Introduction
In this smart world everything is connected to the internet, we can find hidden details using a google search engine. Google is used for everything and using this same search engine we can find sensitive information. Hacking using google is also known as Google Dorking or Google Hacking. Google hacking is a passive information gathering technique that is used to extract information and security misconfiguration on the internet.
It uses specialized search query to find out the right results. Some advanced operators like (inurl, filetype, intitle), using these advanced operators we can find out information about the target on internet. According to ethical hacking researcher of International Institute of Cyber Security, google hacking is such an powerful tool to do passive fingerprinting on the target, it can be servers or other service configured incorrectly or it can be logs which contain highly confidential information in clear text. All these scenarios allow hackers to gain control over the target. Moving on to, how we can search passwords, configuration files, emails, open cameras using Google.
FIND OPEN FTP SERVERS WITH GOOGLE HACKING
- Now we will use the dork to search for FTP servers available after 2018. These servers allow you to find out the files for internal use but unknowingly ended up in public access. intitle:”index of” inurl:ftp after:2018. This URL will pull out open FTP servers.
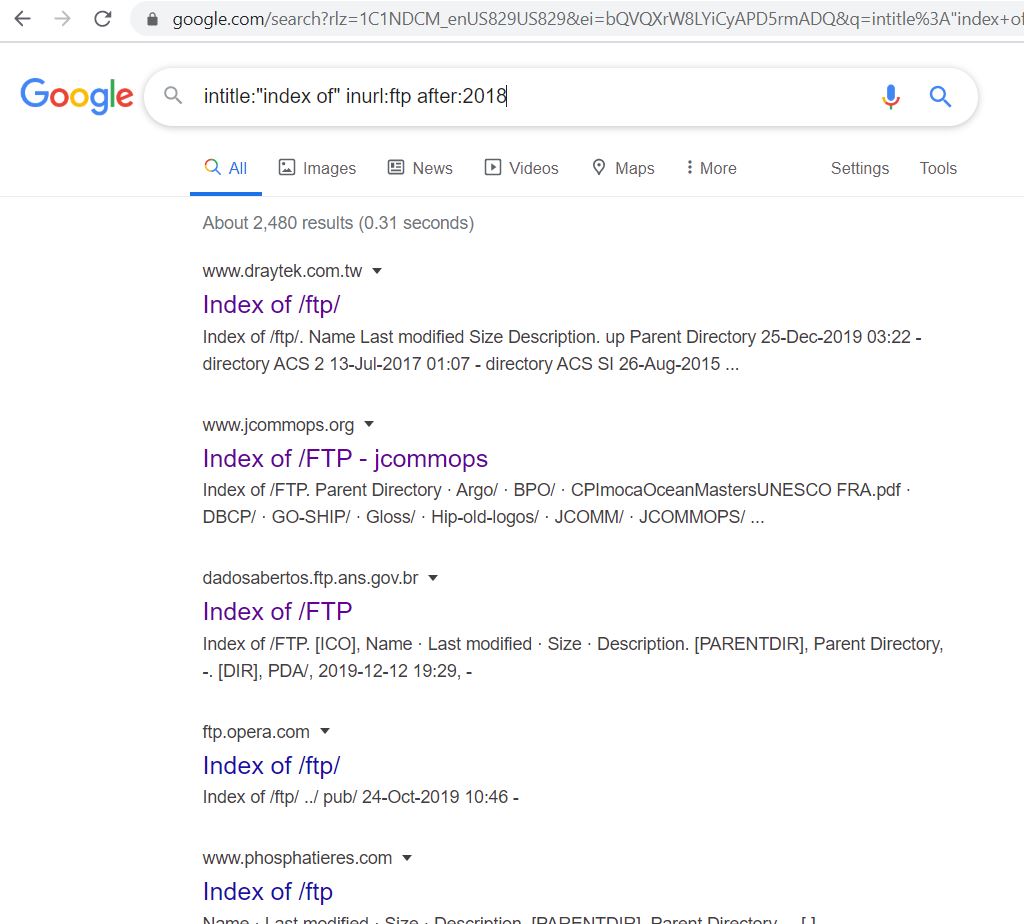
- Now click on any link from this FTP page, let’s see any data is available or not.
