An unidentified threat player has leaked data from Transnational Bank in Kenya. The bank’s website has been out of service for at least a couple of days, hard drive destruction service specialists mentioned.
The incident was revealed via a Twitter account managed by user Szandor Tigris (@SzandorTigris), who claims to be a member of the group of malicious hackers behind the attack, who threatened bank staff with sharing the compromised information, a threat that was fulfilled just a few hours ago. Through a Drive link, the alleged hacker revealed information extracted from Transnational Bank, which includes sensitive user data.
“A bank in the Republic of Kenya was hacked”, mentioned the first tweet posted by Tigris. The tweet was followed by several posts supposedly linked with the hacker, as hard drive destruction service specialists mentioned.
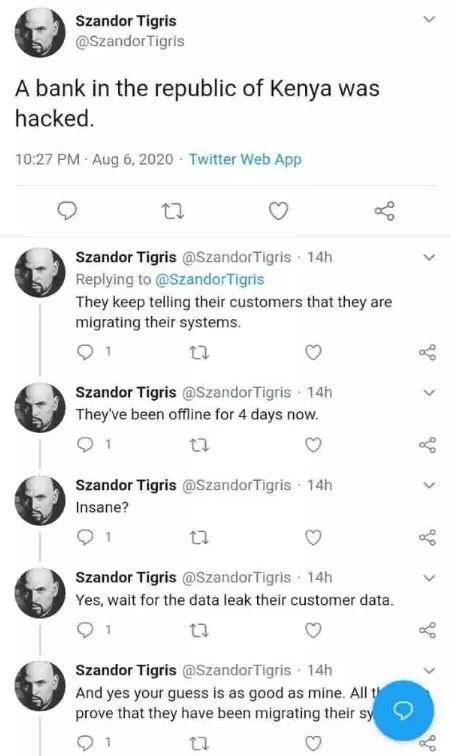
The bank has taken a position contrary to the user’s assertions, as the official version shared with the bank’s customers mentioned that the bank is implementing an IT system migration process, so it was necessary to temporarily disconnect its website. However, the Twitter user maintained his version, inviting the bank’s executives to be honest with their customers and acknowledge that they have been victims of a cyberattack.
With no response from Transnational Bank, the alleged hacker concluded a thread of tweets mentioning that time had run out, so the bank’s information would be leaked online. Hard drive destruction service specialists who have followed the incident closely do not seem to match in their hypothesis about the hacker’s motivations, as this incident does not appear to have anything to do with paying a ransom or a similar crime.
In its most recent statement, the bank only apologized for the inconvenience caused by its website’s inactivity period, completely dismissing the alleged attacker’s version.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











