Introduction
“Extended XSS Search” is based on initial ideas of XSSfinder. XSS is also called a Cross Site Scripting, it is a type of security vulnerability found in web application. XSS allows an attacker to inject client-side script into web application to perform next level of attacks. According to ethical hacking researcher of international institute of cyber security, Google paid around $1.2 M in XSS bug bounties.
Just a brief intro on XSS, types of XSS:
- Stored XSS (persistent XSS): Stored XSS (persistent XSS) attack is the most dangerous attack when an attacker injects any malicious code into the target application. In case it doesn’t have any input validation, then malicious code will be stored permanently in the target web application.
- Reflected XSS (non persistent): Reflected XSS (non-persistent) when the users enter any data in an HTTP request and HTTP responds back with the same data then it’s an unsafe way of handling data, by using this data attacker can send any phishing email to steal the login credentials.
- DOM-based XSS: DOM-Based XSS (Document Object Model) is same like reflected and stored XSS can occur when malicious code is passed into a URL and client-side reads it to modify the DOM.
Now moving on the tool, we will install this tool in Ubuntu OS. Check the below installation steps.
Environment
- OS: Ubuntu 18.04.4, 64 bits
- Kernel version 5.3.0
Installation steps
- Use this command to clone the extended-xss-search file
root@ubuntu-VirtualBox:/home/webimprints# git clone https://github.com/Damian89/extended-xss-search/ Cloning into 'extended-xss-search'… remote: Enumerating objects: 106, done. remote: Total 106 (delta 0), reused 0 (delta 0), pack-reused 106 Receiving objects: 100% (106/106), 25.64 KiB | 151.00 KiB/s, done. Resolving deltas: 100% (55/55), done.
- Now, lets check the folder created using ls command
root@ubuntu-VirtualBox:/home/webimprints# ls examples.desktop extended-xss-search
- First we have to rename this file example.app-settings.conf to app-settings.conf using this command.
- Run mv example.app-settings.conf app-settings.conf
- For this, we have to move to extended-xss-search folder, using cd extended-xss-search command
root@ubuntu-VirtualBox:/home/webimprints# cd extended-xss-search/ root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# ls config example.app-settings.conf extended-xss-search.py inc logs README.md root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# mv example.app-settings.conf app-settings.conf
- Let’s, check the file, using ls command
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# ls app-settings.conf config extended-xss-search.py inc logs README.md
- Now we can check predefined setting in app-setting.conf file using cat app-setting.conf command.
- We have changed tunneling option in the file.
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# cat app-setting.conf [default] HTTPTimeOut = 10 MaxThreads = 5 ShuffleTests = true [types] OnlyBaseRequest = false UsePost = true UseGet = true [type-settings] GetChunkSize = 150 PostChunkSize = 500 SingleQuoteTest = true DoubleQuoteTest = true EscapedSingleQuoteTest = false EscapedDoubleQuoteTest = false BiggerSignTest = false ExtendedMode = true [tunneling] Active = false Tunnel = 127.0.0.1:8080 [files] Cookies = config/cookie-jar.txt HttpHeaders = config/http-headers.txt Parameters = config/parameters.txt Urls = config/urls-to-test.txt Logs = logs/
- Now, we have to enter the target URLs in the urls-to-test.txt file.
- Use the cd command to move urls-to-test.txt file path.
- cd config/
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# ls app-settings.conf config extended-xss-search.py inc logs README.md root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search# cd config/ root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# ls cookie-jar.txt http-headers.txt parameters.txt urls-to-test.txt
- In the config directory you will see four pre-installed files (Cookie-jar.txt, https-header.txt, parameters.txt and urls-to-test.txt )
- Use ls command to see the files
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# ls cookie-jar.txt http-headers.txt parameters.txt urls-to-test.txt
- To can see the file content use cat command and file name.
- Run cat cookie-jar.txt and match your entries in file.
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# cat cookie-jar.txt examplecookie=31337; testcookie=1; authcookie=1337
- Run cat http-headers.txt and match your entries in file.
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# cat http-headers.txt Accept: */*
- Run cat parameters.txt and match your entries in file.