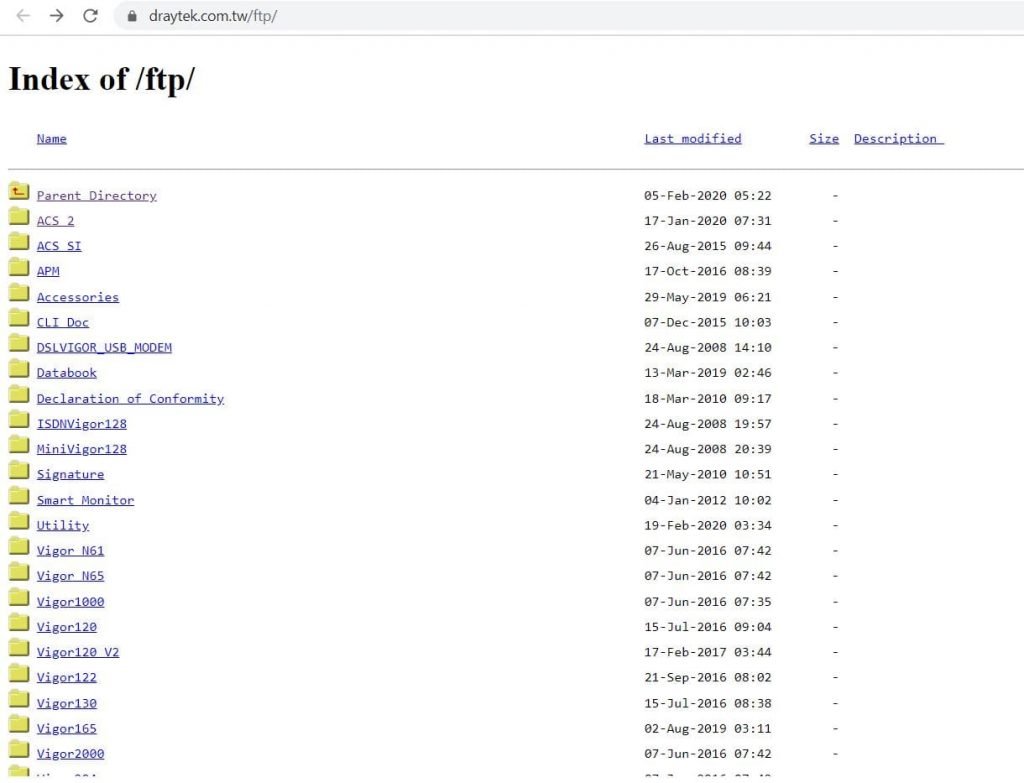
- Yes, we see some data on this.
- Next, let’s open some FTP Files. Check whether we can see any confidential information or not.

- Yes. we see some information.
FIND UNSECURE WEBSITES WITH GOOGLE HACKING
- If we want to find out insecure HTTP pages, we have to modify the query by changing “FTP” to “HTTP” intitle:”index of” inurl:http after:2018. This URL will list out only unsecured HTTP pages, In this results, we can find hundreds of HTTP pages.
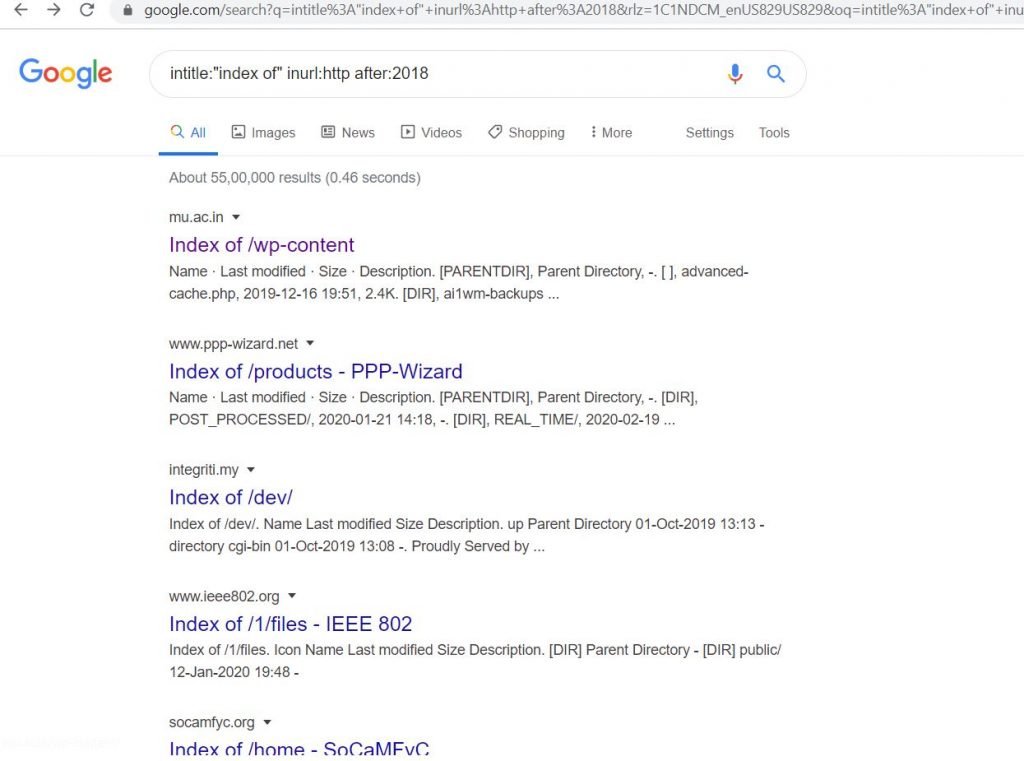
- Now click on any link from that HTTP pages, let’s see any data is available or not.
