After reading this note, you may rather keep using your old bike. Renowned information security researcher Bon Diachenko reported the discovery of a database exposed online, which contained at least 450,000 records belonging to motorcycle company Royal Enfield.
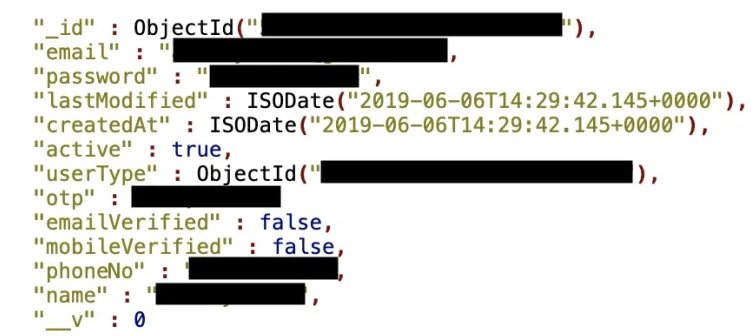
The compromised information include confidential details of the firm’s clients that have a user profile on the Royal Enfield website, including full names, email addresses, phone numbers, encrypted passwords and even links to some social media profiles.
In his report, the information security specialist mentions having found “three IP addresses with misconfigured databases (in other words, with no password or login); the exposed information suggests that the database is owned by Royal Enfield.” In addition, Diachenko ensures that the database includes records of “at least 1,400 privileged customers and distributors”.
SOURCE: Bob Diachenko
Bob Diachenko mentions that he detected the vulnerability on January 19, and immediately notified the motorcycle company’s information security team. A few hours later, access to the compromised information had been shut down; however, Diachenko believes that the information was exposed for at least two weeks. No representative of Royal Enfield has offered public statements regarding the incident.
Diachenko has collaborated on a number of reports on data breach incidents recently, including government organizations such as the Indian Space Research Organization (ISRO), the Bhabha Atomic Research Center (BARC) and the Securities and Exchanges Board of India (SEBI), which have been compromised by database configuration errors. Affected organizations have been lucky enough to get the reports, although in other cases the compromised information can quickly reach the hands of the threat actors, who sell these stolen databases on multiple malicious hacking forums. Leaked databases are the object of desire of cybercriminals, especially when they include financial information of victims.
According to the International Institute of Cyber Security (IICS), oversights and errors of the administrators of these implementations are the main cause of these incidents, so organizations must update their methods and establish guidelines for stricter data security.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











