Sometimes security tools can cause more problems than they solve. According to vulnerability assessment specialists, a remote code execution (RCE) vulnerability was found in Safepay a web browser component developed by BitDefender, which would put thousands of users at risk.
“The incorrect input validation vulnerability in the Safepay browser component of BitDefender Total Security 2020 allows a specially crafted external web page to execute remote commands within the Safepay Utility process,” a company security alert mentions. The flaw, identified as CVE-2020-8102, is found in BitDefender Total Security 2020 versions prior to v24.0.20.116.
On his blog, the vulnerability analysis expert and adblock plus developer Wladimir Palant, detailed how he discovered the vulnerability in the way BitDefender protects users from invalid certificates. As part of the overall system security solution, BitDefender acts as a Man-in-the-Middle (MitM) proxy to inspect secure HTTPS connections.
This behavior is almost a standard used by almost all antivirus vendors and is commonly referred to as Safe Search, Web Protection, Web Access Protection, etc. When presented with an invalid or expired SSL certificate, most browsers pass the option to the user to accept the certificate with a warning, or to leave the website. BitDefender offers a similar browsing experience to its users and provides a customized version of that website.
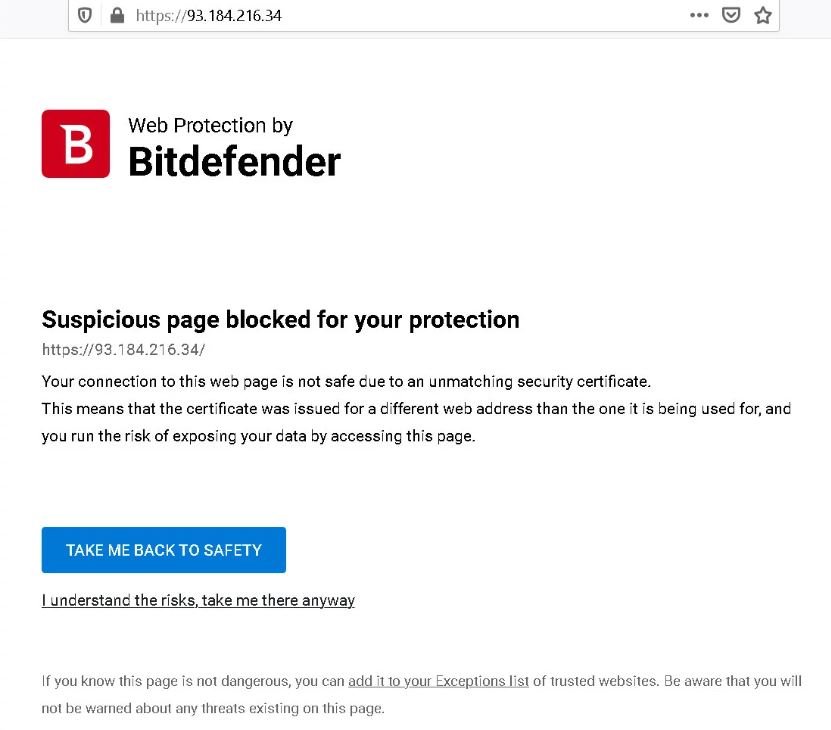
If a user chooses to ignore HSTS warnings and stay on the website at their own risk, that’s usually not a problem. The problem is that the URL itself within the address bar of the web browser remains constant. This tricks the application into sharing security tokens between that (potentially malicious) page and any other website hosted on the same server and running within BitDefender’s Safepay virtual browsing environment.
“The URL in the browser address bar does not change. Regarding the browser, this error page originates from the web server and there is no reason why other web pages on the same server cannot access, regardless of the security tokens they contain, websites can read them. This is a very common problem in the security products of other firms, such as Kaspersky”, mentions the expert in vulnerability analysis.
Palant released a proof-of-concept for the flaw, waiting for the company to release the corresponding updates shortly. For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