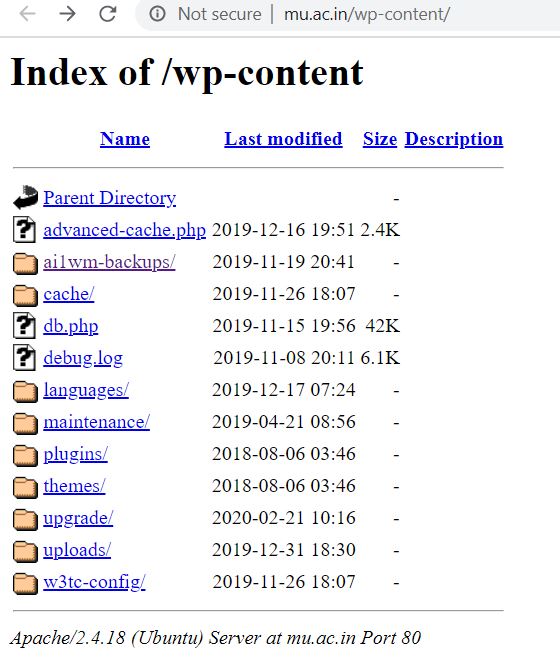
- In the above picture, we see some file containing confidential data in it.
Search Logs For Passwords
- Passwords that are available on internet, you can search using allintext:password filetype:log after:2018. When can see password list in plain text.
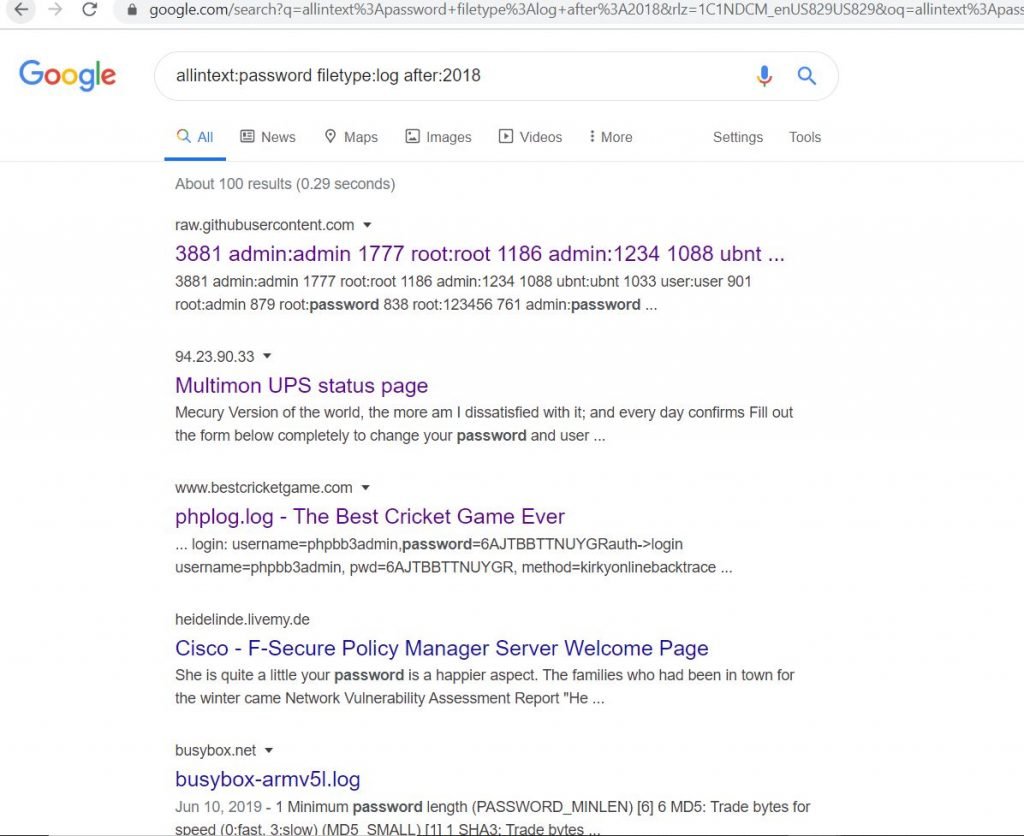
- In the below picture we found some login details like username and password, which is very confidential in nature.
