Security threats against telecommunication systems remain a serious problem, specialists in an exploit writing course say. Voice over LTE (VoLTE) packet-based telephony service, integrated into the Long Term Evolution (LTE) standard, has become one of the most used technologies by telecommunications operators. As a method of encrypting phone calls, VoLTE encrypts data between the phone and the network with flow encryption, which generates unique keys for each call, avoiding reuse of the key flow. Due to its widespread use, a vulnerability exploit campaign in VoLTE could affect a large number of users worldwide.

A team of specialists from Ruhr University, Germany, and New York University in Abu Dhabi has developed a method to abuse a flaw in LTE implementation to intercept the contents of an encrypted VoLTE call. Dubbed “ReVoLTE“, this attack method could allow threat actors listening to any call stealthily using key flow reuse.
The full investigation appears at the 29th USENIX Security Symposium.
What is this attack?
According to the exploit writing course specialists, ReVoLTE exploits the reuse of the same key flow for two calls within the same radio connection, which is possible due to a base station deployment (eNodeB) flaw. Researchers randomly scanned multiple selected radio cells to determine whether this weakness is present widespread, finding that the flaw affects 12 of the 15 base stations analyzed.
The main goal of the experiment configured by the researchers was to intercept the data during a phone call between User A and User B. To do so, researchers (acting as attackers) begin by detecting User A’s encrypted radio traffic, managed on a vulnerable base station.
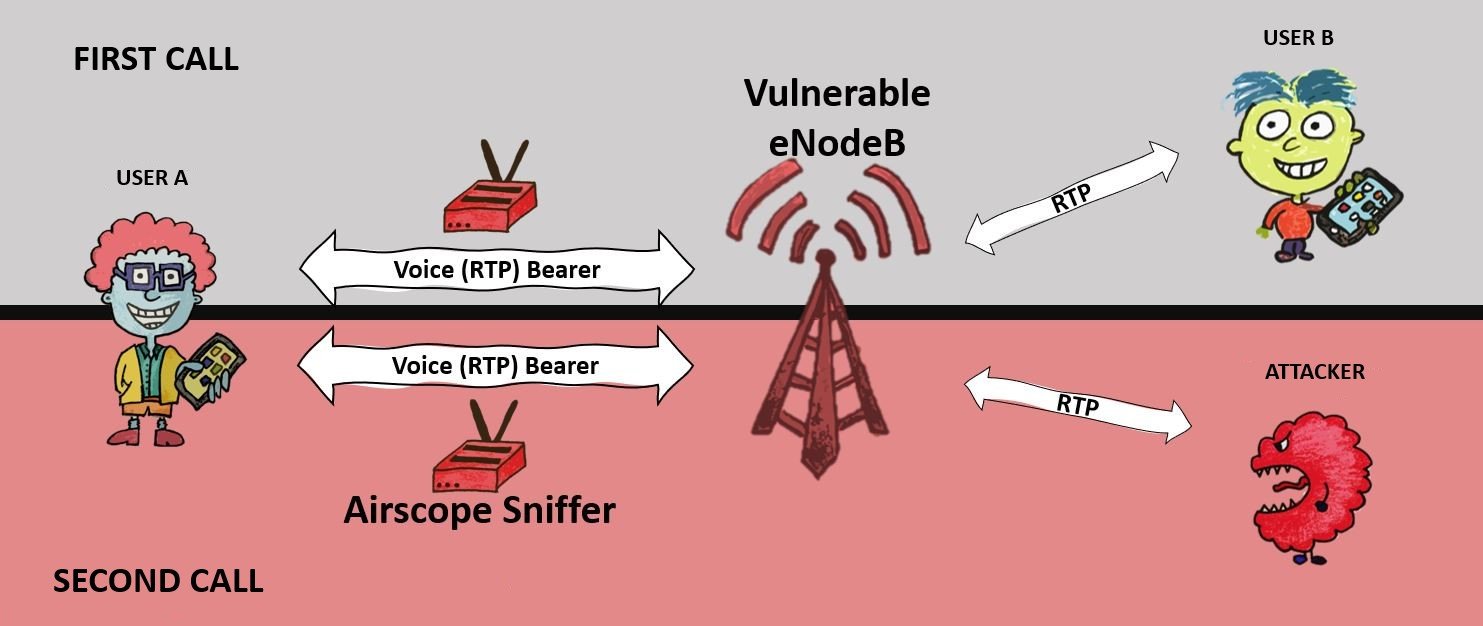
After the first call between the target users ended, the attackers called User A to initiate a second phone call; during this second call, the threat actors detected User A’s encrypted traffic, managing to record the unencrypted sound.
To decrypt the target call, threat actors will have to face a couple of variables: First, hackers must modify the text are formatted (recorded on the attacker’s phone) using the encrypted text of the first call, which will allow to calculate the key flow of the second call; because of the security flaws of the base station, the key flow is the same as on the first call.
The first call is decrypted using the XOR encryption algorithm in the key flow of the first call; we should remember that attackers must engage in a long enough conversation with the target user to get most of the call target decrypted. For example, if the conversation between attackers and victims lasts 5 minutes, 5 minutes of the previous conversation can be decrypted, the exploit writing course specialists mentioned.
Attack risk is real
Although this is a complex attack, researchers considered it necessary to notify providers through the Coordinated Vulnerability Disclosure Program, managed by the GSMA Association; an alert was filed in December 2019. In response, the Association asked telecommunications providers to develop updates for compromised base stations.
At the time of public disclosure of this method, suppliers should have already released the necessary fixes in addition to requesting their installation. Companies in Germany, where the base stations analyzed are located, have already released the relevant updates. It is necessary to consider that dozens of suppliers worldwide could be affected, so it is essential to raise awareness of these failures and their possibility of exploitation, as specialists fear that ReVoLTE is not the only method of attack against VoLTE call encryption.
Researchers also developed an app that detects whether base stations are vulnerable to a ReVoLTE attack, requiring a smartphone with a version of the Android operating system compatible with VoLTE and root access, as well as a Qualcomm chip. This tool is available on GitHub.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











