An information security firm just reported the finding of a critical vulnerability in systemd, the Linux initialization subsystem. If exploited, the vulnerability would allow a threat actor to execute code with administrator privileges on the affected system by sending specially designed queries through DBus.
According to the report, the flaw, tracked as CVE-2020-1712, is present in Ubuntu, Red Hat, Fedora, RHEL, CentOS, SUSE/openSUSE, and ROSA, and received a score of 7.8/10 on the Common Vulnerability Scoring System (CVSS) scale. The security issue was reported by researcher Tavis Ormandy of Google Project Zero.
At this point, only Red Hat has made a position on this finding, mentioning that the issue does not affect systemd versions included in products such as Red Hat Enterprise Linux 7, as there are no services that make vulnerable asynchronous Politik requests.
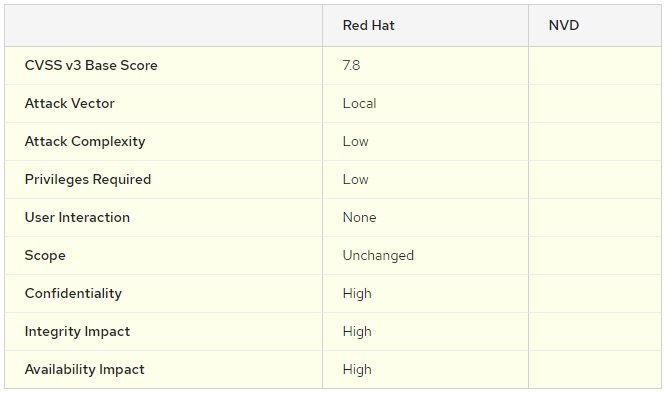
The use-after-free vulnerability occurs when asynchronous Polkit queries are performed while handling DBus queries; even a local attacker without elevated privileges could abuse this failure to block some services on the target system, execute arbitrary code, and perform privilege escalations using specially designed DBus messages.
The information security experts report mentions that if DBus uses bus_verify_polkit_async(), it can take quite a while to complete the action in the Politik library. If this happens, the method handler will be called again with the previously assigned user data.
If the request to Polkit takes too long, flushing the cache releases the stored objects before calling the method again, triggering the use-after-free flaw.
According to the information security report, the vulnerability is exploitable by the systemd-machined service, which provides the org.freedesktop.machine1.Image.Clone API. This interface is accessible to all users without system privileges, which means that any user could trigger the failure or achieve code execution with superuser privileges.
The International Institute of Cyber Security (IICS) frequently reports this kind of errors in various technological developments, contributing to the formation of a collaborative ecosystem to improve security in the field of computing science.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










