According to the information contained in some emails obtained through a request for information, the Federal Bureau of Investigation (FBI) decided to send its “Fly Team”, a brigade specializing in the fight against terrorism, to Portland last July. The primary task of these agents was to interrogate the arrested protesters, as well as to begin with the “initial exploitation of confiscated communication devices.”
These emails suggest that the federal agency has been employing sophisticated technological developments to map protest networks considered left-wing or radical in the light of the presidential election.

Nearly a thousand civilians were arrested in Portland during protests over the assassination of George Floyd, partly as a result of the federal government’s vigorous stance, including the use of non-lethal weaponry, tear gas and paramilitary and specialized tactical groups, including the Fly Team. The messages obtained, signed by former special agent George Chamberlin, mention that Fly Team would support the follow-up to the investigation into the protests. An official familiar with the Portland operation said the email had a funny intent and argued that there was no difference between the legal authorities governing the Fly Team and those that apply to local agents.
A few days ago, several members of the House of Representatives’ National Security Committee claimed that the Department of Homeland Security (DHS) retained the mobile devices of some of the protesters arrested for months. Jim Himes, a congressman for the state of Connecticut, says DHS sought to drive the extraction of data contained in these devices in order to identify connections between groups of protesters.
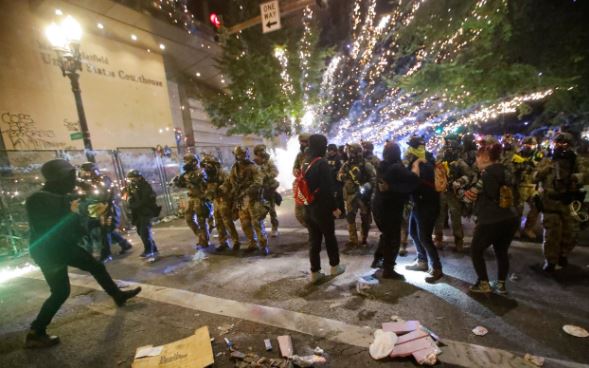
This work would also have been promoted by the Office of Intelligence and Analysis (I&A), an agency that is part of Homeland Security. Although this request did not cause the expected result, emails show that DHS staff maintained contact with Portland Police to follow up on this case.
Although research agencies claim that they require the help of technology companies to access these devices, this is actually part of an encryption campaign, as the FBI and other federal agencies have access to technology capable of “cloning” the information contained on a device, including emails, text messages, contact list, and location data.
A former FBI official who requested anonymity mentions that Fly Team might have access to this technology: “Sometimes administrative workers have no idea of the technological developments they work with at the agency,” the former official said.
The emails obtained do not in any way suggest that investigative agencies actually gain access to the retained devices; anyways it is difficult to dismiss this hypothesis because of the extensive powers with which the FBI can operate, including Order 12333, authorizing the agency to conduct “physical records without consent and physical surveillance” for intelligence purposes. While the U.S. Fourth Constitutional Amendment states that any government office must obtain a court order to conduct any investigation, an exception has also been established in “pressing cases,” applicable when lives are deemed to be at risk.
Specialists who have spoken out about it seem unsurprised by Fly Team and their involvement in the investigations of the arrested protesters. This unit was created during Robert Mueller’s management at the helm of the FBI due to the need to strengthen intelligence work in the U.S. after the September 11, 2001 attacks. Members of this counterterrorism unit specialize in collecting evidence in electronic media, remote surveillance, interrogation of potential criminals, among other skills: “Mueller believed that the reporting system was insufficient; I wanted to send investigators wherever it was needed for more effective work,” says Raymond Holcomb, a retirement FBI agent who helped integrate the first Fly Team.
After constant questions about fly team operations in Portland, the FBI issued a statement noting that the agency is trying to identify and disrupt criminal activity: “These investigations have been conducted in accordance with all legal requirements; peaceful protests are not under investigation.” Local authorities mention ignoring Fly Team’s presence during protests.
For political experts, the presence of this team is a sign of the strict stance the U.S. government has taken on social mobilizations, theorizing that domestic terrorism groups and anarchic groups like Antifa are behind these phenomena.

Nevertheless, former and current FBI members agree on their stance on Antifa, considering it to be more of an ideological current than an organization capable of mobilizing masses and coordinating armed groups. In any case, everything related to Antifa is under the strict scrutiny of Donald Trump’s administration.
Democratic Sen. Ron Wyden mentions that the information available about Fly Team’s activities raises questions about law enforcement by federal agencies: “The time has come for the FBI and DHS to respond for the actions of their agents in Portland.” It is clear that this is a delicate investigation that becomes much more controversial in the face of the proximity of the elections in the U.S., so it also represents an opportunity for groups to opponents of the current regime.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











