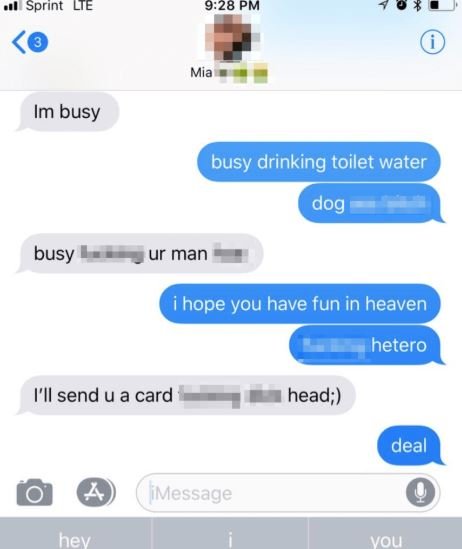
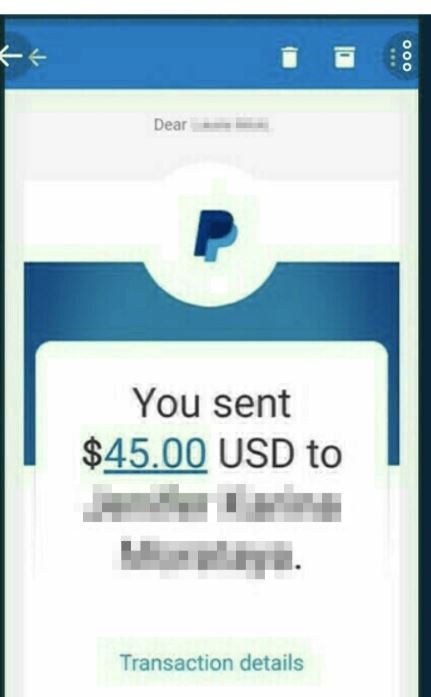
Users of the most intimate online services (such as dating apps, adult sites, among others) are especially interested in protecting their privacy, as a data security issue on these platforms could cause them problems of all kinds, mentioned experts in cloud computing security services. A team of researchers from the firm vpnMentor has revealed the detection of a data breach involving highly sensitive content drawn from multiple dating apps and websites used by people interested in casual encounters.
According to the researchers, all compromised platforms share a common developer, so all files are stored in a single Amazon Web Services (AWS) account. These AWS accounts not only store user information, but also contain all the infrastructure data for the affected applications, including user credentials and unencrypted passwords.
It should be clarified that, while the most popular dating apps (such as Tinder or Happn) are often used by all kinds of users, the platforms involved in this incident are used by people with very specific interests (such as mature women, group sex meetings, among others). The compromised applications are listed below:
- 3somes
- CougarD
- Gay Daddy Bear
- Xpal
- BBW Dating
- Casualx
- SugarD
- Herpes Dating
In total, affected AWS servers store nearly 845 GB of information, equivalent to 20,439 different files, including intimate photos, screenshots, financial movement logs, audio samples, and certain private data, cloud computing security experts mention.
Researchers found multiple details suggesting that these applications were developed by the same company, for example:
- The gaydaddybear.com service is hosted in the same AWS account as ghuntapp.com
- Multiple services’ web design and logo share many similarities
- In their Google Play Store profile, some of these apps mention “Cheng Du New Tech Zone” as developer

There are three AWS buckets that make up this leak, cloud computing security services experts point out. As mentioned above, the stored information includes multiple details such as:
- Images, videos and voice notes sent between users of these apps
- Screenshots of users’ private conversations
- Evidence of financial transactions between users
- Custom content
In addition, the researchers found some personally identifiable details, such as:
- Usernames
- Payment card numbers
- Email addresses
So far it is unknown whether any malicious users managed to access this information before the affected platforms were notified. Access to this information has already been closed.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.