Coronavirus has been shown to be highly dangerous to people’s health, as well as advancing at an accelerated rate. Faced with the impossibility of leaving home, individuals and organizations resort to remote work, which has favored the increase in the use of Internet communication platforms, such as WhatsApp. However, specialists in a hacking course consider that this practice also puts people’s information security at risk.
Taking advantage of this situation, a group of threat actors has brought back a popular WhatsApp hack active for nearly two years, identified in an active exploitation campaign against multiple users. It is worth mentioning that this attack is relatively simple and has a high success rate.
According to the specialists of the hacking course, the attack works this way: When a user installs WhatsApp on their device, it receives a six-digit verification code via SMS, allowing you to activate the WhatsApp account. Threat actors must have a hacked account and write to a friend of the chosen victim.
The attackers, pretending to be the victims, explain to the friend that they are having supposed difficulties receiving the confirmation code, so they had to ask WhatsApp to send the code to one of their contacts. When sending the code to the attacker, the target user’s account is fully compromised. While threat actors will not be able to access victims’ backups with this attack vector, they would be able to access chat groups, in addition to any new messages or files the victim receives.
The hacking course experts claim that the signs that this is a scam are very clear, although some users easily fall into this kind of tricks. Needless to say, verification codes sent by WhatsApp should not be shared with anyone else, although there are some protective measures in case hackers get any of these codes.
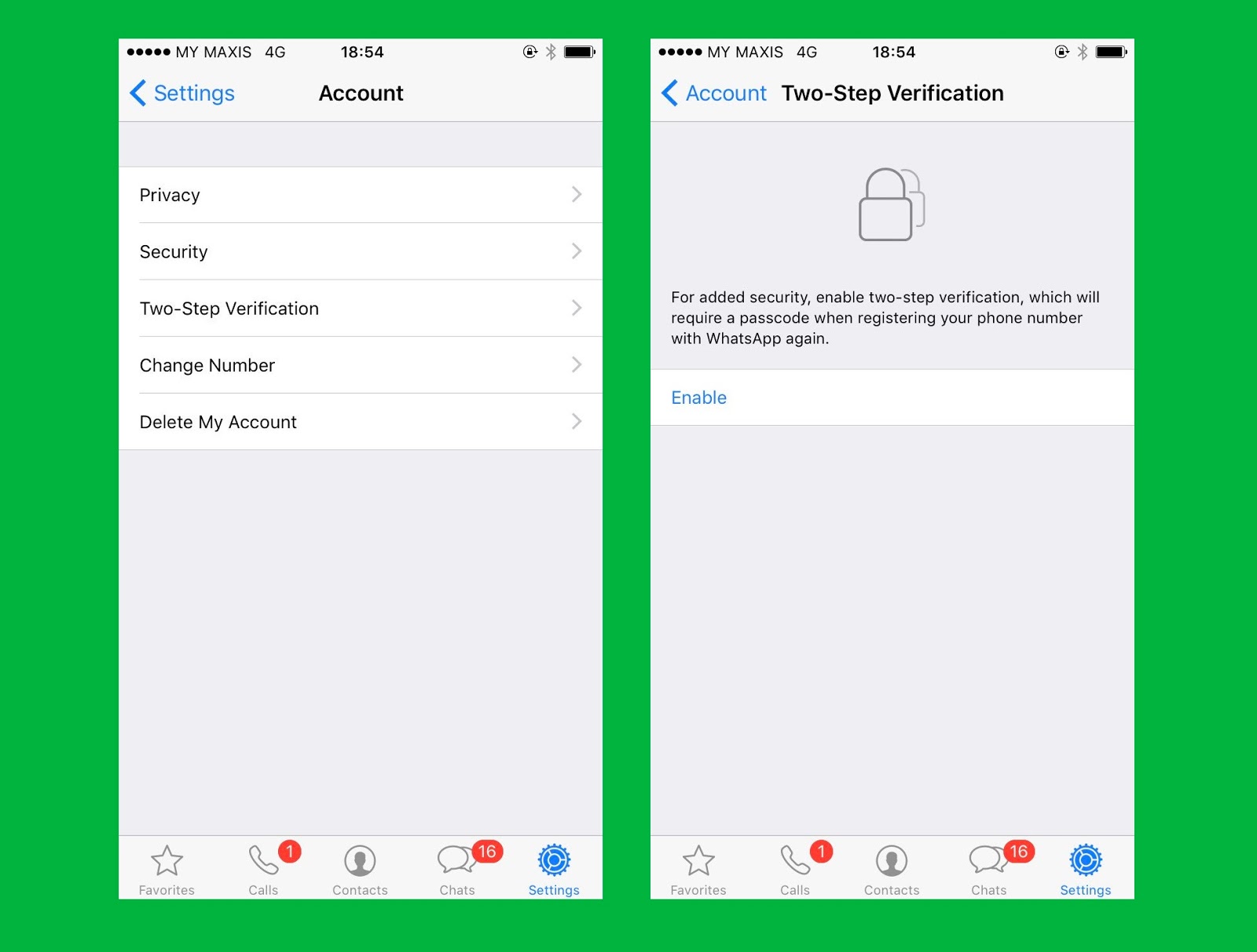
For security, users can enable one of the protections included in WhatsApp, such as two-factor authentication (2FA) or setting an additional PIN to access conversations.
While this service offers end-to-end encryption to users, the International Institute of Cyber Security (IICS) believes that users should remember that there are multiple security risks, making it necessary for users to verify their devices for themselves.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











