Thanks to an operation deployed by the Czech Republic’s cybersecurity unit, the authorities managed to dismantle Atlayo, a kind of social network hosted in Tor. According to the experts of a hacking course, it all began with an investigation related to a Danish drug trafficking group operating on dark web.
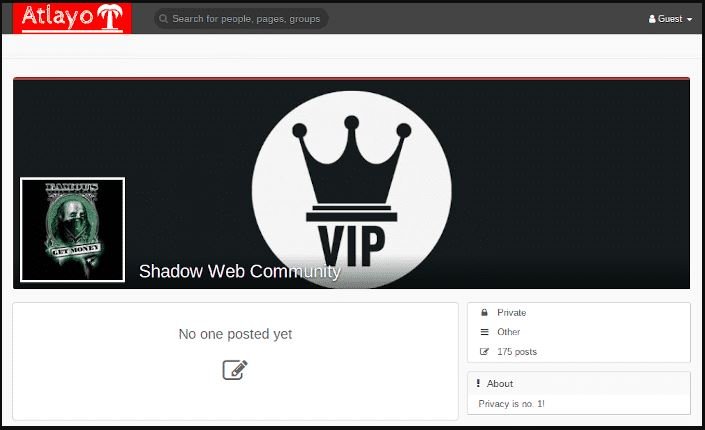
Researchers describe Atlayo as a social networking site on Tor with a special focus on the privacy and freedom of expression of its users. The interface of Atlayo is very similar to that of Facebook, in addition to including similar functions, such as chat, groups, fanpages, among others. The main difference is that users only use “nicknames“, besides that it was frequented by interested in malicious hacking, sale of illegal products, anarchic groupings and even people interested in self-harm.
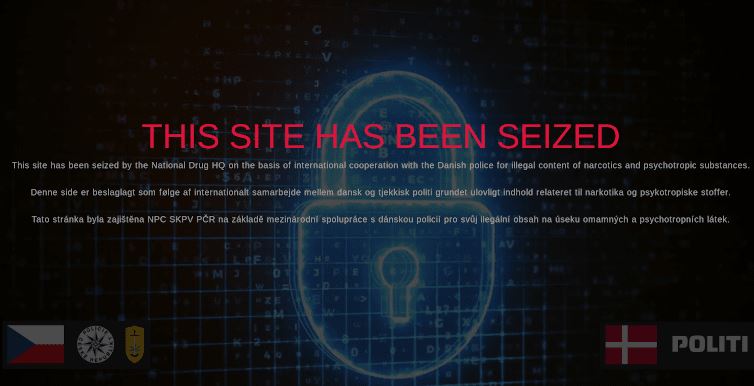
Hacking course specialists mention that a user could access Atlayo using the address onion atlayofke5rqhsma.onion, or traditionally in atlayo.com, in addition to the developers also having their own search engine in xvwhmrw3sgwwmkko.onion; however, all platforms related to Atlayo have ceased to function since the intervention of the authorities.
As can be seen, most atlayo groups focused on the sale of drugs.
Authorities also arrested two men aged 23 and 29, residents of Roskilde, accused of participating in the creation of Atlayo. A third suspect is still on the run, the hacking course specialists mentioned.
Czech authorities collaborated with Copenhagen Police, discovering that Atlayo was staying on the servers of Wedos, one of the largest web hosting services in Europe. Although the police have conducted a thorough investigation, the scope of this network is still unknown: “It is not known how much money has circulated around Atlayo, in addition this network was employed by stakeholders in multiple issues,” said Torben Henriksen, representative of the Copenhagen Police.
This is the first related to the sale of drugs on dark web sites that the police in Denmark and the Czech Republic manage to close, although this is not the first time that the authorities of both countries solve cases and stop the work cybercriminal groups, especially in relation to child sexual exploitation.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