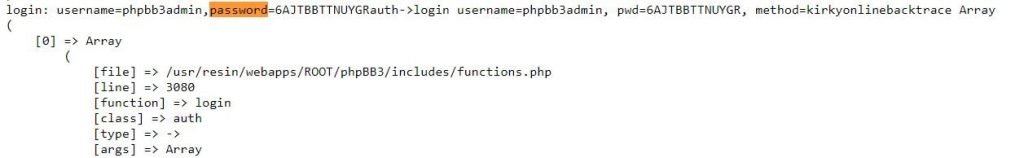
Search For Configuration Files With Passwords
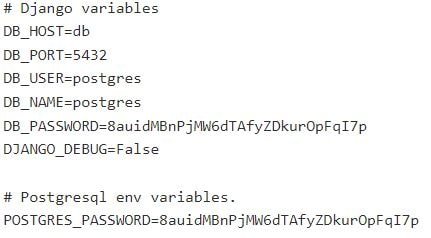
- Configuration files should never be accessible externally. If we use this query filetype:env “DB_PASSWORD” after:2018, we can find some password and database.
- Now, click on any link to check whether we get the password list or not.
- Yes we found login details
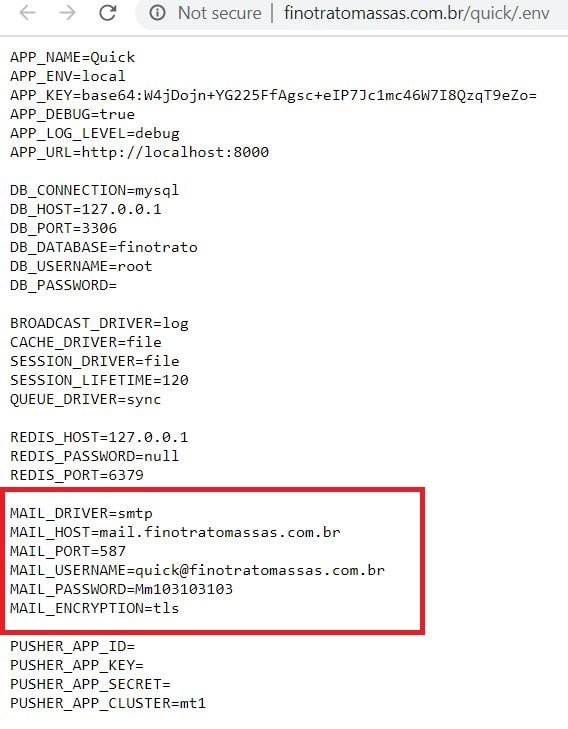
- In some cases, we see invalid URL. In that case, click below arrow after the link, to see the cached option link. Click on it to see google cached pages.
- In the below picture we see another login credentials.
Finding Emails From Google Hacking
- We will search for e-mail lists in spreadsheets (files with the .XLS extension). In the search query, set the file name “email.xls”, by this we can collect emails publicly available.
- Use filetype:xls inurl:”email.xls
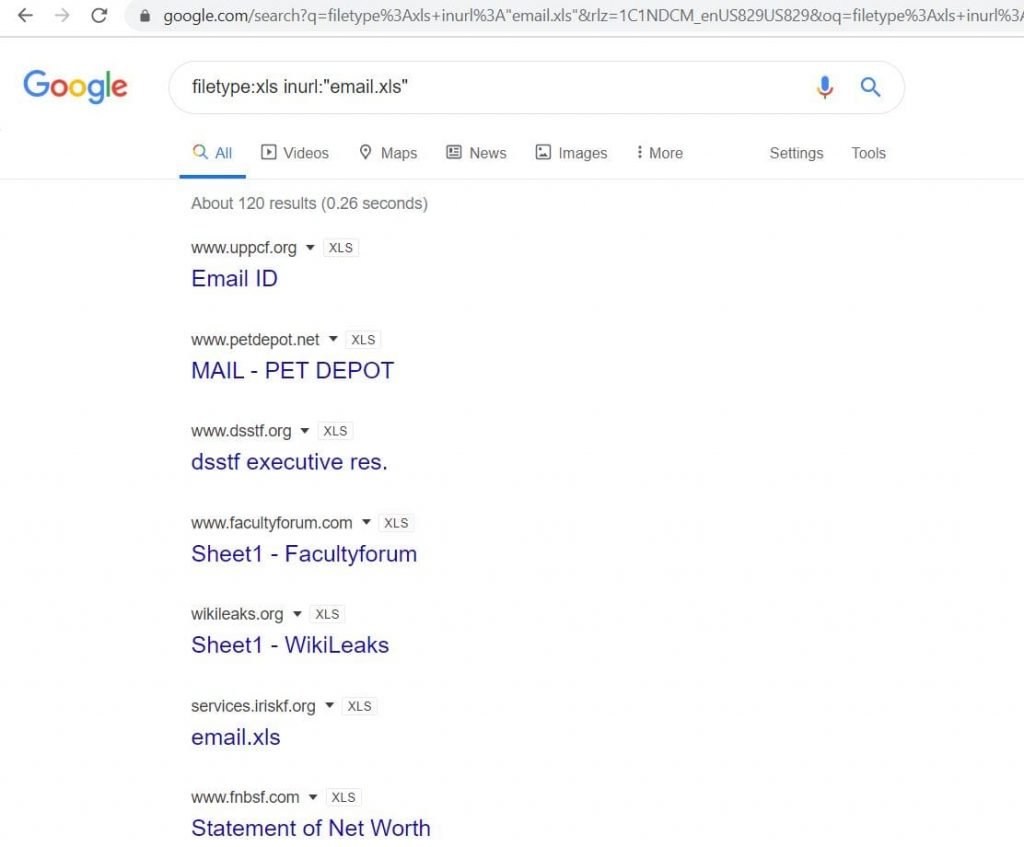
- Now we see Email pages in the above picture, if we click on those links we can directly download the email list.
