Despite its security measures, Play Store remains a great support for threat actors, as mentioned by web application penetration testing experts. The latest malicious campaign deployed through this platform has to do with a set of malicious apps that infest Android devices with invasive and random advertising. In addition, experts mention that these apps are able to hide their icon after they are installed on a device.
White Ops researchers detected a total of 29 potentially malicious apps with a lot of ad traffic and over 3.5 million downloads. Developed by the firm “ChartreuseBlur“, these apps focus on camera effects and photo editing.
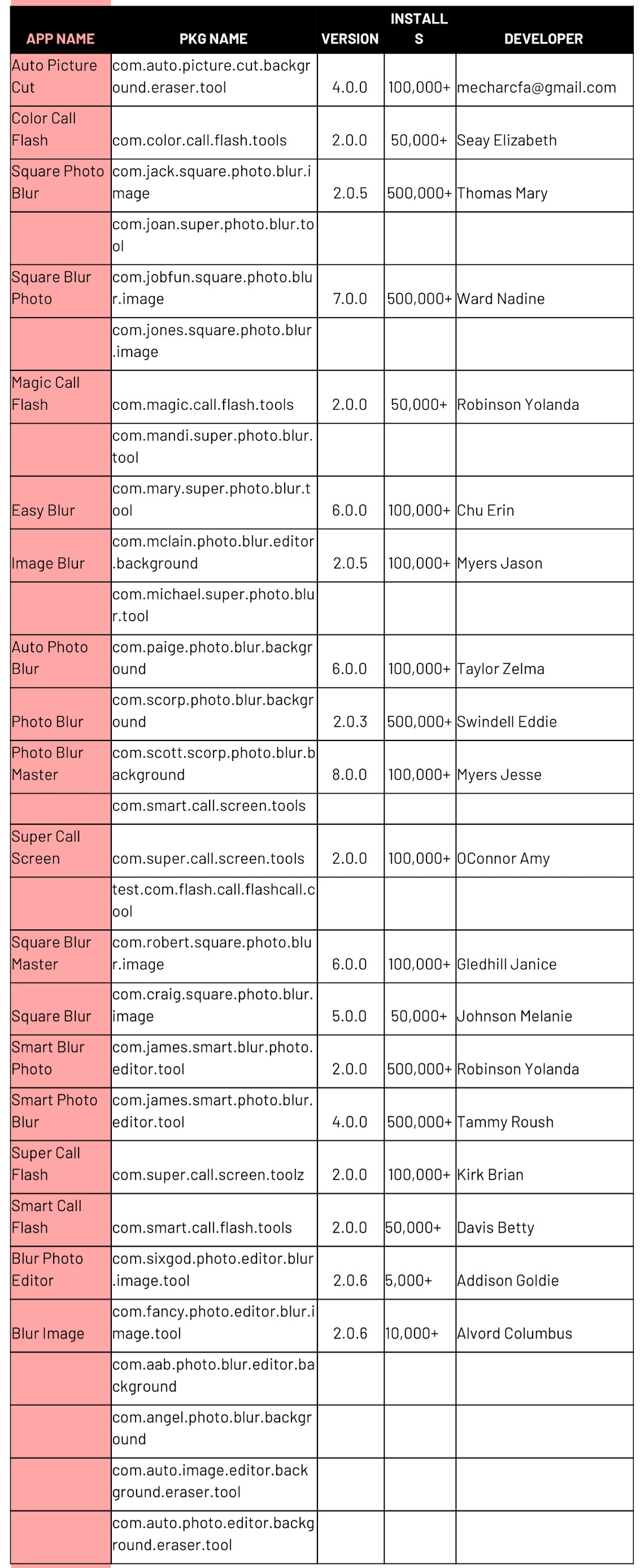
The features of these applications make their uninstalling process very complicated, as users must even enter the settings menu of their device to check if the application is actually installed, mentioned the experts in web application penetration testing. Another method to verify this is to check the list of running processes.
One of the apps that caught the attention of specialists was Square Photo Blur, as they consider it behaves similarly to many other malicious applications. After being downloaded, this app begins to infest the device with ads with no apparent sense, unexpected behavior in any software available on the Play Store. The platform removed this app shortly after receiving some complaints.
Subsequently, web application penetration testing experts concluded that the set of applications analyzed contained a three-stage payload; while the app code appears normally in the first two stages, the third shows signs of suspicious behavior.
This third stage is exactly where the malicious code hidden within the application begins to generate advertisements, besides that its presence can be seen in the form of com.bbb packages. Invasive ads can appear as soon as the user unlocks the phone or when starting charging or switching from mobile network to WiFi connection.
Finally, by selecting the app icon, researchers discovered that Square Photo Blur is a kind of empty shell whose developers managed to bypass Play Store controls.
The list of malicious applications has already been reported, these developments are expected to be removed from the platform as soon as possible. For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











