There are many techniques to steal the victim credentials. Have you ever imagine how cyber criminals are working! Cyber criminals also use tools to hijack accounts. Researchers of International institute of Cyber Security suggested many ways to secure your social media accounts from being hacked.
Today we will walk through top 5 tools used by Cyber mafia or Cyber Criminals to hack innocent accounts. Once these accounts are hacked, they are used for illegal purposes.
1. Account Hitman Tool
Account Hitman tool is the fastest tool to steal the victim’s credentials. Using this tool, millions of accounts were hacked. This uses the brute forcing techniques to attack. It is used to hack accounts with weak password. Later on reuse them for unethical purpose.
- Click on Download, to use Account Hitman tool.
- Download the Zip file and then extract it. After extraction we get below files.
- After opening, Account Hitman will download the requirements packages of the tool and then opened up.

- Once the tool is downloaded we will see current version and few TABs. We will walk through TABs one by one.
- Combos TAB: In the combos, we can add the wordlist to brute force any account. These wordlist can also be wordlist sold in the black market.
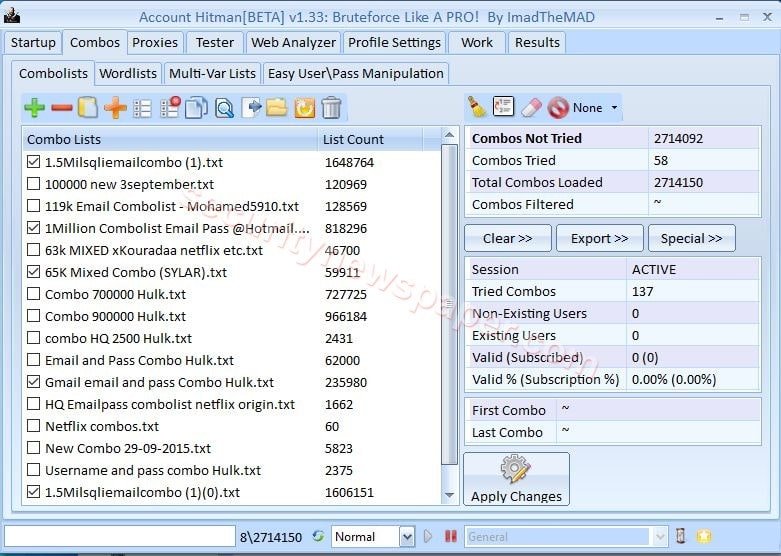
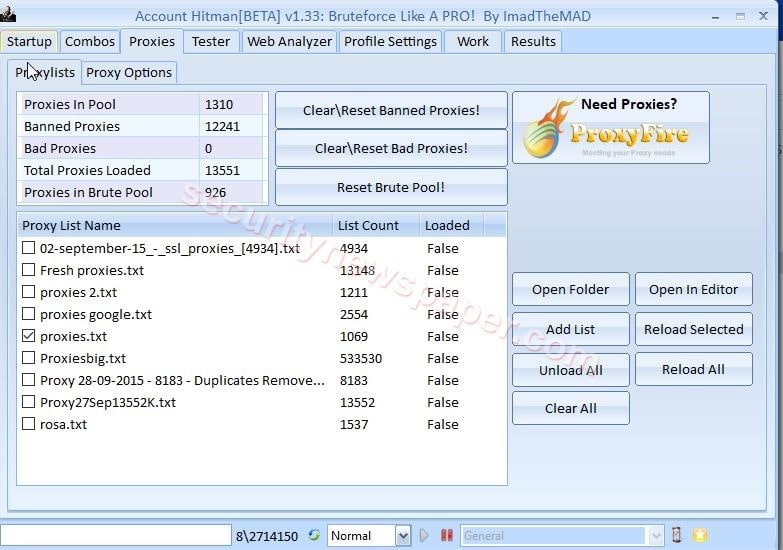
- Proxies TAB: Here, we have proxies list to hide our identity while running tool.
