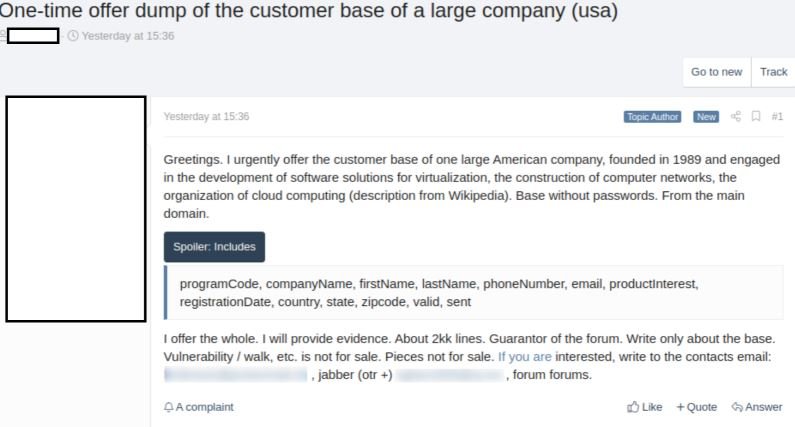
Recently a hacker posted an ad on a hacking forum on dark web to publicize the sale of a database belonging to Citrix. According to specialists in a cyber security course, the threat actor gained access to more than 2 million customer records from the firm.
Headquartered in Florida, USA, Citrix is a multinational technology company that provides server virtualization, networking, software-as-a-service (SaaS) and cloud computing solutions. Citrix’s core product families are Citrix Delivery Center, Citrix Cloud Center (C3), and Citrix Online Services.
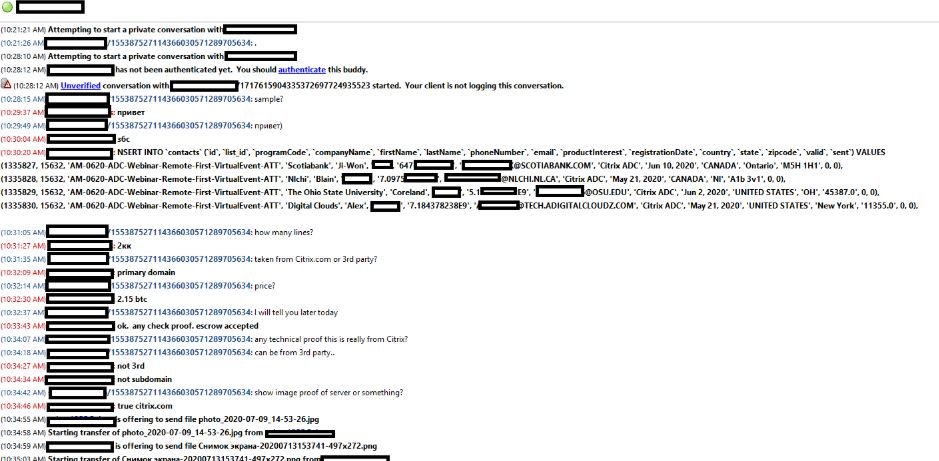
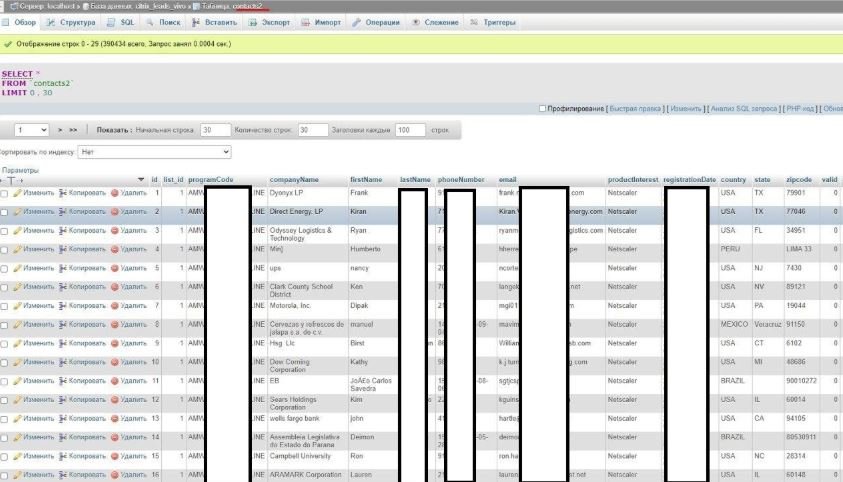
An investigator from security firm Under the Breach managed to contact the hacker by s standing up for a potential buyer. Once the hacker gained the trust, the researcher received a screenshot of the database, confirming its veracity. The method used by cybercriminals to access Citrix networks is still unknown, although experts in the cyber security course believe this may have occurred due to an oversight of staff.
Experts in the cyber security course mention that the database, named citrix_leads_vivo, is on sale in exchange for 2.15 Bitcoin (approximately $20k USD depending on the current exchange rate). In the ad, the hacker notes that this database contains:
- Full names
- Phone numbers
- Company names
- Email addresses
- Registration dates
- Information about country, state or zip code
This is not the first time Citrix has been the victim of a similar incident. A few months ago, the company announced that a hacker group managed to gain access to its internal networks to extract sensitive information and put it up for sale on dark web.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.