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# cat parameters.txt test more debug c name
- Now, use nano command to enter the target URLs in urls-to-test.txt file
- Run nano urls-to-test.txt
- Then enter your specific target URLs in that file then save and exit from file.
root@ubuntu-VirtualBox:/home/webimprints/extended-xss-search/config# cat urls-to-test.txt https://admissions.su.edu.pk/
- Now, we have to install webscarab or burp suite application you Linux, to intercept the web requests. We are using webscarab for the demonstration.
- Use this command to run webscarab application
- java -jar webscarab.jar
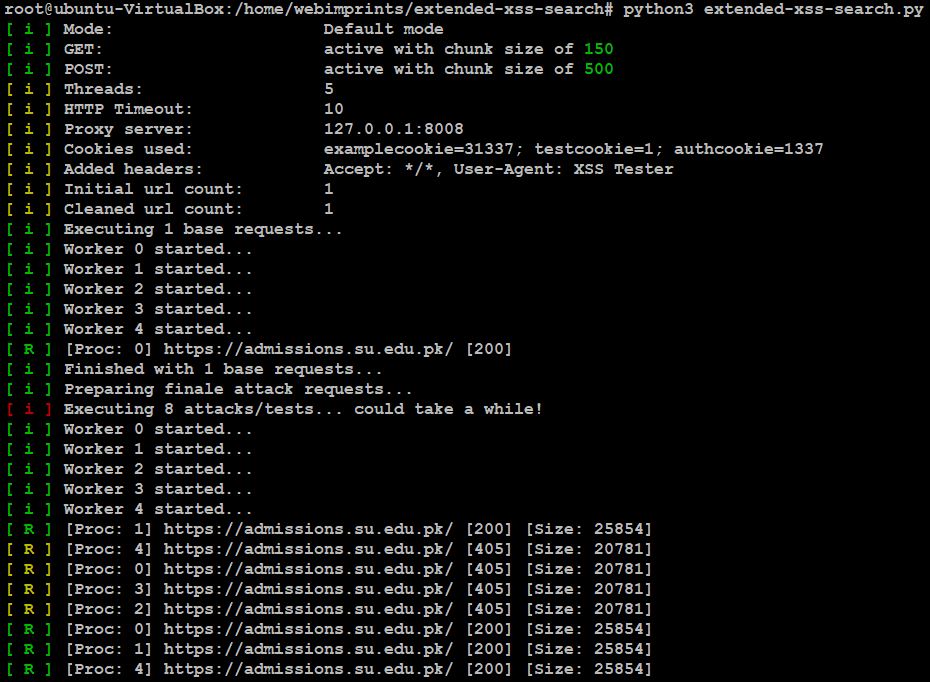
- Now, use this command to test the target URLs.
- python3 extended-xss-search.py
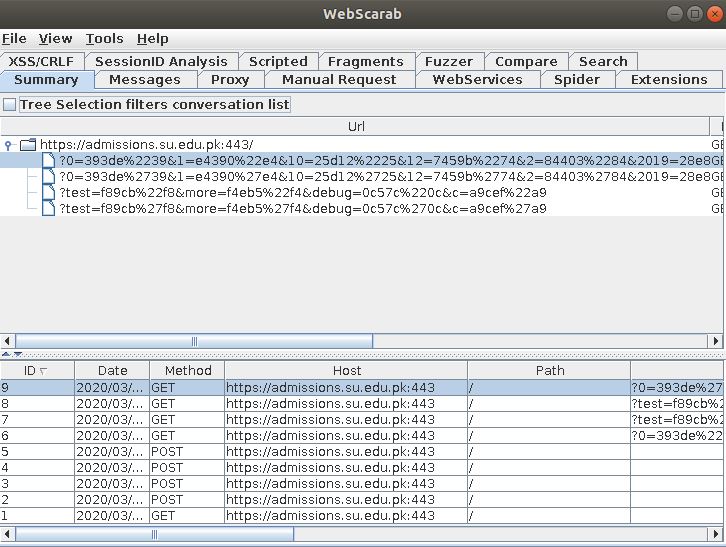
- Now, we can see that webscarab is intercepting all web request to the target domain.
- We can also see that all the parameters are fuzzed and user can also mention any specific parameters or customize parameters to fuzzed in parameters.txt file in config folder.
- Happy bug bounty on your target URL.
Conclusion
We use this Extended XSS Search tool to find out the XSS vulnerabilities in the web application testing on specific URLs. This tool in combination can be used to automate your web application testing for XSS.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










