Database activity monitoring specialists claim that Maze ransomware operators have added Xerox Corporation to their victims list, attack that would have occurred on June 25. Although the company has not commented on this, the information exposed on the attackers’ website appears to confirm that at least one of the computers on the Xerox network was compromised.
Xerox Corporation has nearly 27,000 employees in at least 160 countries and is part of the prestigious Fortune 500, generating revenue of $9 billion USD a year.
Although database activity monitoring experts mention that Xerox was included in the list of companies attacked by Maze since June 24, an alleged member of the hacker group mentioned to the BleepingComputer platform that the information was revealed shortly before the company was infected.
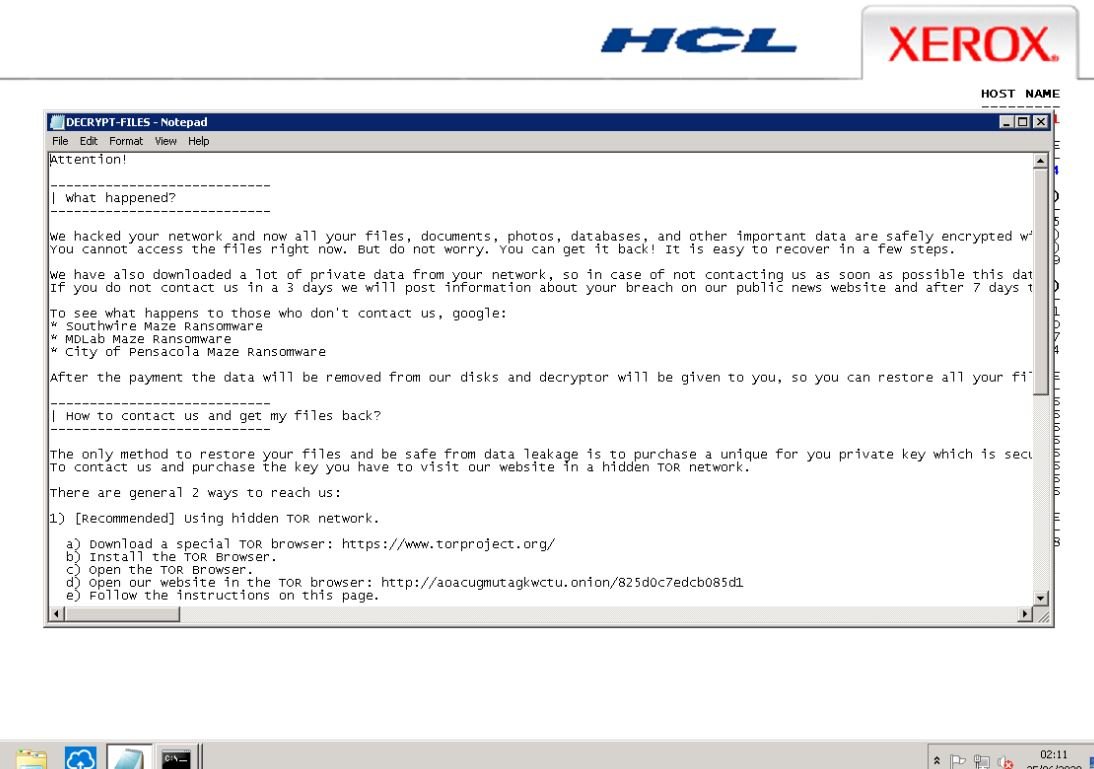
Hackers report that they stole more than 100 GB of Xerox files and claim that they will expose all that information in case Xerox doesn’t pay the ransom. The company is still unclear how the attack happened.
“After receiving the ransom, the data will be deleted from our storage systems and given a decryptor so that they can restore all your files”, mentions the ransom note. Maze released a total of 10 screenshots showing directory lists of June 24 and 25, network shares and the ransom note that is deleted once the decryption routine is complete.
One of the images exposed shows that the hosts in “eu.xerox.net”, managed by Xerox Corporation, were compromised during the incident. Systems in other domains could also be affected, database activity monitoring specialists mention.
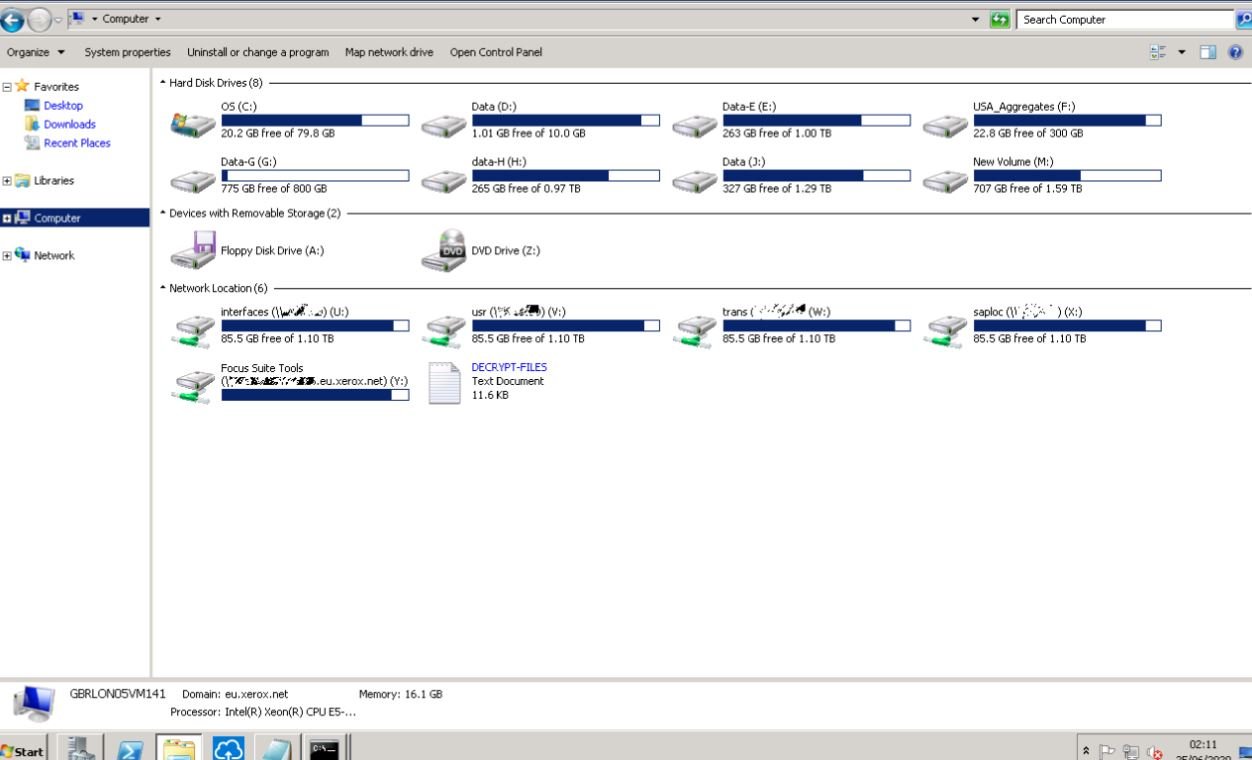
Screenshots show that ransomware operators compromised one of Xerox’s branches in Europe, probably in London. Other images displayed show the ransom note sent by Maze operators, in which hackers threaten to disclose the company’s information.
Maze ransomware operators have been compromising the systems of multiple companies, including large corporations such as LG Electronics, MaxLinear (chip maker), cybersecurity firm Cognizant, among others.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