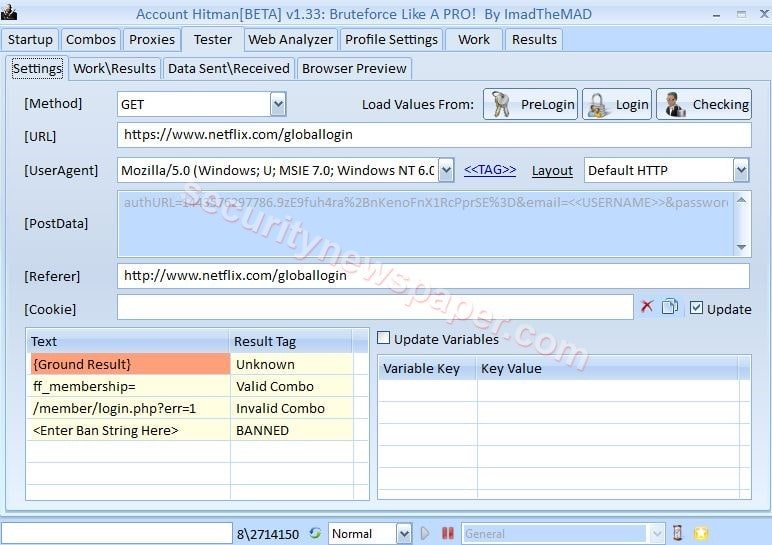
- Tester TAB: In the tester columns, we have an option to send the manual HTTP(s) request to the web server. We can set the Methods (Get and Post), URL, browser UserAgent, post data.
- Web Analyzer TAB: Here, we can monitor all the request send and received.
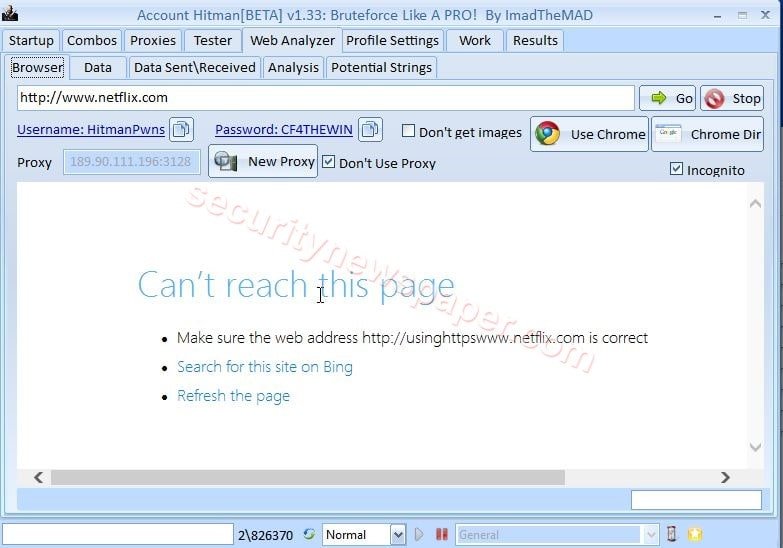
- Profile Setting TAB: Here we have option to manually set the profile for scanning.
