The most recent weeks have been stirred for TikTok. Experts mention that Donald Trump, president of the United States, has ordered ByteDance, TikTok’s parent company, to sell its assets in the country, as well as issue executive orders banning the use of Chinese apps TikTok and WeChat in case this sale does not material in the coming weeks. On the other hand, ByteDance filed a lawsuit against the Trump administration.
This is the kind of news about popular apps that threat actors expect to hear, as it can present the ideal opportunity to attack. In cases like this, when an app is banned from official platforms (App Store, Play Store), users start looking for alternatives to use prohibited apps, exposing themselves to hackers who develop malicious copies. Recently thousands of users in the U.S. received an SMS message inviting them to download the latest version of TikTok on hxxp://tiny[.] cc/TiktokPro; In fact, this link led users to a fake app that could steal their login credentials and gain high privileges on the operating system, leaving the user exposed to various attacks.
This is not the only case, as a group of experts found another fake app variant of TikTok that is actually a spy software (also known as spyware) with Premium features to track all the victim’s activities.
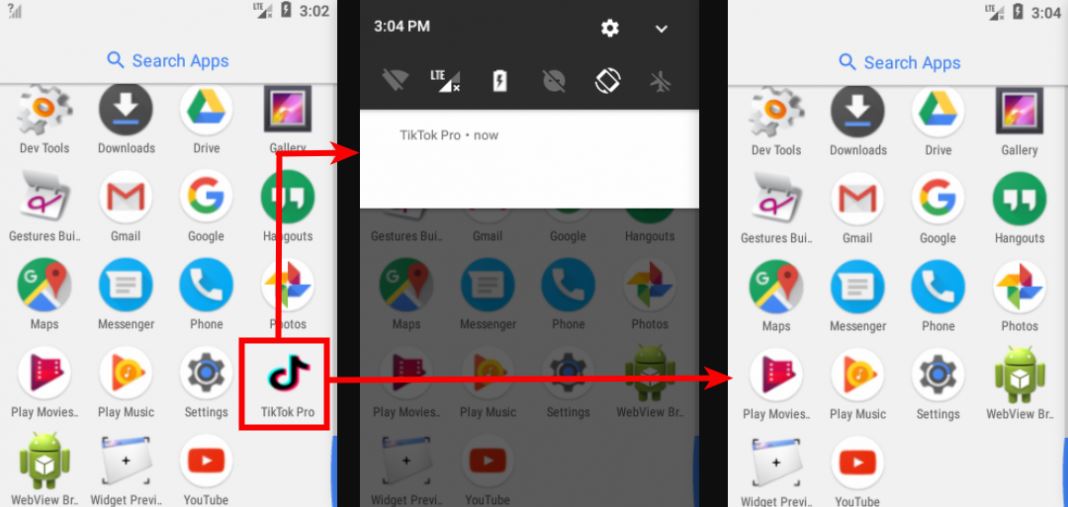
After being installed, this malicious app is presented on the victim’s device under the name TikTok Pro, and starts working immediately by sending a false notification and hiding its icon on the screen, making it difficult to uninstall. According to reports, this malicious app has the following capabilities:
- Theft of SMS messages
- Sending SMS messages
- Collection of the victim’s location data
- Removing photos and other files
- Executing commands
- Taking screenshots
- Phone access
- Ability to launch other apps
- Theft of credentials from Facebook and other apps
Facebook phishing
This spyware has the ability to steal Facebook credentials using a fake login page; upon receiving the CUIFXB command, spyware launches this page trying to steal the target user’s credentials. Subsequent analyses showed that spyware was developed by a framework similar to spynote and Spymax, indicating that it could be an updated version of these tools, available to any user, even those with little hacking knowledge.
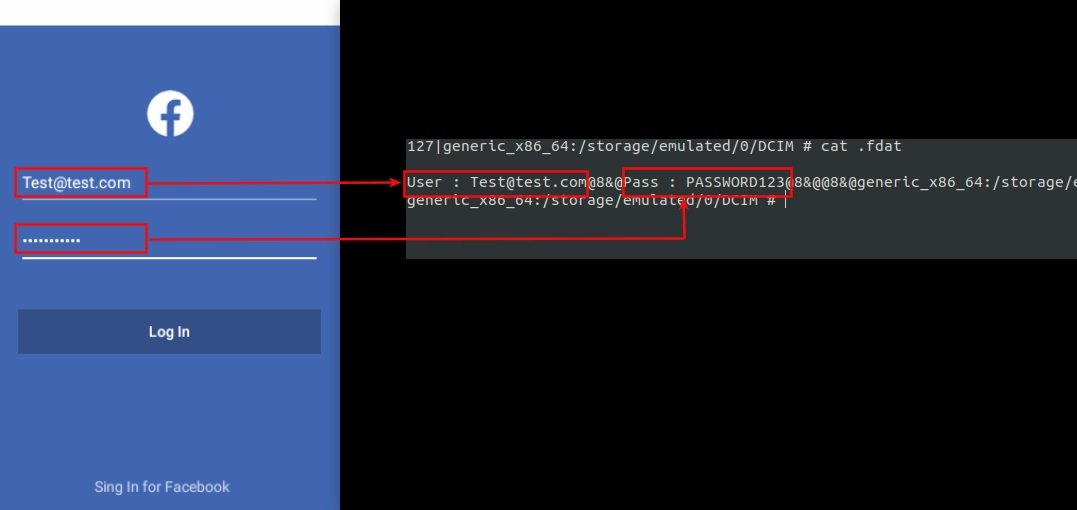
Experts point out that this tool communicates using dynamic DNS, so hackers can easily configure the Trojan to communicate with low-end servers. Other functions include executing arbitrary commands on the target device, taking screenshots, finding location, and all the capabilities of spyware.
This is an interesting feature, as the theft of login credentials is something that has not been observed in tools like Spymax, although it is not completely alien to a spyware app. Finally, experts mentioned that the TikTok Pro framework allows any user to develop a spyware app that will be passed through any other tool; in total, researchers have found 280 malicious apps created with this framework.

Remember that it is not recommended to install apps from untrusted sources, as this is one of the main vectors of mobile security risk.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











