Specialists in IT security risk assessment have revealed a new technique with which it is possible to exploit a vulnerability to disable almost any antivirus solution on Windows, macOS and Linux operating systems. While some antivirus tool vendors recently implemented substantial improvements, the flaw has proven to be highly functional against multiple deployments.
Antivirus tools are one of the main methods of anti malware protection, although there are multiple methods to bypass this barrier and compromise a system. Unlike other attack variants, the method presented by this group of specialists is especially stealthy and can help a threat actor to abuse a computer system with ease.

RACK911 Labs IT security risk assessment experts mention that when an unknown file is saved to disk, the antivirus installed by the user performs a “real-time scan”, which could take a few seconds or even minutes, depending on the antivirus tool. If a file is identified as suspicious, it is quarantined or deleted. Because antivirus tools run with high privileges on the system, threat actors can take advantage of this to exploit some known security flaws.
According to specialists, there is a brief window of time between the start of the scan and the suspicious file cleanup operation that could be used by a threat actor to deploy a race condition using a directory function (in the case of a Windows OS) or a symbolic link (on macOS and Linux systems). This action could exploit privileged file operations to disable antivirus, or interfere with the operation of the operating system to disable the security tool.
After performing some tests on Windows, macOS and Linux, IT security risk assessment experts proved able to disable and delete some files important for the proper functioning of the antivirus, even removing some important files for the operating system. Below is a list of the files analyzed by this team, specifying which of them turned out to be vulnerable to this attack variant. Affected antivirus developers have been notified, although it is unknown which have already released the necessary fixes.
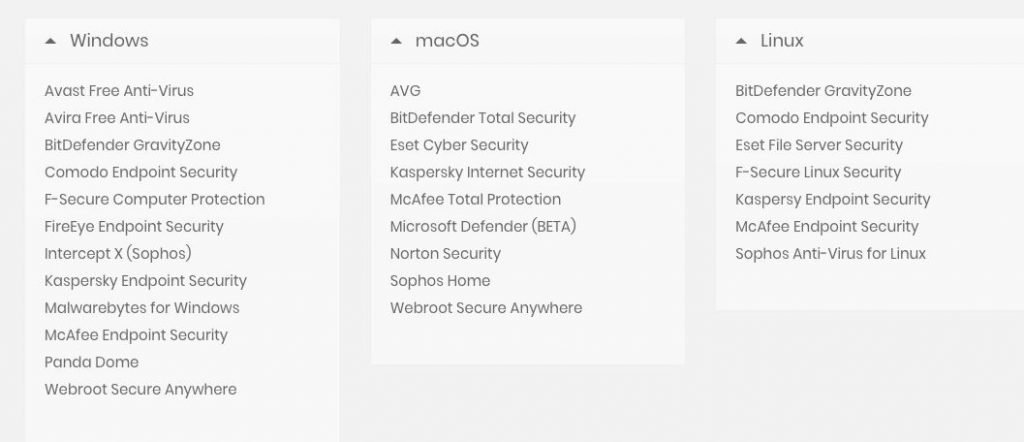
According to the International Institute of Cyber Security (IICS), it is highly possible that these failures are also present in the antivirus of other companies. Specialists published their proof of concept, so developers of these tools will be able to conduct some security tests to determine if their products are exposed to this attack variant.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










