Thousands of public organizations and private companies keep using remote work to comply with isolation measures due to coronavirus combat, so demand for cloud services has been increasing during the last months. Network perimeter security specialists say that even though social distancing is necessary, this behavior has also favored cybercriminals, who now have greater resources to deploy malicious campaigns.
A report from cybersecurity firm Abnormal Security describes a recently detected phishing campaign in which threat actors pose as Amazon staff members to extract access credentials to Amazon Web Services (AWS).
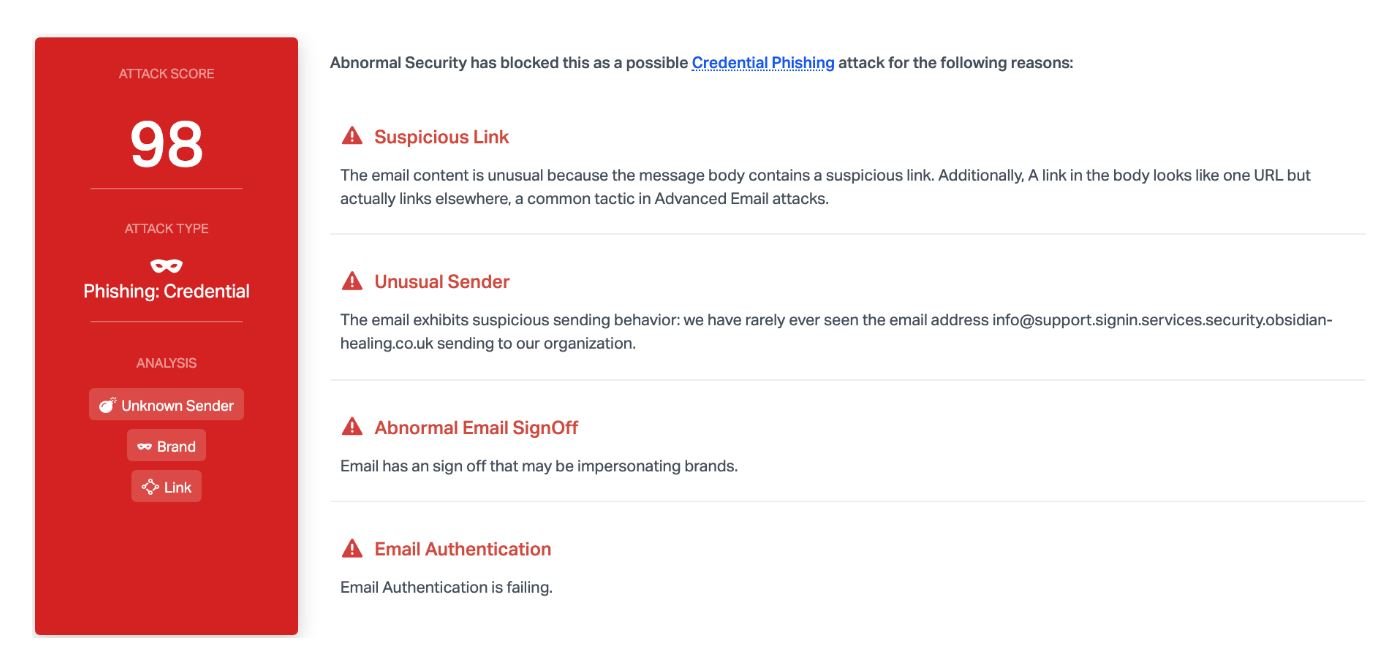
This attack begins with an email, allegedly sent by AWS support, in a format that is actually identical to that of the company’s legitimate notifications. However, when users carefully analyze the content of the message, they may see that the link in the text is different from the Amazon address, although many users may not notice this, the network perimeter security specialists mentioned.
