Since its emergence, Emotet has been one of the most active malware families among cybercriminals, who constantly develop new versions of this malware. One of Emotet’s most recent samples allows hackers to spread over insecure WiFi networks nearby an infected device, as mentioned by network security specialists.
In case you find a nearby WiFi network, Emotet can infect any connected device, meaning great attack potential for malware developers. This new version of Emotet includes new social engineering evasion tactics to perform malicious activities like credential theft, Trojan deployment, among others.
Although the first records of this wireless malware propagation binary occurred in early 2020, network security specialists mention that the executable has a timestamp of April 16, 2018, meaning that this attack vector remained unnoticed for almost two years.
This new version of Emotet infects the target device with a self-extracting RAR file containing two binaries (worm.exe and service.exe) used for propagation via WiFi. After decompression of the RAR file, the worm.exe binary runs automatically. After execution, the binary begins to scan for other WiFi networks for propagation. Emotet uses the wlanAPI interface, used to manage wireless network profiles and network connections.
When obtaining a WiFi identifier, the malware calls WlanEnumInterfaces (function to enumarate all available networks on the victim’s system). This function returns the wireless networks listed in a series of structures that contains all their details (SSID, signal, encryption, authentication method, etc.).
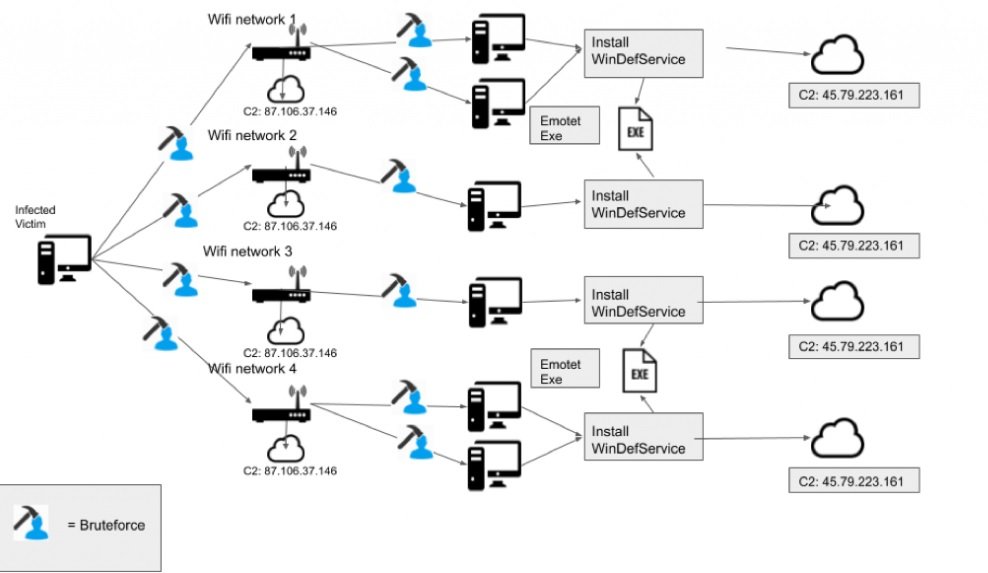
When data collection for each localized network is complete, Emotet deploys a ‘brute force loop’ to access the attacked networks; if it fails to connect to a target network, the function is repeated on the next network. Network security experts have not determined how hackers obtained the password list, although it may be the product of a data breach.
In case of finding the correct password and realizing the connection, the malware stays asleep for about 15 seconds before sending an HTTP POST to the attacker’s C&C and establishing the connection to the WiFi network. Finally the built-in Emotet executable is delivered, so that the malware begins to infect all possible devices.
Network security experts at the International Institute of Cyber Security (IICS) mention that one of the main ways to protect against potential Emotet infections is the establishment of strong passwords, since the list of passwords used by hackers should contain, for the most part, factory passwords for WiFi devices.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