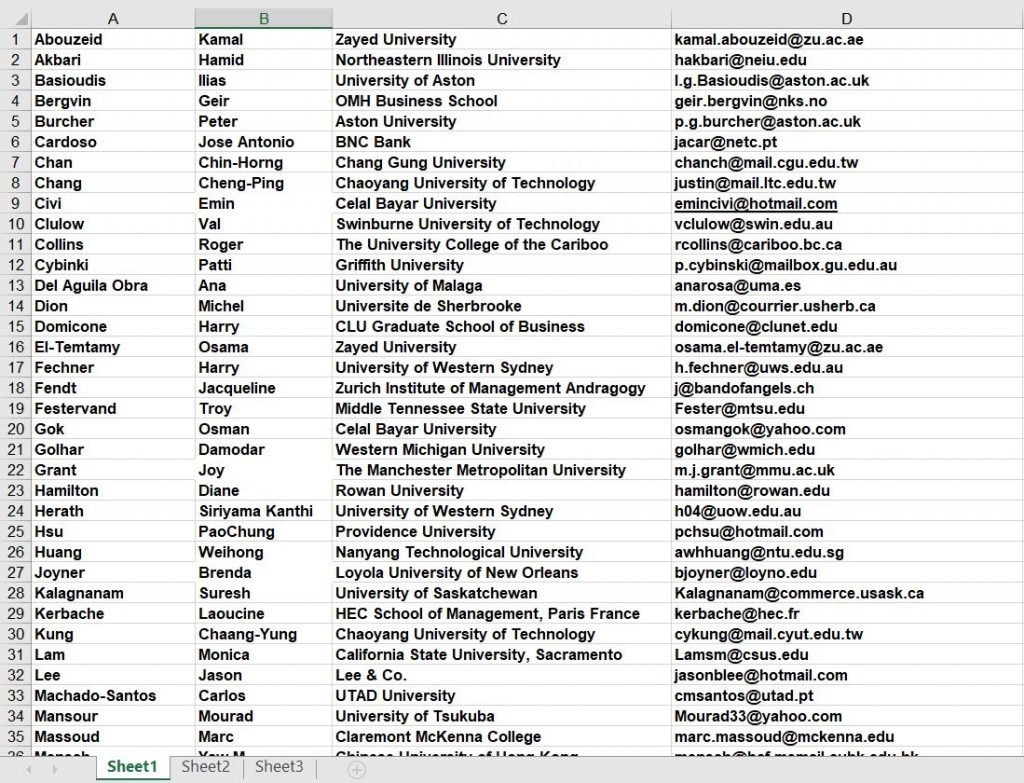
- In the above picture, we see the email addresses in the spreadsheet.
HACK CAMERAS USING GOOGLE
- We can access the camera via HTTP(s) pages. Most common URLs to access camera’s have “top.htm” or “index.shtml”, so we will search “top.htm” in URL along with the current time and date.
- Using the below dork, you will get open camera’s.
- Use
inurl:top.htm inurl:currenttimeOR inurl:/view/index.shtml”Camera”.
