According to a report elaborated by database security audit experts, the systems of the University of California, San Francisco (UCSF) were attacked by a hacker group known as Netwalker on June 1. In response to the incident, the IT team disconnected computers from an entire area in order to prevent the spread of malware.
Thanks to an anonymous informant, multiple members of the cybersecurity community had access to negotiations between victims and attackers, conducted on a dark web platform.
While law enforcement agencies, such as the FBI or Europol, strongly recommend not negotiating with hackers, more and more victims of encryption malware are resorting to paying the ransom demanded by the attackers. According to database security audit specialists, the Netwalker hacking group has been linked to at least two other ransomware incidents over the past month; these attacks also targeted leading universities in the U.S.
The dark web site employed by hackers doesn’t seem anything extraordinary, as it even resembles any tech company’s FAQ site. However, a careful glance allows you to appreciate a countdown clock that marks the time victims have to pay the ransom before the situation worsens. Usually the ransomware operator groups threaten to double the ransom figure or permanently delete user information.
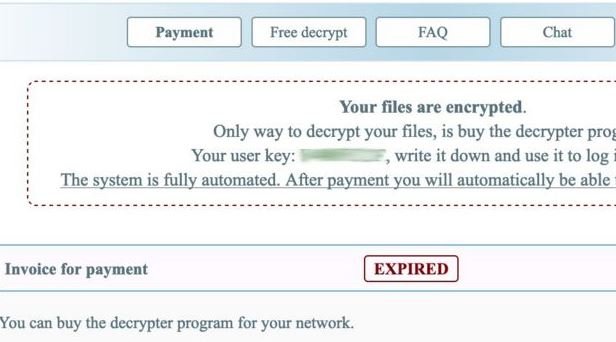
In the case of UCSF, the hackers left a means of contact on the ransom note after the attack. When the victim contacted the attackers, they responded by saying, “Don’t be shy, we can work together on the current incident.”

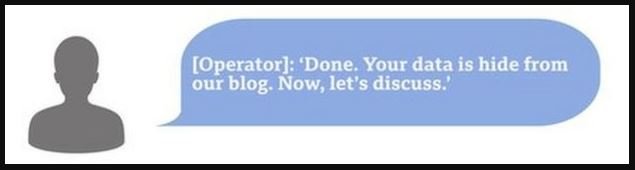
A few hours later, the university requested more time, while asking the criminals to remove any details about this incident from their blog, which Netwalker’s hackers agreed to.
The original amount demanded to UCSF was $3 million, although the university’s negotiator assured hackers that economic havoc stemming from the pandemic prevented paying such a high ransom, so the attackers agreed to negotiate another figure. UCSF is believed to have received advice from external database security audit experts with experience in this type of negotiation.

After a day of negotiations, UCSF pledged to pay a ransom of $1.02 million, although criminals set their best bid at $1.5 million. Eventually, the university offered a payment of just over $1 million, 140 thousand dollars.

According to the International Institute of Cyber Security (IICS), the university transferred 116.4 Bitcoin to the hackers’ online wallet, regaining access to their systems. The incident was also notified to the competent authorities.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











