A team of data security training specialists from Microsoft announced a new initiative to uncover forensic evidence of attack against Linux systems, hoping to detect the presence of rootkits and malware variants that could go unnoticed for the most common security solutions.
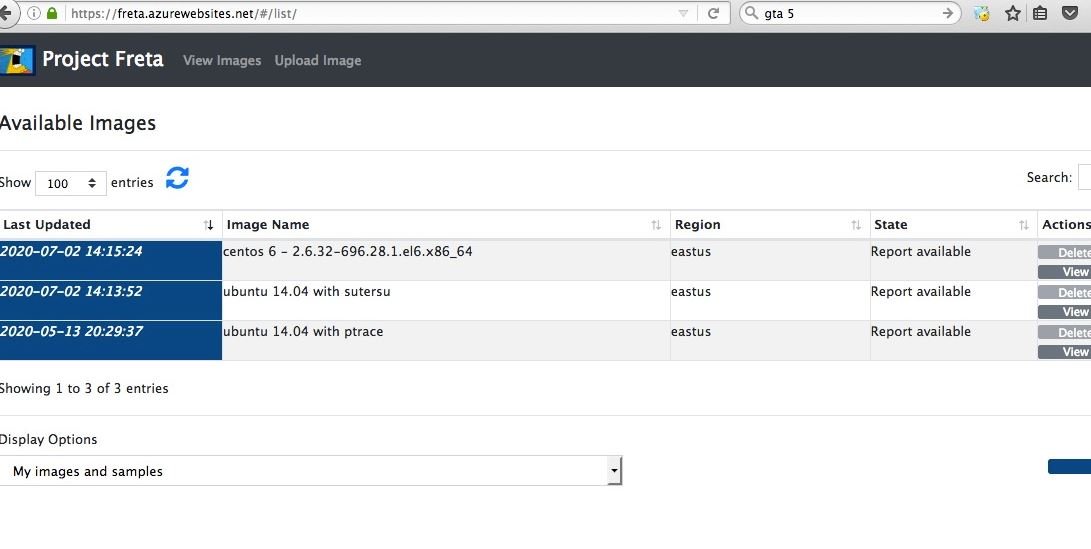
Project Freta is a screen shot based forensic memory mechanism that aims to provide full system volatile memory inspection for malware detection and other security threats. The project is named after Warsaw’s Freta Street, the birthplace of Marie Curie, the famous French-Polish physicist.
“Modern malware is complex, sophisticated and designed with non-discovery as a basic principle,” said Mike Walker, Microsoft’s chief security officer. “The Freta Project intends to automate and democratize forensic analysis of virtual machines to the point where each user and every company can sweep volatile memory for unknown malware at the push of a button, without the need for configuration,” the data security training expert says.
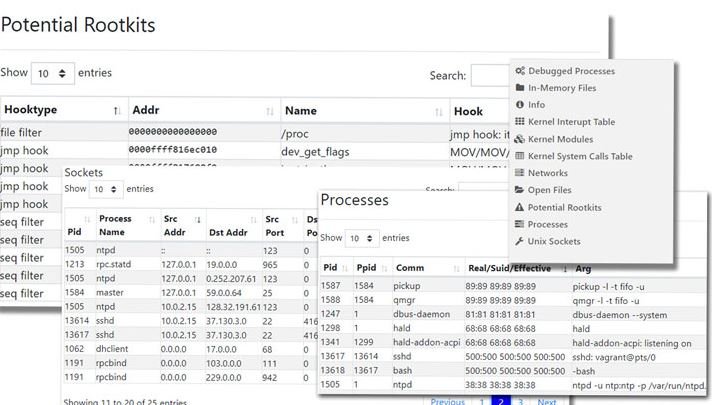
The creators of the project mention that its goal is to deduce the presence of malware from memory to gain an advantage in the fight against hackers, which employ multiple evasion methods with highly sophisticated malware variants.
This detection system works by addressing four different aspects that would make systems immune to any attack:
- Detection of safety sensors prior to installation
- Residence in an area that is out of sight of the sensor
- Detection of sensor operation
- Altering sensor functions to cause sabotage
According to data security training experts, Microsoft focused on Linux due to the need to take logs in the cloud in a platform-independent manner from an encrypted memory image. The company also points to the high complexity of the project, due to the large number of publicly available kernels for Linux.
This initial release version of Project Freta supports more than 4,000 Linux kernel versions with Windows support.
Microsoft is also in the process of adding sensor capability that allows users to migrate volatile virtual machine memory to an isolated environment for further analysis, as well as other tools for artificial intelligence-based decision-making.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











