A couple of months ago, the EUtoday website published an ethical hacking report on the security of RSA certificates, mentioning that, while this is a secure algorithm (based on calculation with prime numbers), its misuse would allow the generation of vulnerable or fake certificates, which could lead to multiple security issues. These issues also affect Internet of Things (IoT) devices, as using fake certificates could allow an attacker to deploy distributed denial of service (DDoS) attacks, information theft, and other malicious activities.
RSA certificates are an example of public key cryptography. This method uses two different encryption keys: a private key and a public key. The private key is used to decrypt messages or generate digital signatures, while the public key can encrypt data or verify digital signatures. This method is safe as long as an attacker does not know either of the two factors used for RSA calculation.
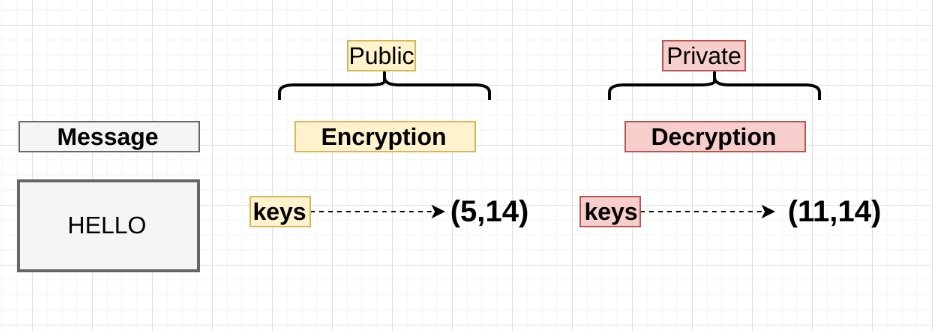
However, ethical hacking specialists consider this assumption will not always be valid, as demonstrated in a study of 75 million public RSA keys, one in 172 of these keys share a common factor.
These common factors represent a serious security issue for RSA keys, as they could allow a threat actor to determine the two prime factors used in the calculation. This information would help to derive the private key associated with the public key. In the study, researchers managed to find the private keys for more than 435k out of the 75 million RSA keys analyzed.
In their report, ethical hacking specialists attribute this security weakness to the continued growth of IoT device use, as they have reduced entropy and significant energy constraints. It should be noted that entropy is a fundamental factor in generating a secure random key; since these devices generate the same random numbers frequently when they try to identify prime numbers to use in RSA certificates it greatly increases the chance that these certificates will share a prime value, becoming vulnerable to attack.
According to the International Institute of Cyber Security (IICS), it is vital to address these security risks, as we can currently find IoT devices in virtually every home in the world, so their use for malicious purposes could expose millions of users.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











