For a couple of years now, cybersecurity firms, manufacturers and mainly car owners with keyless opening and start system have reported multiple incidents of “relay attacks”, which consist of the use of wireless signal repeaters to be able to access a vehicle without the owner’s knowledge that they are being stolen.
As if this threat is not enough, the threat appears to have widened for owners of chip keyed vehicles, as a recent report has revealed that it is possible to abuse some cryptographic flaws to create copies of these keys and access a vehicle without any difficulties.
A team of cybersecurity researchers revealed a report detailing the finding of serious vulnerabilities in the encryption systems used by immobilizers in some cars. These immobilizers are radio communication devices implanted in cars to allow ignition according to the signal sent by the car key. Some of the affected model manufacturers include Hyundai, Kia and Toyota, which employ an encryption system known as DST80, from Texas Instruments.

If a hacker could swipe a Proxmark radiofrequency identification(RFID) reader/transmitter device (within reach of almost any pocket) near the chip key or DST80 car, they could get enough information about device encryption; therefore, encryption would no longer be an obstacle between the hacker and the car, allowing them to start the engine. Below is the list of cars vulnerable to this attack*:
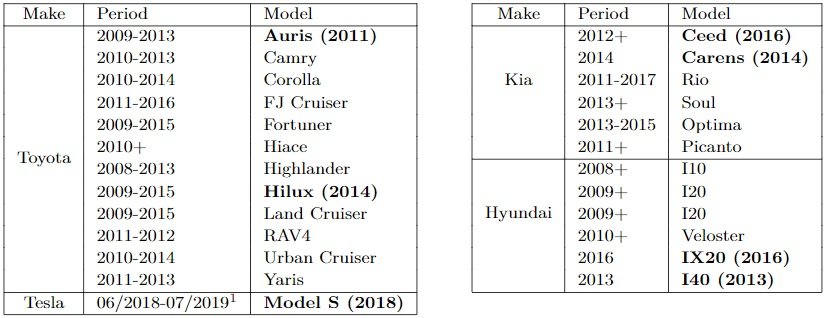
*Tesla recently announced that the vulnerability in the Model S will be fixed with a firmware update.
While other cybersecurity specialists and even Toyota have recognized the existence of these vulnerabilities and the real possibility of an attack in real environments, it should be noted that exploiting this variant is much more complex than, for example, in a relay attack. In most cases, threat actors only require a couple of devices to replicate the signal transmitted by the smart keychain, plus this attack is stealthier and allows thieves to keep distance from the target.
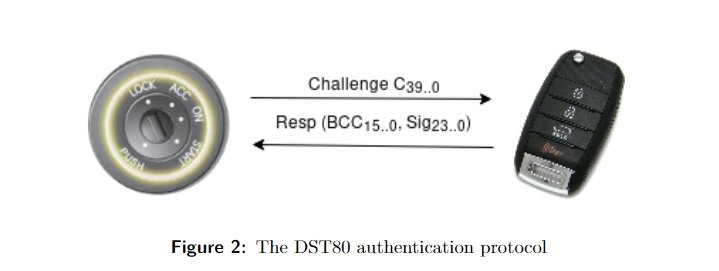
Moreover, the key cloning attack described by researchers requires threat actors to scan the target with RFID reader just inches away. Finally, we must remember that this technique is focused on cars with a key ignition mechanism, so a hacker who manages to access the vehicle will still have to find a way to turn the ignition barrel without the car key.
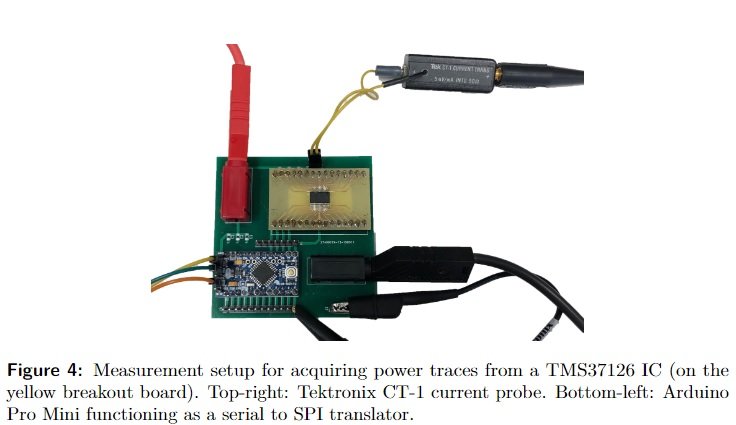
While this limits the actions of threat actors, cybersecurity researchers point out that in some cases it would be enough to insert a screwdriver into the barrel to turn it over and start the car. “Manufacturers did not implement the appropriate safety measures in the mechanical aspects of the auto,” says one of the researchers. For security, the published report does not have all the technical details to replicate such an attack in a real-world environment. The different companies have already been informed, although not all have responded to the finding.
According to the International Institute of Cyber Security (IICS), a potential solution to this threat is the reprogramming of immobilizers, although some manufacturers would have to replace the keys with a chip to completely mitigate the risk. However, the exact steps each company will take to address this problem are still unknown.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











