Security testing course specialists from Cisco revealed the presence of at least four critical vulnerabilities in the router equipment included in IOS XE software and Cisco IOS. According to the report, the flaws were corrected in the most recent update, released on June 3.
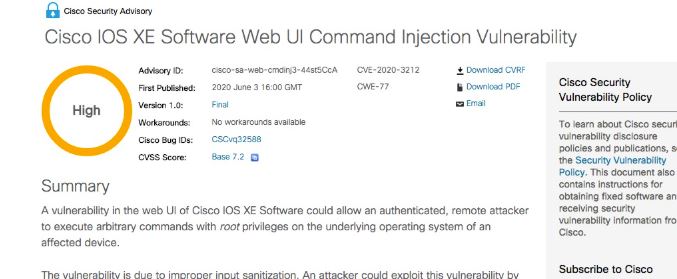
One of the reported vulnerabilities received a score of 9.8/10 on the Common Vulnerability Scoring System (CVSS), and is related to authorization controls for the Cisco IOS XE Software application hosting infrastructure. This condition allows unauthenticated remote hackers to execute API commands without the required authentication. The flaw was tracked as CVE-2020-3227.
IOx software mishandle authorization token requests, allowing threat actors to exploit the vulnerability by using a specially designed API call to request the token and execute IOx API commands on the device.
The second flaw, tracked as CVE-2020-3205, is a bug that would allow command injection into Cisco deployment between Cisco IOS software virtual machines for Cisco Industrial Integrated Services Routers (ISRs) 809 and 829 and Connected Cisco 1000 Series Network Routers (CGR1000), security testing course experts report.
The software does not properly validate signaling packets targeting the Virtual Device Server (VDS), which could allow an attacker to send malicious packets to an affected device, gain control of VDS, and then fully compromise the system, including the IOS VM and guest VM. VDS handles access to devices shared by IOS and the guest operating system, such as flash memory, USB ports, and console.
The third notice refers to CVE-2020-3198 and CVE-2020-3258 errors, related to remote code execution vulnerabilities on the same Cisco industrial routers. The CVE-2020-3198 flaw allows an unauthenticated remote threat actor to execute arbitrary code on the affected systems, causing massive failures.
Security testing course experts mention that a hacker could exploit the vulnerability by sending malicious UDP packets over IPv4 or IPv6 to an affected device. The risk of exploitation can be mitigated by implementing an access control list to restrict incoming traffic to UDP port 9700.
Finally, CVE-2020-3258 would allow local malicious hackers to execute arbitrary code on the affected device. To exploit this vulnerability, threat actors must have level 15 privilege user credentials, the highest on Cisco systems. Exploitation of this flaw is unlikely, so it was assigned a score of 5.7/10.
According to the International Institute of Cyber Security (IICS), updates are already available, so you only have to verify that your installation is successful.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











