Forced social distancing has unusually driven the use of remote communication platforms such as Skype, Hangouts, WhatsApp and mainly Zoom, which has shown a prominent growth in terms of its number of users a couple of months ago, mention specialists of a cyber security course. Academic institutions, government offices and private companies have resorted to using Zoom to maintain their primary activities relatively normal.
Zoom’s rise in popularity has not gone unnoticed by the cybersecurity community, which has begun to point to some questionable practices that previously went unnoticed. One of the obvious errors is a very weak privacy policy, which allows for unnecessary and invasive data collection for users. In addition, an attack variant known as “zoombombing” was recently revealed, which would allow a threat actor to suddenly block a meeting.
These are not the only issues that have been identified in Zoom. A group of researchers from the cyber security course has published a report detailing how Zoom has become an ideal platform for online scammers, who have managed to extract login credentials from more than 350 verified accounts. This information is available on some hacker forums hosted on dark web.
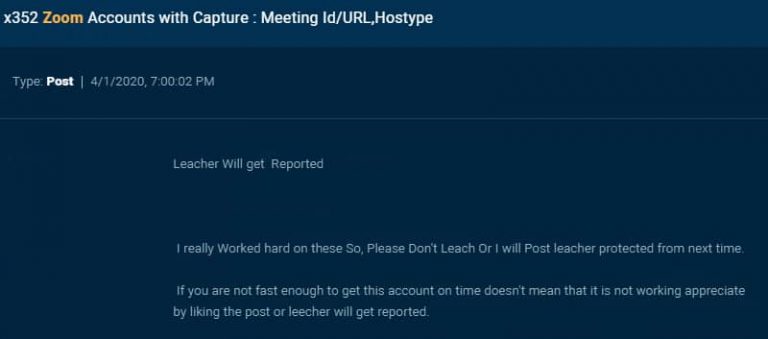
The file also contains sensitive information about Zoom users, such as full names, email address, passwords, Zoom account type, session IDs, and more. The accounts exposed do not belong only to individual users, as some accounts operated by medical service companies, academic institutions and some small businesses were also found.
Cyber security course specialists detected this information exposed a few days ago, and theorize that the threat actors behind this campaign are not really looking for an economic benefit, but are trying to mock the affected Zoom users: “On the hacking forum where we found this file, multiple users had posted comments to thank those who leaked the data they also set out their intentions to break into some Zoom sessions,” the experts added.
The link is available to any user who wants to download it, so researchers infer that threat actors aren’t really interested in money.
The International Institute of Cyber Security (IICS) mentions that Zoom has been working on correcting some of the security flaws that have been reported. For the time being, users of this platform are advised to restart their login credentials to prevent any unauthorized access attempts arising from this incident.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











