Ransomware remains one of the most used attack variants by cybercriminals, and new ways of using encryption against victims are detected at every moment. Cybersecurity firm Emsisoft has reported the detection of a new variant of ransomware, known as “Ransomwared”, which exhibits somewhat different behavior from other similar attacks.
As we know, in a ransomware attack threat actors encrypt the files of victims to demand a ransom in cryptocurrency in exchange for re-establishing everything to normal. The main difference with Ransomwared, is that the operators of the attack do not demand money, but instead assure victims that they will only be able to recover their files if they send intimate photos to an email address controlled by the hackers.
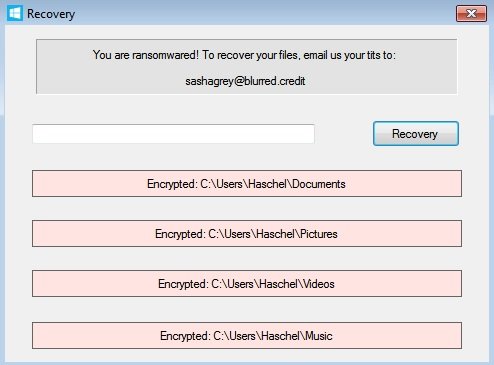
After infecting the target system, Ransomwared encrypts the victim’s files and adds them the .ransomwared or .iwanttits file extensions. Finally, the victim finds the ransom note with the unusual request: “You are ransomwared; to recover your files, email us your tits to…” mentions the ransom note found by cybersecurity specialists.
SOURCE: Emsisoft
In its report on the finding, Emsisoft mentions: “We are not sure how threat actors get to know if a photo belongs to the victim, so sending any image available on the Internet could be enough to regain access to their files”.
Still, cybersecurity experts managed to promptly develop a tool to remove Ransomwared encryption, so they recommend not interacting with attackers and recovering compromised files using the free tool, available here. In case you experience any problems while using this tool, contact Emsisoft team.
So far it is unknown whether there is a group of sophisticated threat actors behind this new ransomware or if it is an amateur development. There are also no further details about Ransomwared’s distribution methods or whether its developers are involved in other criminal activities.
The International Institute of Cyber Security (IICS) has tracked the latest reports of ransomware attacks in order to find potential distribution channels, similar file extensions, and other indicators on the possible developers and their main objectives.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