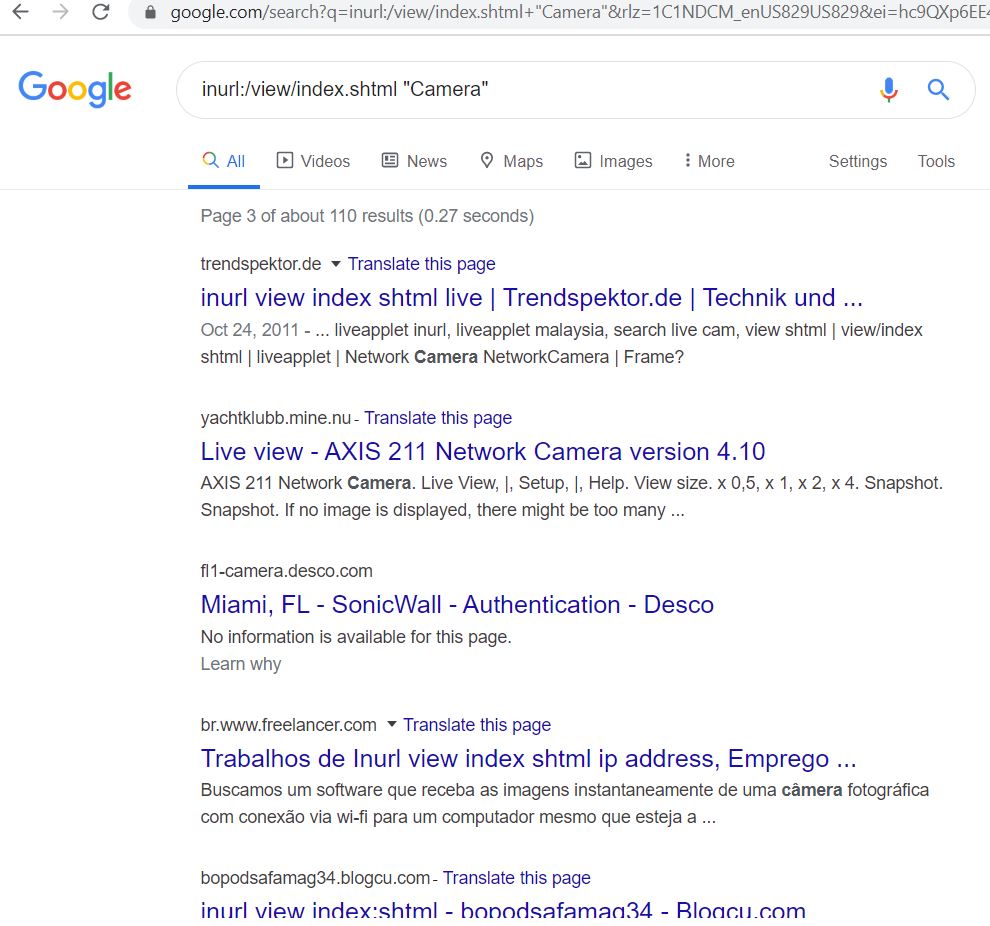
- Now use another query, inurl:top.htm inurl:currenttime, let’s see what we get.
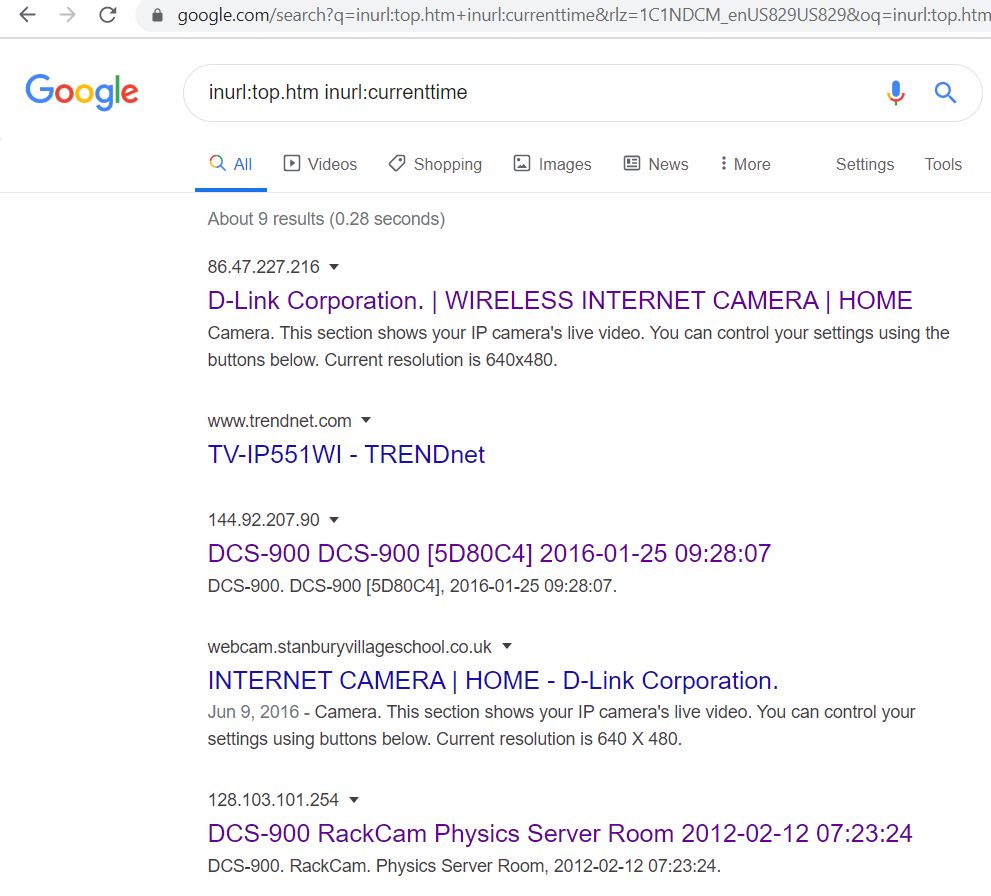
- In above Picture we can see live traffic cameras in the USA, Oregon, city of Salem, this camera is available without a password. This is how google dorks allow you to find authorization pages for cameras with default or no password.