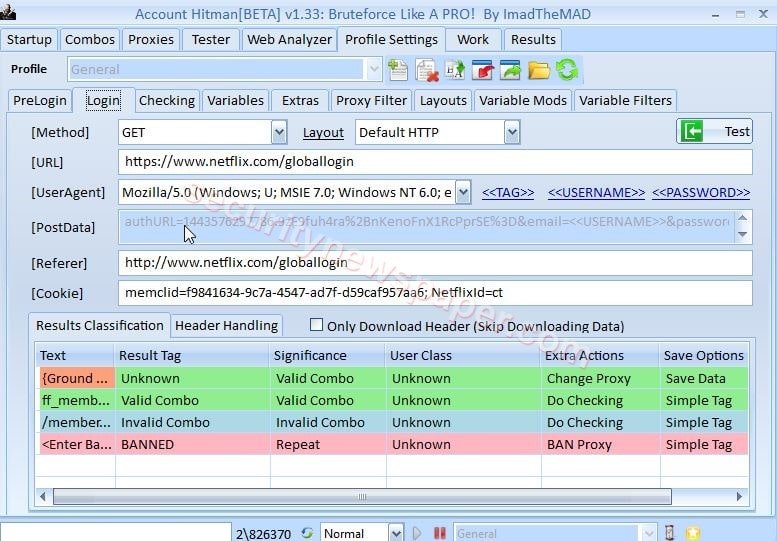
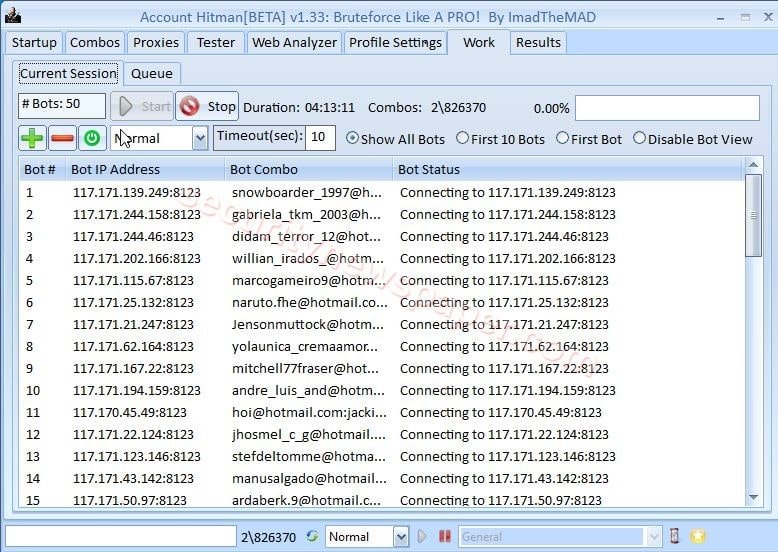
- Work TAB: Once the brute force attack is performed, in this TAB we can see the logs and the status of attack.
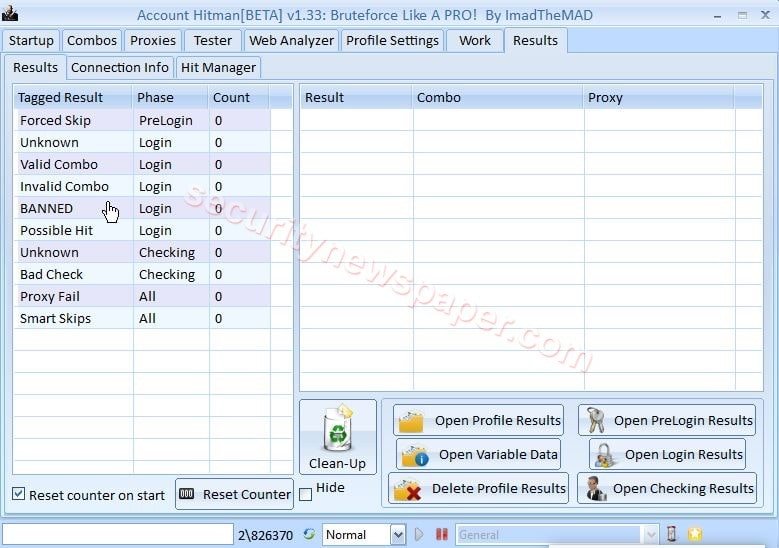
- Results TAB: In this column, we can view the results of the attack with the count.
