While many users ignore it, GitHub has native tools on the platform that allow you to search for vulnerabilities before your projects move to definitive instances. Code scanning is now generally available and can be enabled by anyone in their public repository.
These tools have progressed to the execution of a security scan that does not require further intervention from the developer. Code scanning integrates with GitHub Actions to maximize your computer’s flexibility. The tool scans code as it creates and displays actionable security patches within pull requests and other regular-use GitHub features, automating security processes and preventing failures from reaching users in these developments.
CodeQL drives code scanning. This is considered the most powerful analytics engine in the world, with more than 2,000 CodeQL queries created by GitHub and the developer community.
Code scanning, on the other hand, is based on the SARIF standard, which allows the integration of third-party analysis engines to view the results of security tools in a single interface, as well as exporting the results through a single API.
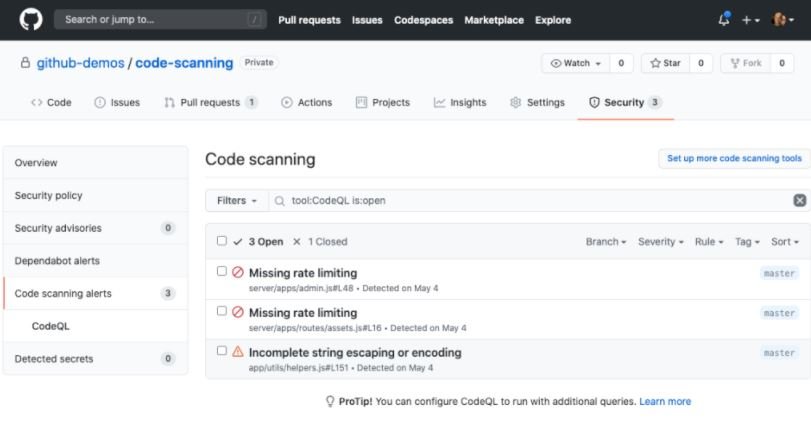
According to the developers, since the release of the beta several objectives have been achieved including:
- More than 1.4 million scans in more than 12,000 repositories, en enabled detection of various security issues such as remote code execution vulnerabilities, SQL injections and XSS failures
- Fixed about 72% of vulnerabilities detected in code scans, which can be considered a success compared to 30% of fixed bugs per month fixed in the industry
- Partnerships have been established with at least 10% of commercial and open source security providers. allowing developers to run CodeQL natively on GitHub
Code scanning is free for public repositories, while private repositories can access this tool through GitHub Enterprise.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











