Group-IB security experts have detected a new fraudulent campaign in which threat actors use the image of the popular Zoom video conferencing platform. Scam traders offer alleged monetary compensation related to COVID-2019, attracting victims to fraudulent websites where criminals seek to steal their financial information and even their money.
One of the main measures for combating the pandemic is social distancing, so public and private organizations around the world are increasingly turning to the use of remote communication platforms such as Zoom, which has caught the attention of multiple groups of threat actors in search of making easy money.
This investigation began after multiple users began reporting fraudulent-looking emails allegedly sent by Zoom. These messages offered “COVID-19 compensation”, which any user could claim by accessing a website via an attached link. By clicking on that link, users are redirected to various fraudulent sites to steal information from their bank cards and online banking accounts.
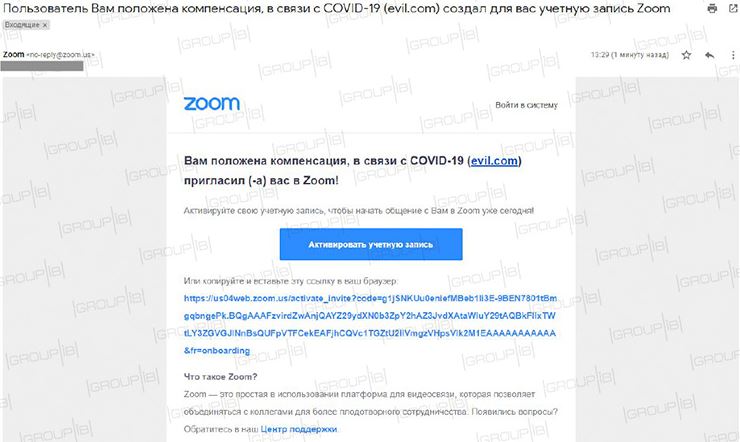
The most worrying thing about this campaign is that threat actors are not using a fake domain, but managed to compromise one of the services: “By registering for Zoom, the app asks the user to enter their first and last name with the ability to use up to 64 characters in each field; criminals take advantage of this feature to write the phrase <<You are entitled to compensation for COVID-19>>, in addition to the fraudulent link.
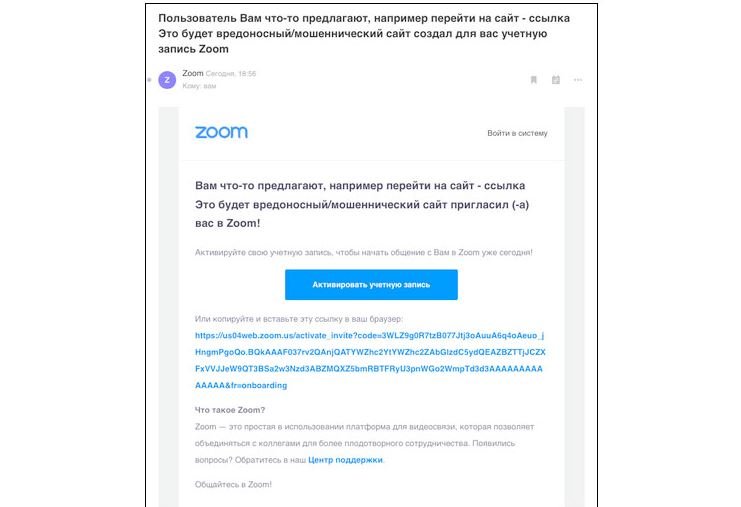
Sending phishing messages is also possible due to abuse of a legitimate service. After completing registration, Zoom offers the possibility to invite up to 10 new users, specifying their postal address. Threat actors can enter the addresses of potential victims, so they will receive an email in the name of Zoom (via no-reply@zoom.us), although the content is generated by the scam operators.

The sites used by threat actors had titles that appeared to be from civil and even lottery organizations such as “Official Compensation Center”, “Express Lottery”, “Online Bank”, among others.
This fraudulent campaign is similar to a scheme detected by Group-IB in April this year, in which threat actors managed to defraud users in Russia by about 250 thousand rubles.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