2. Sentry MBA
Sentry MBA is another tool that most of the cyber criminals are using to take over the user accounts major websites with sentry MBA tool. Using this tool, cyber criminals target many accounts with a huge combo lists of usernames and passwords. Most of the hackers use this tool for credentials stealing. Sentry MBA tool has user-friendly interface.
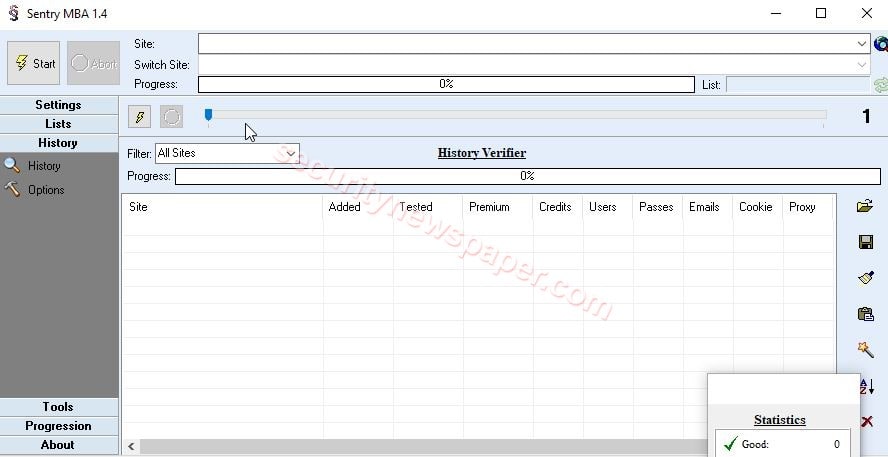
From the past few months, this tool is getting more popularity among users. To perform an attack on the target website, we need the configuration file, Proxy file, and Combos list. This Sentry MBA tool is freely available on the internet. Click On Download to check how this tool looks.
- After download, extract the zip file
- Now, launch the sentry MBA tool.
- Here, we can view the version details of sentry MBA Tool
- We also have few different column here.
- Setting: In this column, we can set a few general options, proxy settings before performing the attack on the target website.
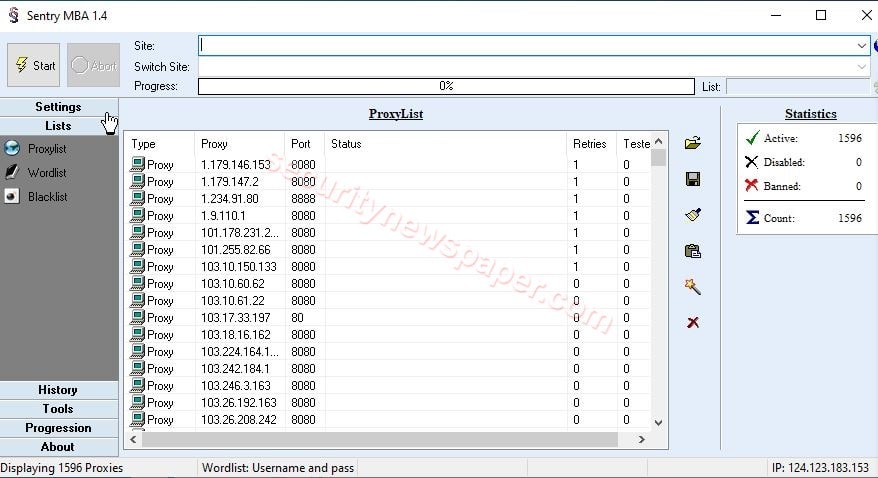
- Lists: In this column, we can import the wordlist and proxy list to perform an attack.
- History: In this column, we can view the previous attacked data.
