Social distancing measures will remain in place in most of the world for the coming months, so employees and managers from public and private organizations will continue to rely on remote work tools (such as Zoom, Slack, among others) as information security awareness experts mention.
One of the most popular tools during isolation has been Private Branch Exchange (PBX), a legacy technology that allows sending voice messages directly to users’ mailboxes. When someone cannot answer a phone call, a recording will be automatically sent to their inbox.
This is a very useful feature for members of hundreds of companies, although information security awareness experts claim that threat actors have found a way to leverage this platform to deploy phishing attacks against specific users. The report was prepared by specialists from the firm IRONSCALES.
The attack is based on the use of a technique known as voice phishing (or vishing), which requires sending emails with specific subject lines to attacked users by sending messages allegedly coming from PBX deployments. The following image shows an example of a custom email that includes the company or user’s name, so there is no clear indication that it is a phishing email.
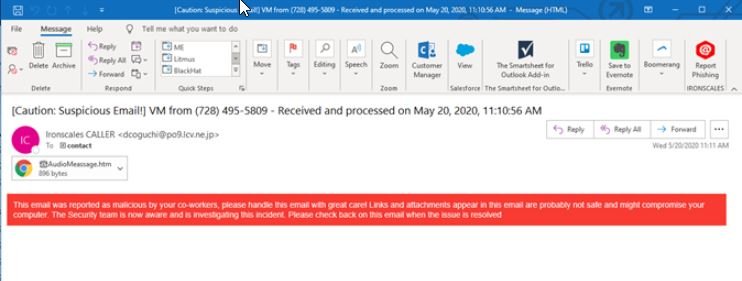
Although the content of these messages is scarce, information security awareness experts believe that victims fall into the trap due to the specificity of the email title: “This level of sophistication explains why these messages are able to bypass any email security filter, because in reality these systems are not able to detect phishing messages that do not include malicious payloads”.
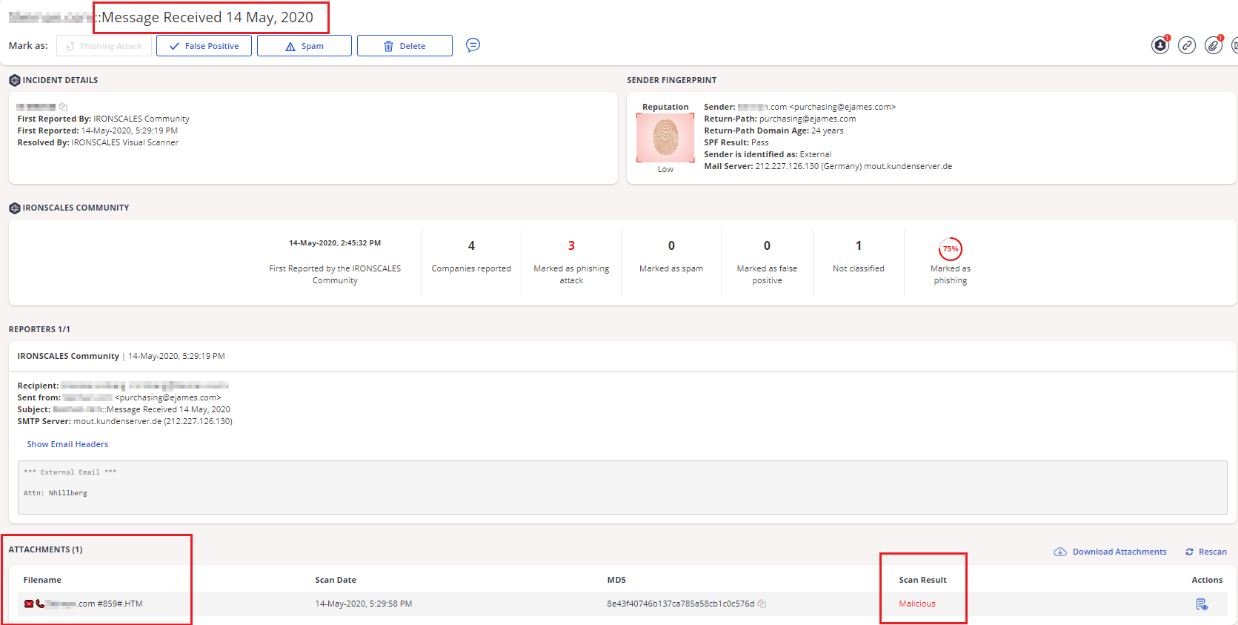

Virtually any company that uses this tool is susceptible to attacks, so the International Institute of Cyber Security (IICS) recommends users implement some steps to mitigate the risk of vishing:
- Notify employees about this risk and how an attack is carried out. An employee with cybersecurity skills can detect an attack before it’s too late
- Implement technological developments capable of detecting such sophisticated phishing scams; while the use of these technologies involves considerable investment, in the long term organizations will be able to realize that these costs are worthwhile
More than 100,000 voicemails have been the target of vishing attacks, so it should be considered a risk for each company that depends on the use of these tools.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