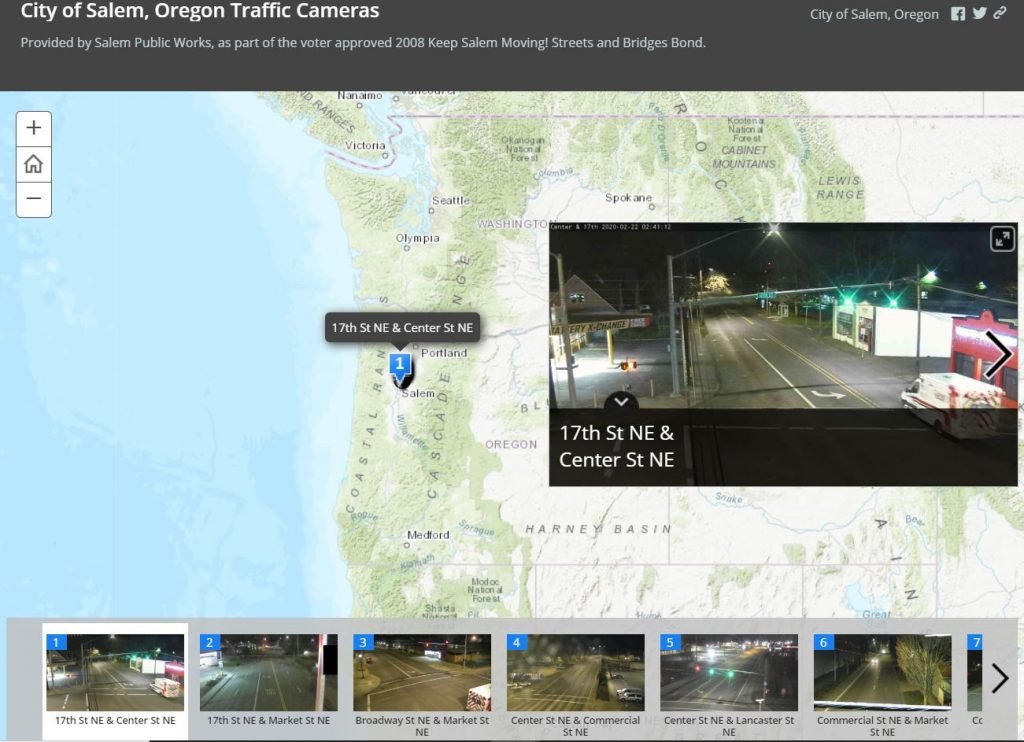
- In the above picture, we saw live traffic cameras in USA.
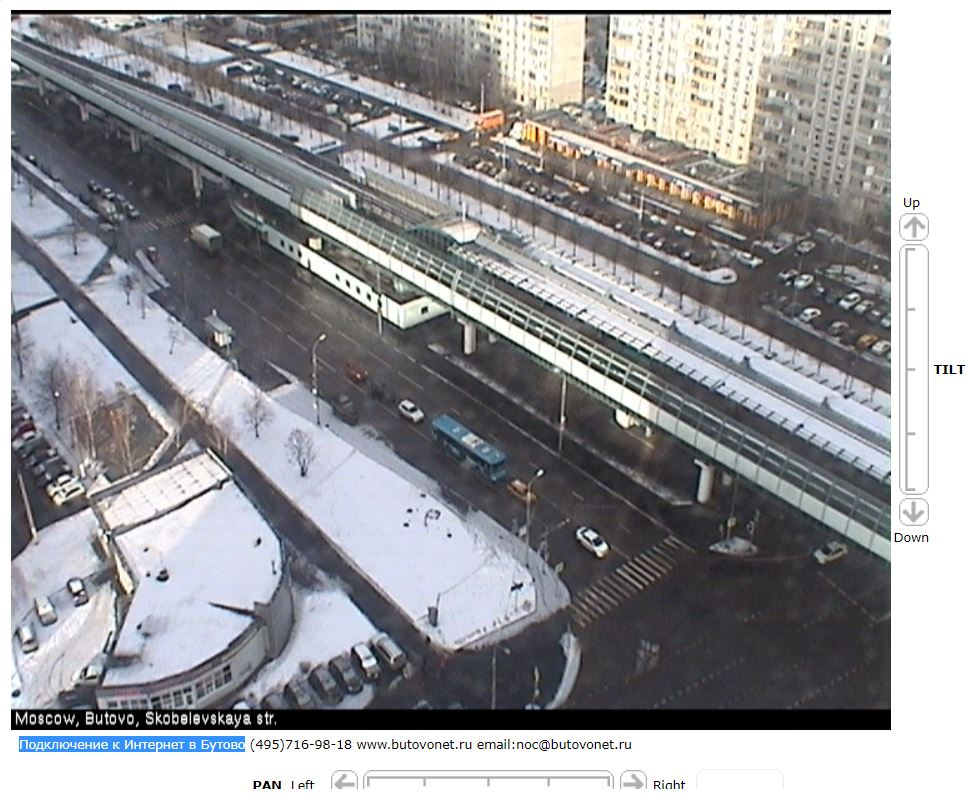
- In the above picture, we see a live traffic camera in Russia.
