A new variant of online scam has been detected. Cloud security course experts mention that some cybercriminal groups have been targeting website owners, demanding ransoms of between $1,500 USD and $3,000 USD to prevent their websites from being wiped out.
Scammers assure victims that they have gained access to their databases using login credentials obtained in other information leaking incidents, in addition to exploiting some uncorrected vulnerabilities. In case of not paying the ransom, the victim is threatened to post the information stored on their website, in addition to sending emails to all addresses that the hackers find, which would compromise their privacy.
As if that wasn’t enough, scammers also assure victims that they can deindex their websites from the most commonly used search engines using malicious SEO techniques (also known as blackhat SEO), cloud security course experts mention. The ransom must be paid within five days of the threat and through a Bitcoin transaction.
Unlike other similar scam variants, the ransom note of this attack is well worded, so researchers believe the attackers will be English speakers. Below is a snippet of the ransom note.
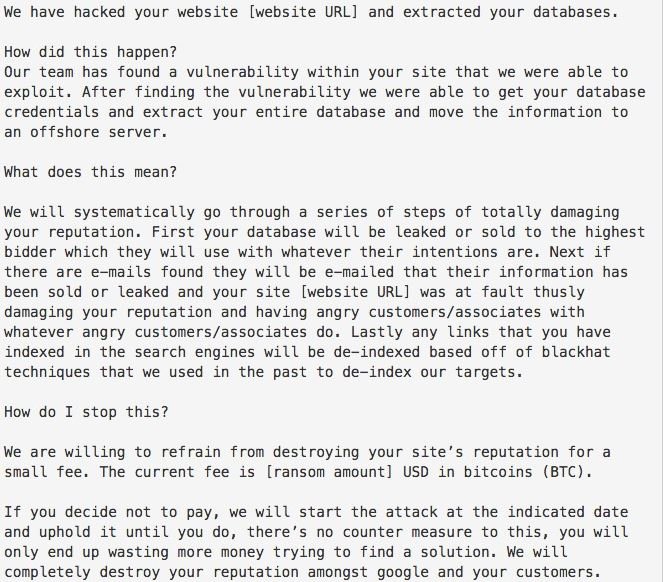
Cloud security course specialists have detected multiple cryptocurrency addresses linked to this campaign, although the amount of money stored in these online wallets is minimal, so experts infer that very few users have fallen into this trap. In addition, content management systems (CMS) have provided guidance to thousands of users, mitigating the risk of this fraud; criminals have also not made contact with potential victims by any other means.
It should be noted that although the campaign has not been expected to succeed by hackers, their activity levels remain high, so potential attack victims will have to remain alert to any signs of anomalous activity.
This campaign is based on lying and threatening website administrators, although we should not forget that a threat of this nature is completely possible in real-world scenarios, since ransomware is one of the main threats to individuals, private firms and government organizations.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