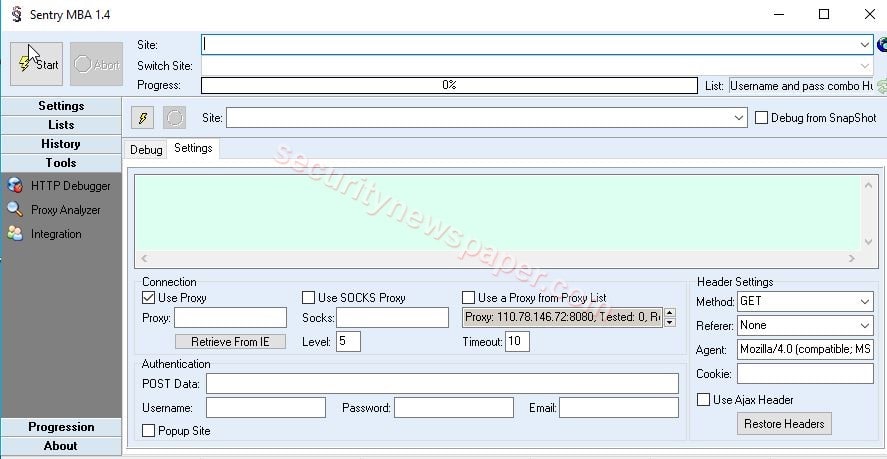
- Tools: Here, we can debug the related to attack.
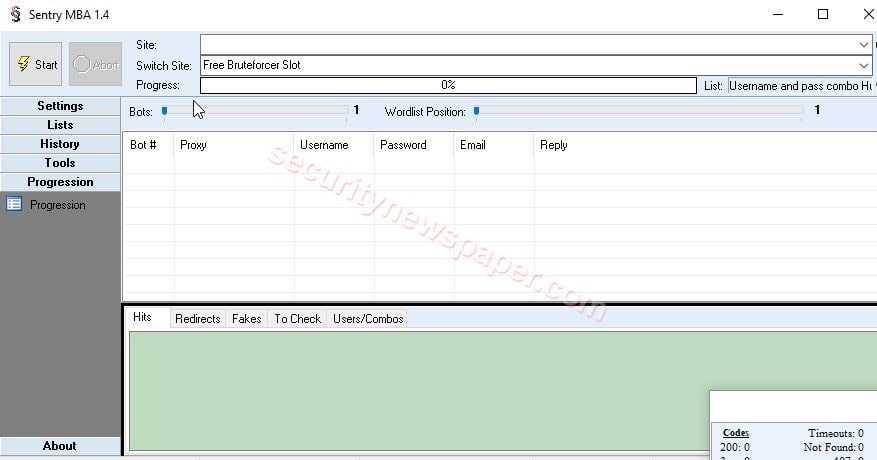
- Progression: Here, we can check the status of the attack on each and every user’s account.
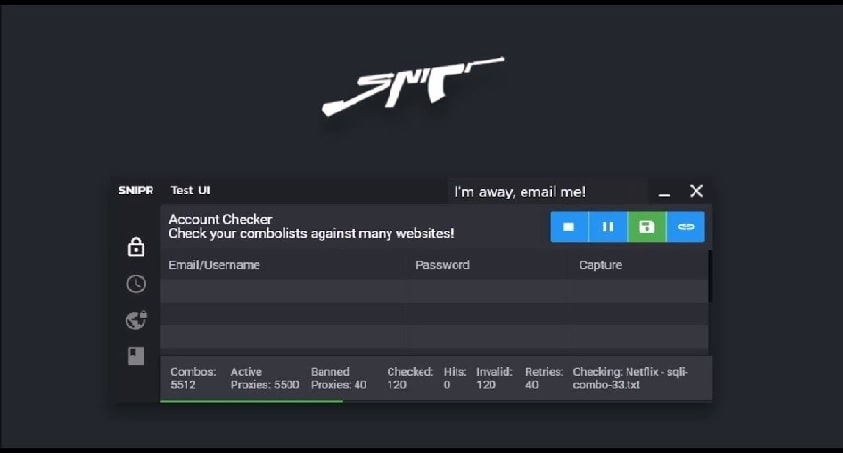
3. Snipr
Snipr is a cracking program, which can crack any users account by specifying the wordlist (combo list which contains the list of usernames and passwords) and proxy list. As per ethical hacking researcher of International Institute of Cyber Security, hackers set the required option before performing the attack on the particular web application. This tool keeps on submitting the credential on the target web page using a bot.