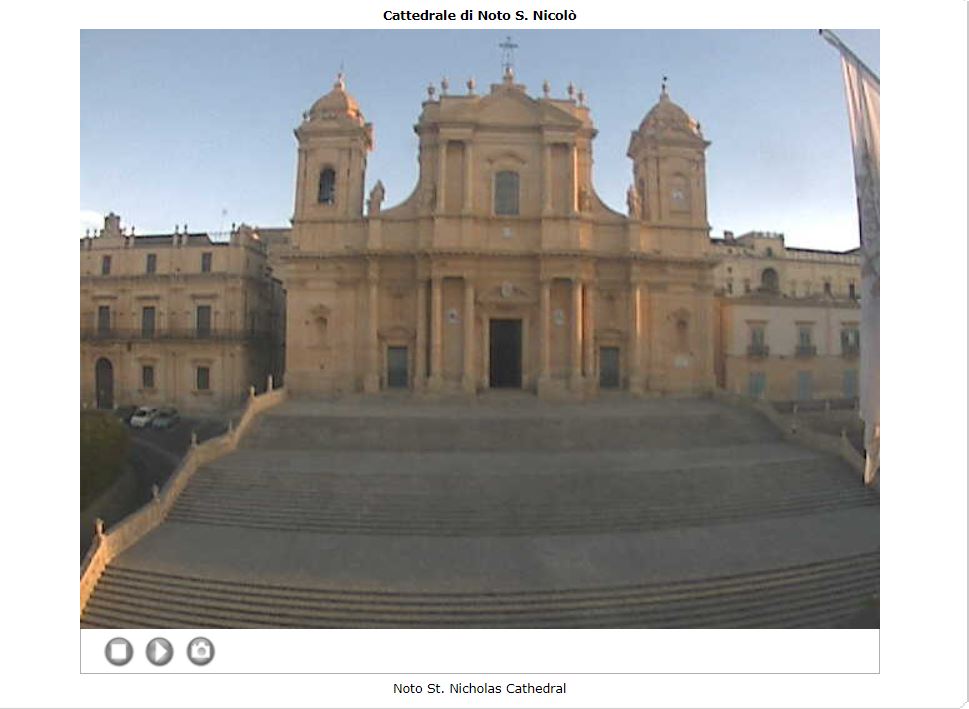
- In the above picture, we see a live camera in Italy.
Conclusion
- Google crawl everything that is connected to the Internet, we should be cautious while connecting devices with default username and password.
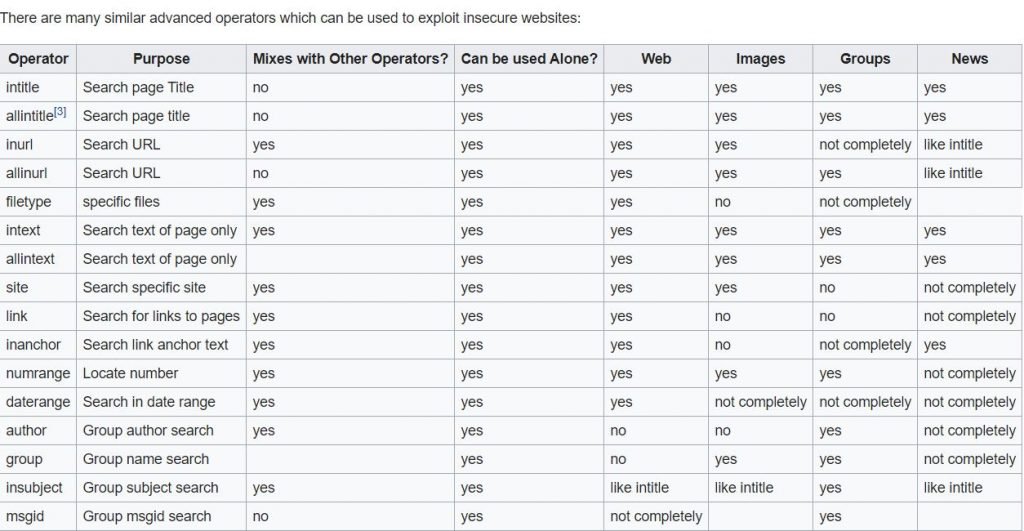
Advanced operators for Google hacking
- These are advanced operators that can be used to exploit insecure devices on internet.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











