Hackers are always looking for new ways to compromise vulnerable systems. According to network perimeter security specialists, the slightest flaw in a Windows operating system could represent a serious security risk.
Although users have their Windows implementations updated with the latest patches and protected with a functional antivirus, malicious actors will always find a way to sneak into a compromised system, as a recently found Microsoft Store vulnerability demonstrates.
A few hours ago, a network perimeter security researcher publicly disclosed a vulnerability in the Windows 10 application store. If successfully exploited, it could allow an attacker to bypass the security software installed in the operating system and randomly delete any kind of files.
As per the report, the security flaw was specifically found in the executable wsreset.exe, a feature in Microsoft Store design to remove cache and cookies from the platform, aiming to help during problem resolution processes.
This tool runs with Administrator permissions, the network perimeter security experts pointed out, which allows users to easily access all areas in the affected system. When this file is run, it uses all kind of symbolic links to detect directories where cache and cookies are stored.
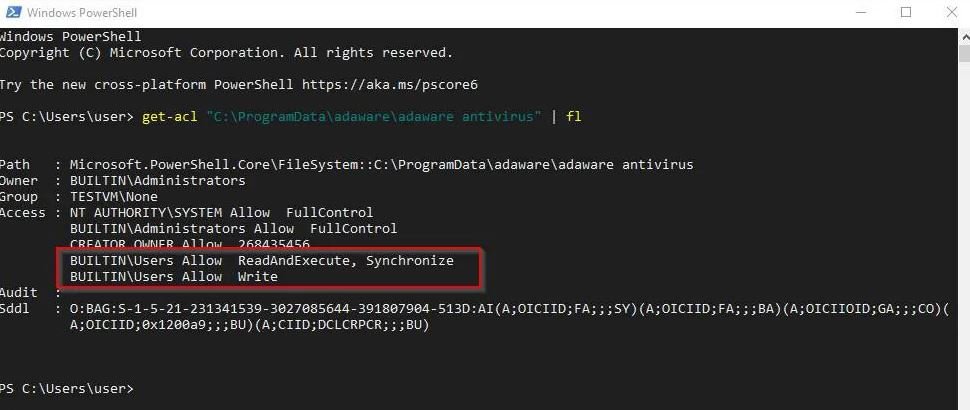
Hackers can modify this symbolic link so that instead of pointing to the Microsoft Store directories, they point to any other directory. In this way, if an attacker directs the program to the directory of an antivirus, executing it will remove the files necessary for the antivirus to work, leaving it disabled and completely unusable.
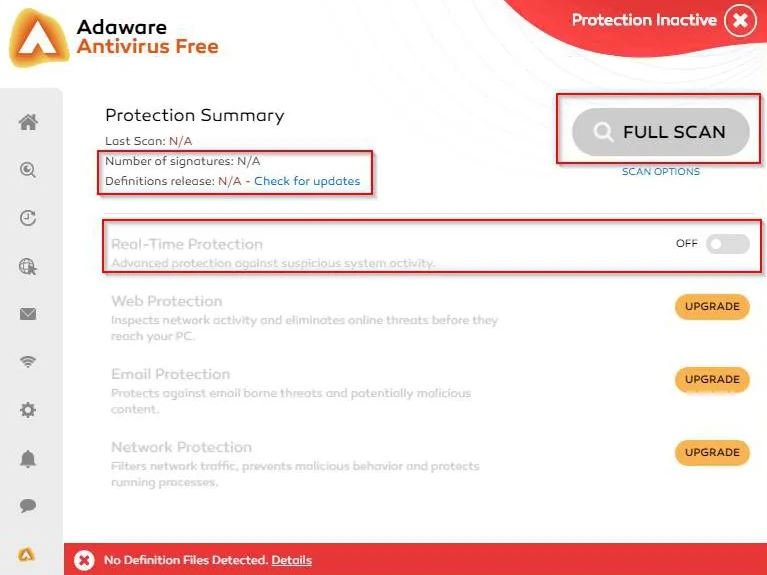
This attack allows malicious actors to bypass the security measures of any PC; in other words, hackers should use it in combination with other attack methods to compromise an affected system. By itself, this attack only could generate random files deletion, the experts mentioned.
Nonetheless, if a hacker uses this Microsoft Store bug to disable an antivirus, as the researcher proved capable, they could carry out other techniques to infect vulnerable PCs with other types of malware, so system administrators must be careful.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











