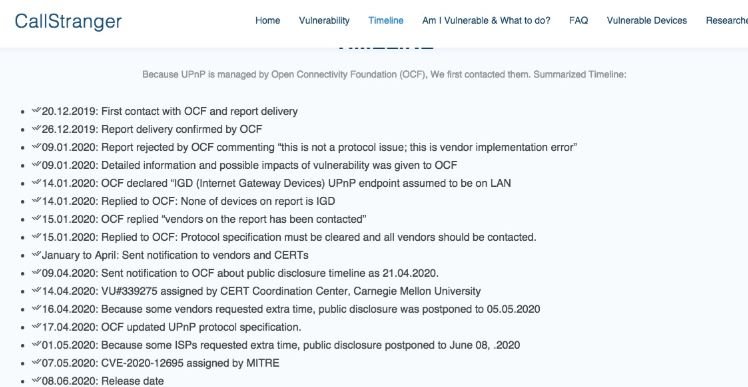
The massive use of Internet of Things (IoT) devices has created new security issues. A team of network security course specialists has revealed a critical vulnerability in the core protocol with which millions of IoT devices operate.
The vulnerability was named “CallStranger”, and its exploitation would allow threat actors to hijack Internet-connected devices for use them in denial of service (DDoS) attacks. In addition, hackers can exploit this flaw in other attacks involving the omission of some security solutions and accessing the internal networks of a target organization for malicious purposes.
Network and computer security experts who discovered the flaw published a website to provide more technical details about CallStranger. On this page, researchers claim that this flaw affects Universal Plug And Play (UPnP), a set of protocols used by the vast majority of smart devices.
UPnP allows IoT devices to identify with each other on-premises networks and after establishing connections for data exchange, connections, and even working between connections in a very simple way.
According to network security course specialists, UPnP protocols have been around for almost twenty years, but since 2016 their development has been operated by the Open Connectivity Foundation (OCF) in an effort to standardize their operation for all existing IoT devices.
Due to its extensive use, a security flaw in this technology could have disastrous consequences. A few months ago, a researcher revealed a vulnerability that would have allowed threat actors to send TCP packets to a remote device with a malformed return header value in the UPnP SUBSCRIBE function.
Threat actors could have abused these poorly formed headers to take control of any device with an Internet connection and UPnP support, such as security cameras, printers, routers, and more.
In this attack, threat actors target the Internet interface of vulnerable devices, although malicious code runs in the UPnP function, which usually runs only on internal ports. The attack could be used to bypass security solutions (such as firewall or antivirus) and perform full scans of the target network.
OFC was notified a few months ago, so UPnP protocols have already been updated. Although fixes were released on April 17, some manufacturers might take time to upgrade their systems, so IoT device administrators in enterprise environments are encouraged to check the status of their updates.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











