Surveillance has become one of the leading practices of governments around the world, mentioning experts in a pentesting course. A few years ago, during a series of protests in North Dakota, USA, technology expert Cooper Quintin received multiple reports on the use of surveillance mechanisms against protesters, mainly IMSI catcher devices.
This technology, also known as Stingray, functions as a cell tower, tricking receiver devices into revealing their near-accurate location. In addition, authorities can also use these devices to extract information from mobile devices.
Because of these reports, Quintin tried to take some precautions. During the protest, the expert used a software-defined radio and an Android app to look for abnormal signals. In a later pentesting course report, Quintin mentioned that he was using software for 2G technology, which would have prevented him from detecting 4G signs, if any.
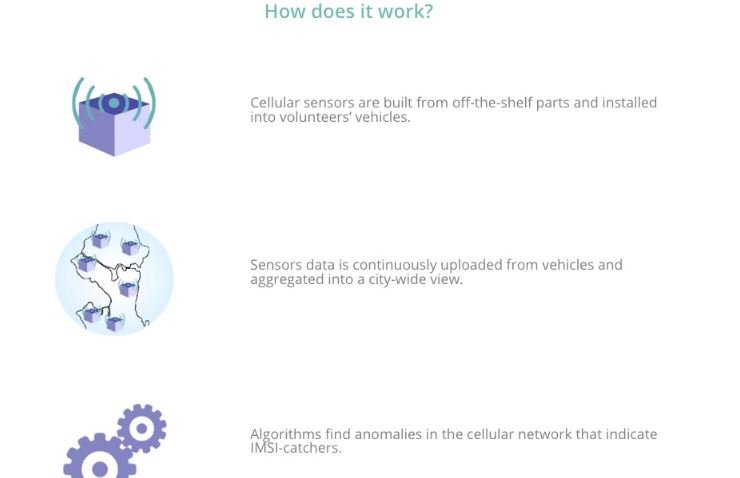
It’s been almost four years since then, and Quintin has apparently refined his method. A few days ago, the expert and a collaborator known as “Yomna” and the Fake Antenna Detection (FAD) Project launched an open source project designed to detect IMSI receivers running on 4G networks. Dubbed Crocodile Hunter, this hardware and software kit includes a code to measure the cellular network in a given area, as well as an application programming interface that collects information and shares it with other researchers.
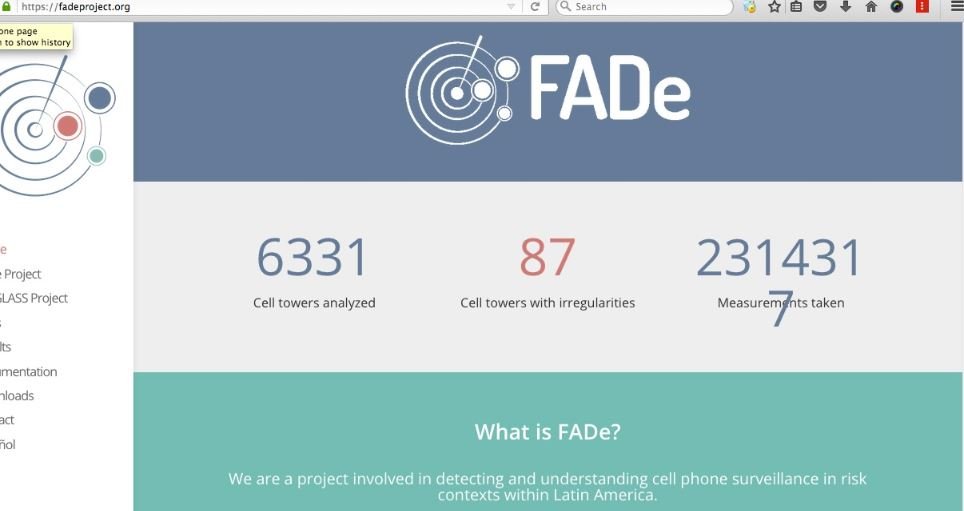
Quintin says no other IMSI receiver detector has such advanced features as Crocodile Hunter: “We seek to refine the accuracy of the tool to perform a clearer mapping of surveillance systems, mainly used during protests in the United States and the rest of the world,” the expert said. Crocodile Hunter will be featured at the DEF CON virtual conference.
Whether this toolkit works remains to be seen; if so, it would attract the attention of thousands of users and security agencies, say experts in pentesting course. For example, the Department of Homeland Security’s Immigration and Customs Enforcement Agency, which has used this technology for years, would be limited when the systematic surveillance they operate with was checked, which could be a problem.
On the other hand, agencies such as the Federal Bureau of Investigation (FBI) might consider tools like Crocodile Hunter to meddle in their regular work, which could get developers in trouble.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











