Collecting information from technology users has become commonplace, cloud computing security specialists say. Although the main use of this practice is the preparation of marketing campaigns, experts mention that threat actors also resort to gathering information to generate more sophisticated attack vectors and obtain the resources needed to attack victims.
One of the most common methods is sending bulk messages through the most popular messaging apps. For this, threat actors create fake offers of fashionable or interesting products for a community, video game enthusiasts, for example. In this campaign, hackers target Fortnite players, sending messages in which they allegedly give away V-Bucks, the virtual currency used in this video game.
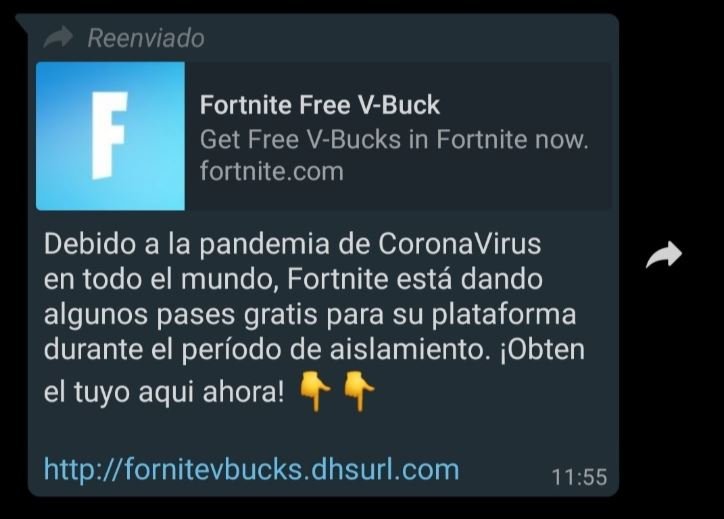
“Fortnite is giving away some passes for your platform during this isolation period. Get yours now,” mentions the message sent to random users. The message contains a link that directs victims to a website with a form and hackers ask the victims to complete it to get the alleged gift, cloud computing security experts mention.
When the victim completes the form, the page displays a window that mentions that the responses are being processed, in addition to asking the user to share the link with ten of their contacts. Needless to say, the victim receives no gift, and their responses are sent to a location controlled by the hackers.
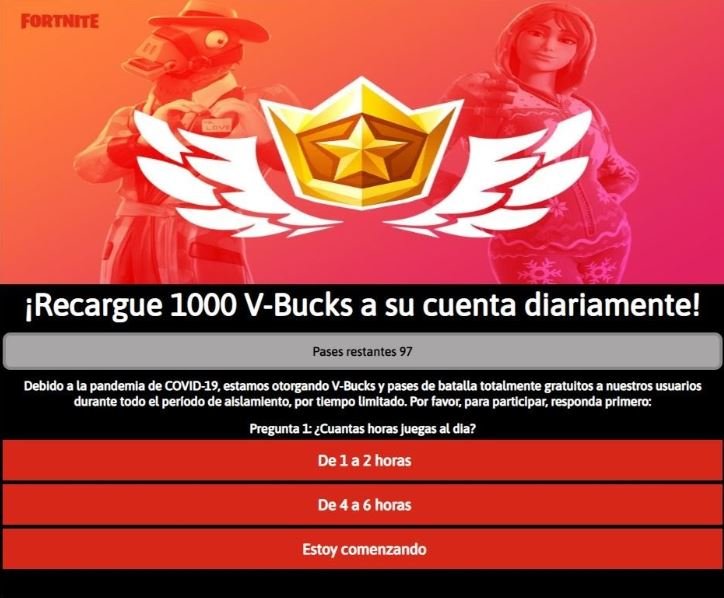
Many users rely on this scam, as they are not asked for personal data. However, by now the hackers have already obtained the IP address of the victim without having to explicitly request this information.
This website is actually a blog created in Google’s Blogger. The drivers of this website activated a series of ‘cookies’, which are small files in browsers with session information or browsing habits that can be integrated into Google Analytics, mentioned by cloud computing security experts.
These techniques are common in the world of marketing and there are many tools to carry them out. However, the International Institute for Cyber Security (IICS) considers that in this case the problem is that a false domain is used in conjunction with an illegitimate announcement. In addition, it is clear that hackers use these methods for malicious purposes, exposing victims to subsequent attack campaigns.
For security, users are advised to ignore this kind of phishing messages, which have recently proliferated due to confinement.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