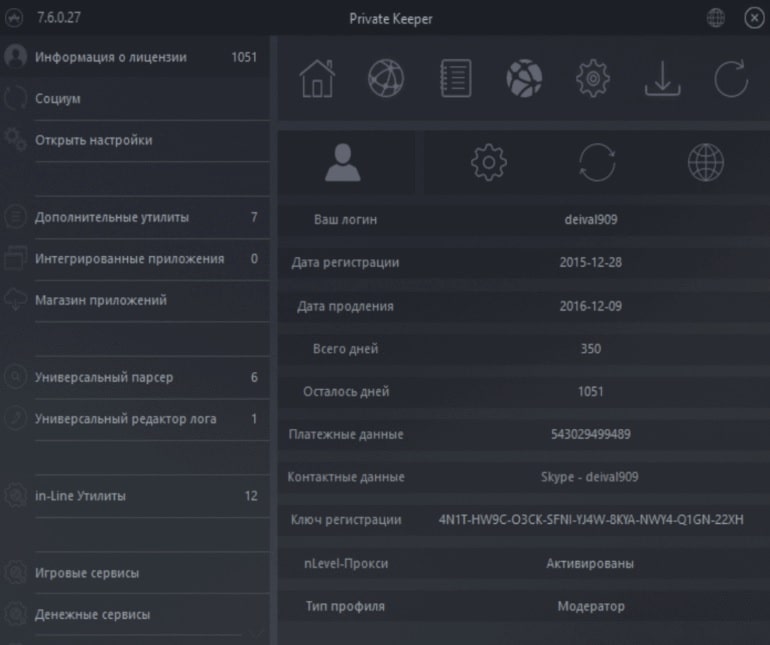
4. Private Keeper
Private keeper is an advanced application tool for people to crack any users’ passwords. This tool performs brute force attacks. It contains combo lists and proxies list, which are collected from other private services. These files are pre loaded in this application.
5. Black Bullet
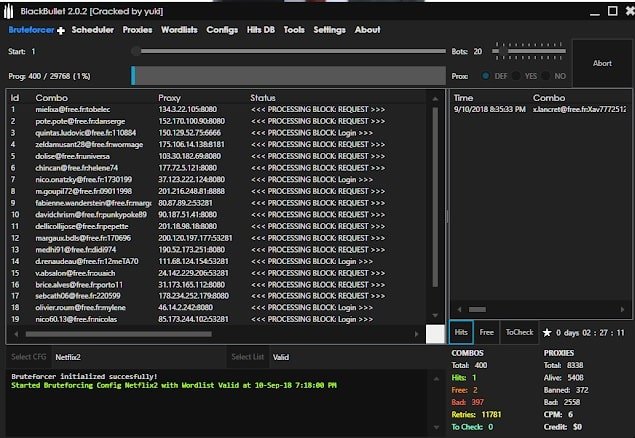
Black Bullet is another tool to break any user’s account. This is a very powerful tool for cracking passwords, it has configurable tools in which we can set our own configs to crack any user’s account. This tool contains large number of wordlists and proxies’ lists using this, it can perform the attack on the target website with multiple users account at a time. In Black Bullet tool contains set cookies option to assign cookie to each bot.
Conclusion
We demonstrated top 5 tools used by cyber criminals. Researcher of always suggest few points to keep your self safe and secure.
- Keep your password strong
- Never every link your banking accounts with social media accounts.
- Always have 2 way authentication on your banking accounts.
- There are ways to keep eye on your accounts.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











