Cybersecurity specialists from TechCrunch report that Dr Lal PathLabs, one of the main lab testing firms operating in India, has exposed an enormous cache of patient data through an unsecured public server. The New Delhi established company, grants services to up to 70,000 patients a day, and has became one of the main resources for COVID-19 tests in the country with the approval of Indian government.
According to the report, the company was storing hundreds of spreadsheets packed with sensitive patient data using an Amazon Web Services (AWS) implementation. The exposed data was stored without a password, so any user could have accessed it. Sami Toivonen, an Australia-based security researcher, found the AWS bucket completely exposed, notifying it to the company, which shut down the access shortly after. Nor the expert or the labs know for how long the data remain exposed.
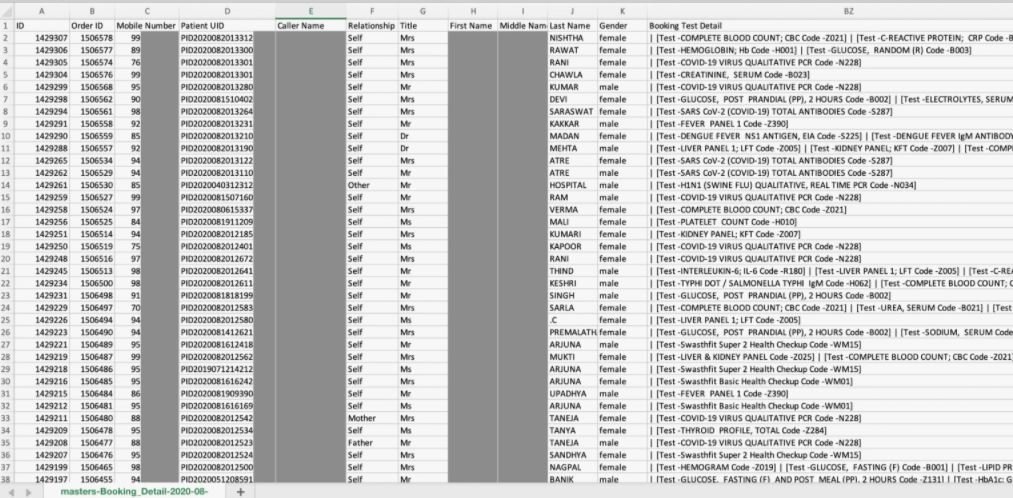
Toivonen also mentions that the exposed spreadsheets are full of millions of patients’ records and lab tests. Besides, each spreadsheet contains details such as full names, addresses, gender, medical history, among other data. It was also mentioned that the spreadsheets specify if patients tested positive for COVID-19.
The TechCrunch experts dot a sample of the exposed files with verification purposes, finding out that the patients’ data was 100% legitimate.
After notifying to the company, the expert told to TechCrunch: “When I discovered this I was really surprised that another publicly listed organization had failed to secure such data, but I know this is a team sport and everyone’s responsible for it. Anyways, I’m glad that they secured it immediately, this kind of incident could affect millions of people in several ways”.
On the other hand, a Dr Lal PathLabs spokesperson mentioned that the company was aiming to improve its security systems in order to prevent further similar incidents.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










