A curious incident has caught the attention of the cybersecurity community. According to network penetration testing specialists, someone hijacked a forgotten subdomain of the company PricewaterhouseCoopers, using it to host ads from websites and pornographic content apps, demonstrating why companies should not unprotect their corporate DNS registers.
Vitali Fedulov, a developer and security researcher, said he found twice this week the subdomain pwc.com, which hosts a series of adult-targeted ads. These ads redirect users to chat websites, blogs and other platforms only suitable for adults. It is also possible to access these sites via the web browser.
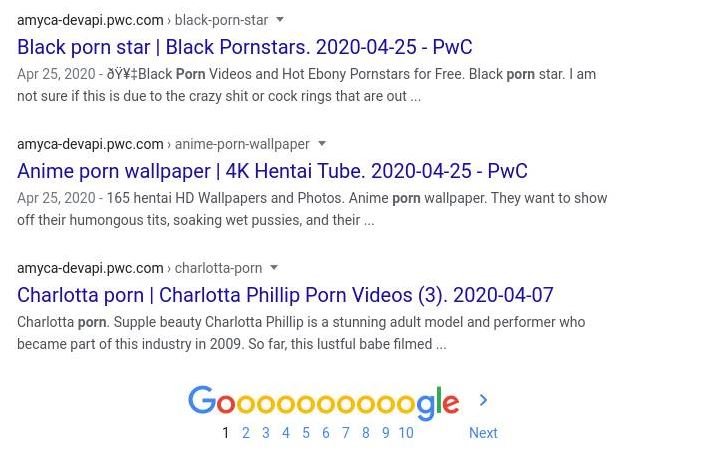
After the report, the subdomain amyca-devapi.pwc.com was disconnected, so it is no longer resolved to an IP address, although your Google entries remain so far. Fedulov, who has been in charge of the development of an image search engine, considers this to be too large an oversight to occur twice, network penetration testing experts mention.
“PricewaterhouseCoopers provides security services, even for government organizations, I think it’s time to publicly disclose this incident,” Fedulov said. “In addition, the company seems un interested in supporting the cybersecurity community with vulnerability reward programs, as other large companies do,” the researcher says.
So far, the company has not officially spoken out.
The subdomain pointed to amyca-dev-node.azurewebsites.net, a custom Azure subdomain created to host some kind of cloud API development system. At some point, the company let its amyca-dev-node subdomain expire, allowing a threat actor to register it as their own. When users and bots of search engines visited amyca-devapi.pwc.com, they were directed to the amyca-dev-node.azurewebsites.net, which was already controlled by hackers and already contained these inappropriate ads, as mentioned by network penetration testing experts.
It should be noted that in this case there was NO intrusion into the PwC networks itself, as it is only an oversight with a forgotten DNS from which some criminal tried to take advantage. Still, this should not be overlooked, since the reputation of a large company is at risk.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the Website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










