Specialists from a hacking course reported the finding of a security vulnerability in Signal, a messaging platform with a focus on user privacy. According to Tenable researchers, exploiting this flaw could allow tracking user activity by simply calling their number in the app. Signal is very popular with journalists, activists and even political refugees, so exploitation could have disastrous consequences.
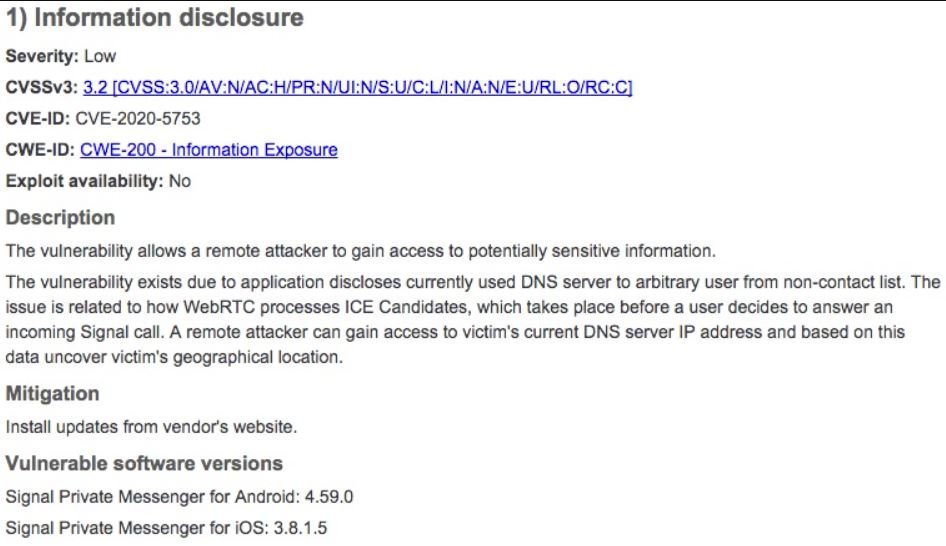
David Wells, researcher in charge of the finding, points out that there are two fundamental aspects to this vulnerability. The first is that if two Signal users have each other as contacts, they may be able to determine their mutual location and IP address of the other with just one call, even if the other user does not answer the call.
On the other hand, hacking course experts mention that this information exposure could be triggered even if the target user receives a call from Signal from an unknown number, in addition, the attackers do not even rely on the victim answering the call to determine an approximate location.
“It’s a little strange that someone can get your location with just one phone call,” Wells says. “You could use a prepaid phone and call the target user; everything happens so fast that there is only one missed call log left of an unknown number. This is more than enough for the attacker to verify which DNS server the phone connects to and force it to respond; Knowing which DNS server you are interacting with, it is possible to determine a general location,” adds the hacking course expert.
It should be noted that this method is unreliable; during his investigation, Wells called a Signal user based in Pennsylvania, although the associated DNS server dropped a location in Toronto, hundreds of miles away.
Apparently the problem lies inside the application, and unlike other variants of attacking users of messaging services (such as phishing), there is nothing users can do to keep themselves secure, the International Institute of Cyber Security (IICS) reports.
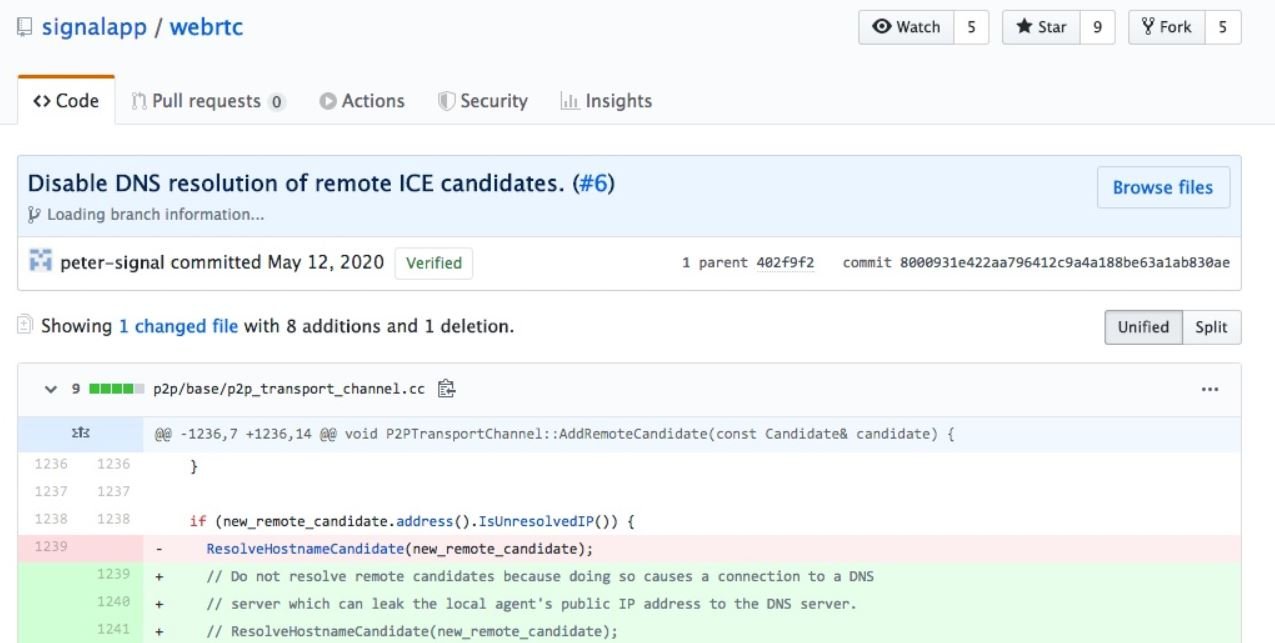
Signal has not stated anything about it, although a source close to the company mentioned that an update patch will soon be available on application platforms. While Wells considers this not a critical flaw, the fact that applications with access to this kind of details leave so many loose ends is undesirable: “I wouldn’t say this is a hacking attack, because we’re not breaking encryption in Signal or anything like that, although the firm needs to fix this issue,” Wells concludes.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










