Specialists from a hacking course report that Data Viper, a kickstarter information security company, suffered a cyberattack that led to the leaking of its database online. Data Viper collects exposed information in more than 8,000 data breach incidents, including records of about 15 billion usernames, passwords, and other data.
In addition to exposing the information online, the person responsible for the attack claims that the database is for sale on dark web. The firm collected data from thousands of security incidents, and could even have obtained information from companies that are unaware that they have been hacked.
Founded by cybersecurity expert Vinny Troia, Data Viper identifies itself as an intelligence platform designed to provide organizations with the largest collection of private information, hacking channels, and exposed databases online. According to hacking course specialists, firms like this sell access to similar collections of information for the purposes of police investigation, fraud prevention, among others.
This is a very competitive market, so Data Viper tries to differentiate itself from its competitors by offering potential clients access to “private and undisclosed incident data”. In previous reports, Troia himself has acknowledged that he often poses as a buyer or seller of stolen data on dark web forums.
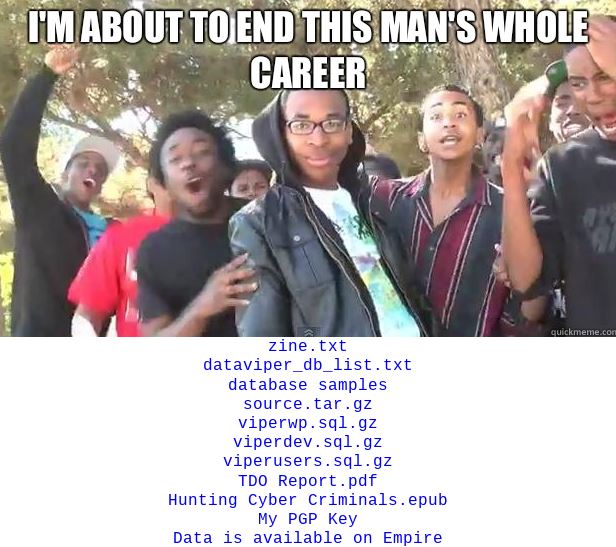
Although this practice is not uncommon, things seem to have gone wrong for this firm. A few days ago, a user posted a link on hacking forums where he described how he hacked Data Viper after having stayed on the company’s networks for months to finally extract hundreds of GB of private data. In addition, the hacker included links to multiple advertisements on the Empire Market hacking forum where hundreds of millions of account details are reported to be sold, stored by Data Viper.
While some of the databases for sale are related to previously reported incidents, other data groups for sale belong to companies that have not reported incidents, or ignore that they have been hacked, mention the hacking course experts.
Through his Twitter account, Troia acknowledged his company’s hack, although he notes that the threat actor only has access to The Data Viper’s development server, so the firm’s storage-related critical systems remain protected. Troia adds that he attributes the attack to an attempted intimidation after he stated that he plans to disclose the identities of the hackers responsible for relevant data breach incidents.
The researcher claims that the hacker group known as “GnosticPlayers” or “Shiny Hunters” has broken into the systems of multiple websites using similar methods, including redirecting the developers of these sites employing credential stuffing attacks to login to their GitHub accounts.
Troia concluded by mentioning that the incident in Data Viper was not the result of a credential stuffing attack, but occurred because one of its developers accidentally exposed the company’s repository access credentials.
Although technically the sale of hacked databases is not considered illegal in the U.S., the Department of Justice (DOJ) has undertaken multiple efforts against these practices. A few months ago, the authorities took control of the domain WeLeakInfo.com, a platform for selling data extracted in cybersecurity incidents; other similar sites have been removed by the DOJ.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