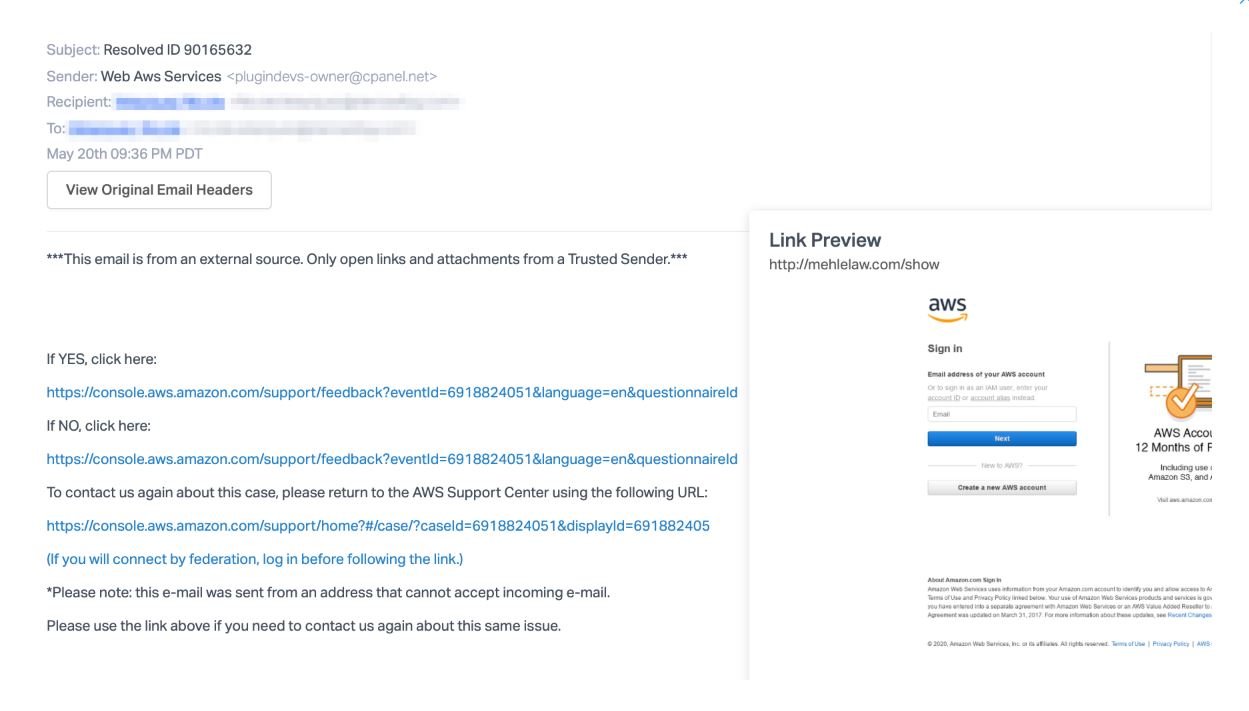
The link contained in the message redirects users to a website identical to AWS login (threat actors even took their time to embed images extracted from the company’s official website). As in any other phishing campaign, this fake login will only work to collect the credentials of unsuspecting users.
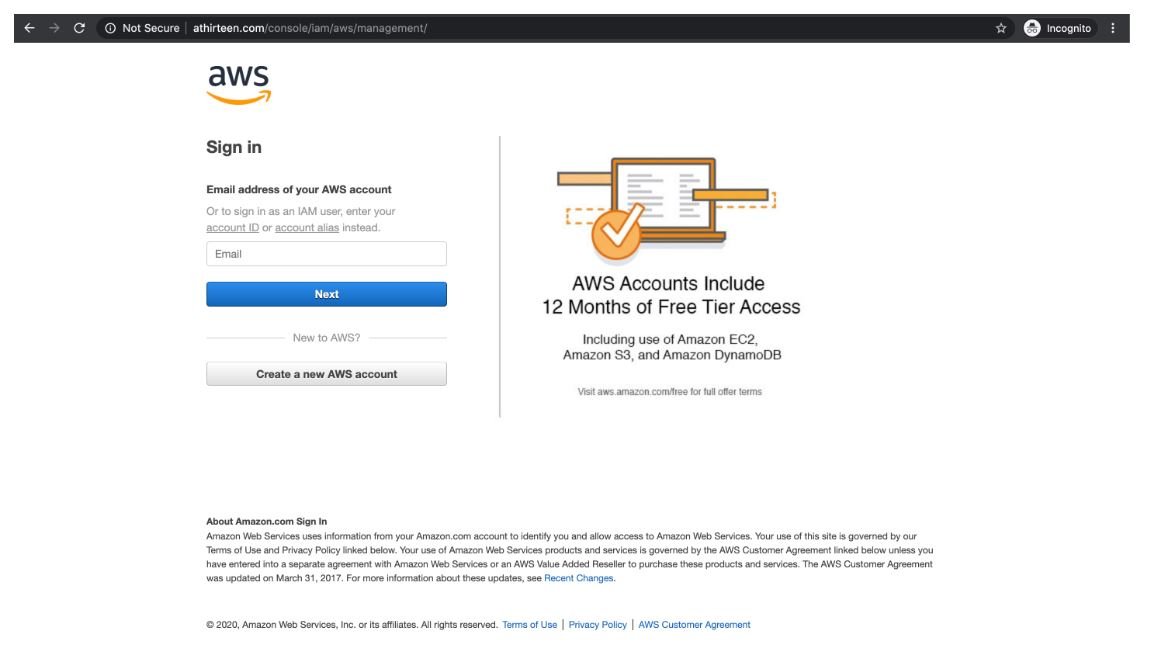
Abnormal Security’s network perimeter security specialists claim to have detected multiple versions of this attack, using different sender addresses and a variety of payloads, although all attacks were aimed at stealing AWS login credentials. It should be noted that all emails related to this campaign come from the same IP address, hosted on a French VPN.
Cybersecurity specialist Balaji Parimi points out that this information could be used by threat actors to easily access companies’ most valuable resources, such as intellectual property, human resources information, financial details, growth or expansion plans, among others: “Companies use cloud storage to protect valuable resources. The loss of access credentials would be a severe problem.”
Social distancing measures remain in place in hundreds of cities, and will remain in place over the next few months, so the International Institute of Cyber Security (IICS) anticipates that phishing campaigns targeting remote employees will remain a serious problem in the medium term.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











