomware was also transferred to the remaining hosts on the network using SMB, taking advantage of an RDP connection to run the malware from the dynamic domain controller.
In its report, DFIR mentions that: “The malicious campaign only took about 29 hours from the initial execution to the total commitment of the target; if security teams lose the first day of recognition, there are less than three hours left to contain the attack before the infection completely affects the target system. In this incident, threat actors demanded a ransom of about 600 Bitcoin (about $6 million at the current exchange rate).
Combating this practice remains one of the industry’s top priorities. This week, Microsoft revealed the closure of trickbot’s infrastructure, a botnet used as the primary means of delivering some ransomware variants, including Ryuk.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











