One of the main features of the ransomware is its ability to evolve and improve its capabilities to infect attacked systems. Specialists in a cyber security course reported the detection of a new encryption attack method that takes defense evasion to a never-before-seen level, deploying a VM deployment to avoid detection.
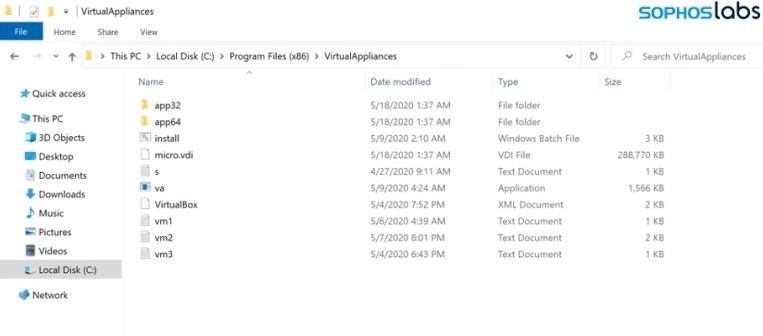
The ransomware in question is known as Ragnar Locker, which was detected in a recent attack. According to the report, the encryption malware was deployed to an Oracle VirtualBox virtual machine running Windows XP operating system. The attack load was a 122 MG installer and a 280MB virtual image, all in order to hide an executable of just 49kb.
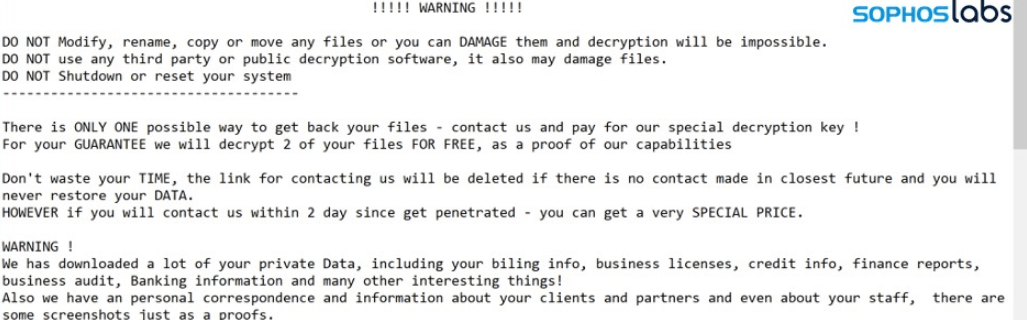
Cyber security course specialists suggest that Ragnar Locker operators extract and publish sensitive data from target networks before launching the ransomware attack as a form of pressure for victims. A few weeks ago, a Ragnar Locker infection was detected in the Energias de Portugal (EDP) networks, the country’s largest energy company. In addition to infecting the systems, hackers stole about 10 TB of sensitive information, demanding a payment of 1,500 Bitcoin (more than $10 million according to the current exchange rate). Apparently, the energy company decided not to pay the ransom and reset its systems on its own.
The operators of this ransomware have also been linked to attacks that employ exploits against remote desktop connections (such as the RDP protocol, Windows) to gain persistence on specific networks. Once they gain administrator-level access, hackers use native management tools on the Windows system to navigate across the network and reach other clients and servers.
In the attack analyzed by Sophos cyber security course specialists, Ragnar Locker operators used a GPO task to run Microsoft Installer (msiexec.exe), passing parameters to silently download and install a specially designed and unsigned 122 MB MSI package from a remote web server. The main contents of the MSI package were:
- A functional installation of an old Oracle VirtualBox hypervisor; actually, Sun xVM VirtualBox version 3.0.4
- A virtual disk image (VDI) file called micro.vdi, an image of a simplified version of the Windows XP SP3 operating system, called MicroXP v0.82. This image includes the 49 kB ransomware executable
In their report, experts mention that its features make this ransomware variant a considerable risk to the networks of the most important organizations around the world. For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











