A few years ago facial recognition looked like technology reserved only for the world’s most advanced intelligence agencies, although this has changed markedly. Data security training experts point out to the growing number of users of PimEyes, a Polish website that uses facial recognition to search for images of a person across the entire web, all its users require is an image of the person they will look for.
How does PimEyes work?
This website’s users can upload photos available on social networks, WhatsApp accounts, news platforms or any available site, then the PimEyes will throw to the user all photos where people similar to the image entered on the website appear. The standard version of PimEyes (free to use) could grant hundreds of similar results, adding a “match scale” from 1 to 5, a MailOnline report notes.
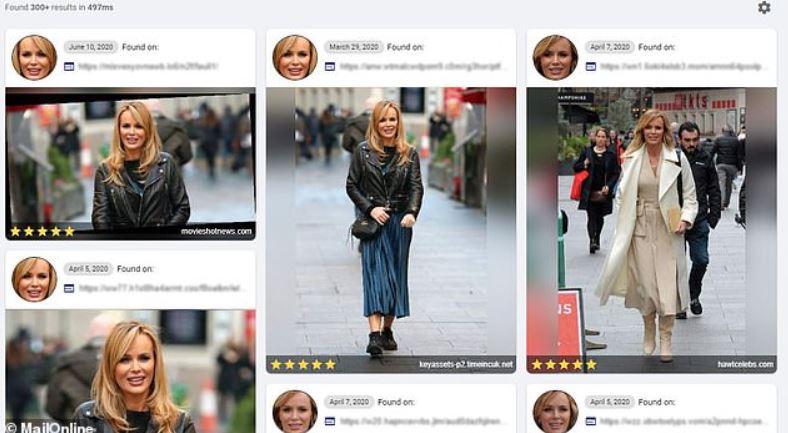
SOURCE: MailOnline
It should be mentioned that this free version also provides information about the site where the similar images were found, although it does not provide an exact URL or any other additional data.
Users can also use a premium version of this service (for about $15USD a day); the paid version provides customers with accurate and detailed information about the provenance of the images. The Premium version also allows users to enable alerts that will notify when a similar photo is posted on any online platform, as data security training experts mentioned. Paid version users will be able to set up to 25 alerts, which would even allow detailed tracking of the target user’s activities.
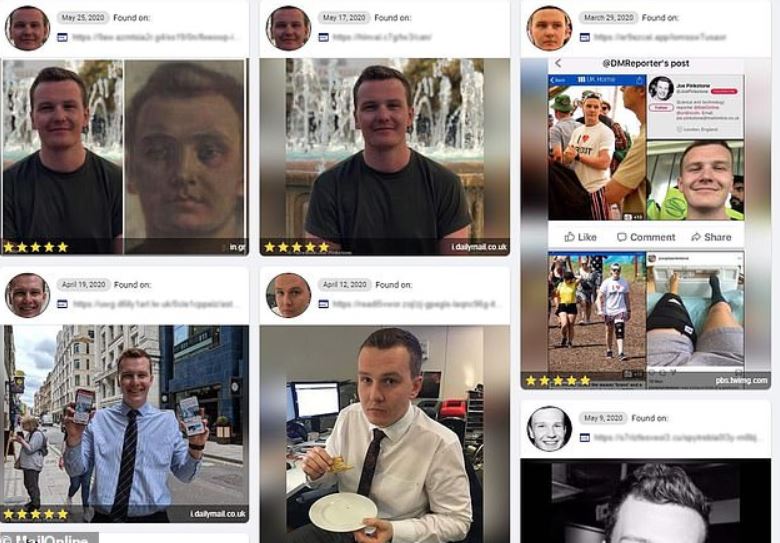
As if that wasn’t enough, PimEyes offers special services for law enforcement agencies, as its developers claim to be able to analyze sites on dark web, an Internet sector plagued by malicious hackers, drug dealers and other cybercrime groups.
One thing that has caught the attention of data security training specialists is the fact that PimEyes is incorporated into the mobile app of a company called Paliscope. This company also offers facial recognition services to some law enforcement agencies, which has allowed multiple suspects to be identified in criminal investigations. According to its website, Paliscope has collaborated with the 4theOne Foundation, an organization dedicated to finding child victims of trafficking.
Privacy issues
While this tool is novel and highly effective, its use is not without criticism. Multiple members of the cybersecurity community consider PimEyes to significantly affect the online privacy experience of everyone who has ever uploaded photos of them to the Internet.
The main problem is that there are no security controls in PimEyes to prevent a user from uploading to the platform an image of anyone, whether it’s a celebrity, a politician, a friend, a romantic partner and so on. Using this tool is very simple, so no one would have greater inconveniences to find confidential details of a specific person with a simple search.
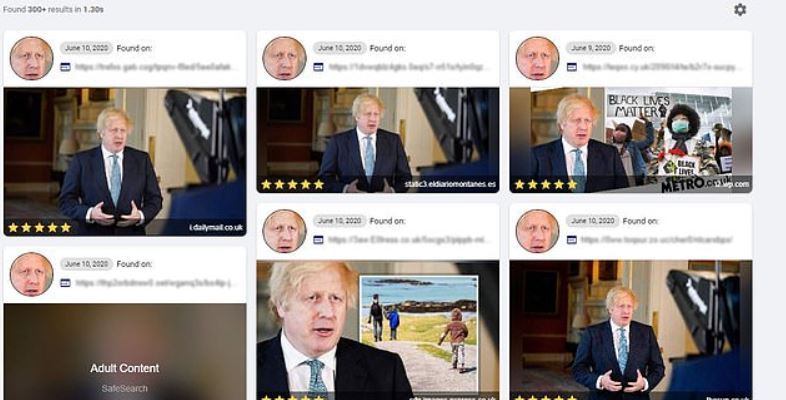
This is not the first time an online tool is pointed out due to its advanced facial recognition capabilities. In January 2020, specialists said that the Yandex search engine (also known as the ‘Russian Google’) provided a facial recognition system lacking any regulation, which would have been used to breach into the privacy of millions of people. Other tools have operated similarly, although they were discontinued or their use is no longer allowed.
In this regard, Brian Higgins, data security training specialist at Comparitech, mentions that the site presents obvious and serious security drawbacks: “I seriously doubt that the developers are inexperienced enough to believe that their tool is only used with good intentions,” the expert says.
Higgins adds that the existence of such platforms will continue to pose a security risk to Internet users: “Even if developers of PimEyes were forced to shut down their operations, dozens more similar tools will eventually appear. The only real protection, and that is in the hands of each person, is that we start taking our online privacy seriously so that the Internet knows as little information about us as possible.”
Internet user privacy is a right, and companies, public organizations, and law enforcement agencies should make greater efforts to improve this experience rather than allowing tools to violate user privacy. For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










