A serious incident appears to have jeopardized all the work of students, academics and researchers at the Madras Indian Institute of Technology, one of Asia’s leading technology research centers, according to data protection experts. Apparently, those affected have been infected with an unknown variant of ransomware. Although the administration claims to have support for all the compromised information, many fear that it will be impossible to recover their research, projects, documents, reference material and so on.
One of the affected researchers shared via Twitter a screenshot of the message they received after loggin into their servers, which is supposed to be a ransom note.
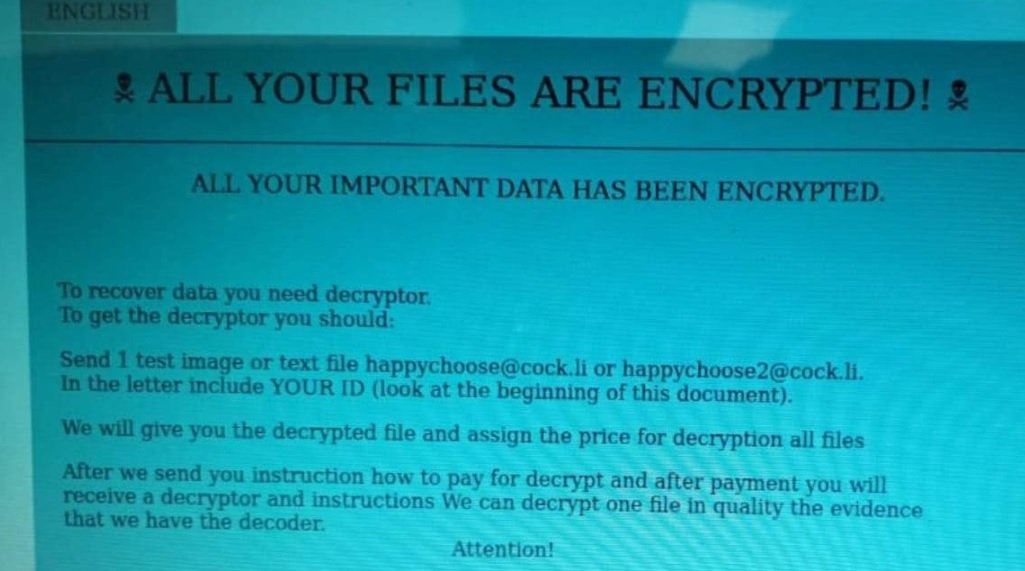
In this message, hackers assure all data stored on IIT’s systems has been encrypted and victims have to pay a ransom to get the decryption key. To contact the attackers, victims should use nothing but the email address they provide in their message (happychoose@cock.li). “After that, you are supposed to get a decryption tool with the instructions to use it”, mentioned the affected data protection expert.
In response to massive concern, IIT’s General Secretary has asked all staff, investigators and students to back up their data: “We are under a serious attack that has compromised all computers running Windows system used in the campus. We are asking users to backup their data as soon as possible”. Besides, campus’ administration fears that attackers are aiming to critical computers on IIT’s networks, as a point to access other parts of their systems and deploy second stage attacks.
Manu Zacharia, a data protection specialist, has told about this incident: “This is obviously a massive ransomware attack. Attack methods used by this hackers seems to be quite sophisticated, as ITT’s servers had stop working long before the ransomware were detected”. In addition to Zacharia’s statements, other cybersecurity firms assured IIT is a usual cyberattack target.
At this point, admins don’t seem to have a backup plan; nonetheless, International Institute of Cyber Security (IICS) considers that it could be a matter of time to know the firsts details on the incident, such as the malware variant used by the attackers, their method or the sum demanded to victims.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











