Specialists have detected a new variant of ransomware for mobile devices that abuses notification mechanisms and home button to lock users’ screens. Identified as “AndroidOS/MalLocker.B”, this malware is hidden in Android apps available on unofficial platforms.
Unlike their conventional counterparts, Android mobile ransomware variants don’t actually encrypt victims’ files, but simply lock the device. Upon completion of its installation, the ransomware seizes the screen of the device and prevents the user from simply ignoring the ransom note; in some cases ransom notes may appear as false notifications from investigative agencies.
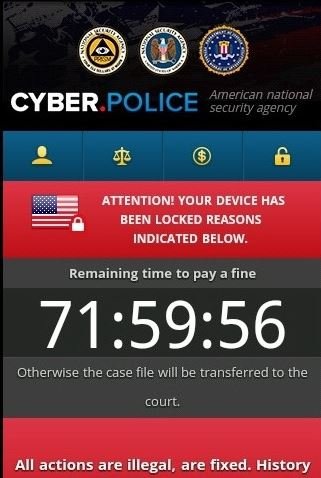
This is one of the most popular mobile ransomware attacks and has been active for almost six years. During their evolution, these ransomware variants have found a way to abuse some functions on smartphones to prevent users from unlocking the device.
According to the experts, MalLocker.B has some variants of that technique; in the first instance the malware abuses the incoming call notification, using it to display a window that covers the entire area of the screen. Subsequently, the malware abuses the “onUserLeaveHint()” function, used when users want to leave an app in the background. MalLocker.B abuses that function to set the ransom note on the user’s device.
By abusing these functions, threat actors manage to lock the user’s screen and prevent victims from ignoring the ransom note. Similar malicious tools have been detected previously; in 2017 ESET reported a variant of ransomware known as DoubleLocker, capable of abusing the accessibility service to reactivate automatically after the user pressed the home button.
MalLocker.B contains code that is too rudimentary to pass Play Store patches, so users are advised to avoid installing Android apps that they downloaded from third-party locations, such as forums, website ads, or unauthorized third-party app stores.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











