A serious discovery threatens the network security environment of thousands of organizations around the world. A series of vulnerabilities were recently found in various Cisco enterprise products (IP phones, switches, firewalls, cameras, among others) that, if exploited, would allow threat actors broad access to affected enterprise networks. Cisco is the leading provider of this class of devices for corporate environments, so millions of users are at risk.
A malicious hacker could exploit some of these vulnerabilities (aiming against a switch, for example) to collect large amounts of unencrypted internal information and then scroll through the compromised network. In addition, attackers could exploit other known vulnerabilities to attack multiple Cisco devices at once to turn them on/off at will, use them as an access point, and as a means of collecting sensitive information.

SOURCE: Armis
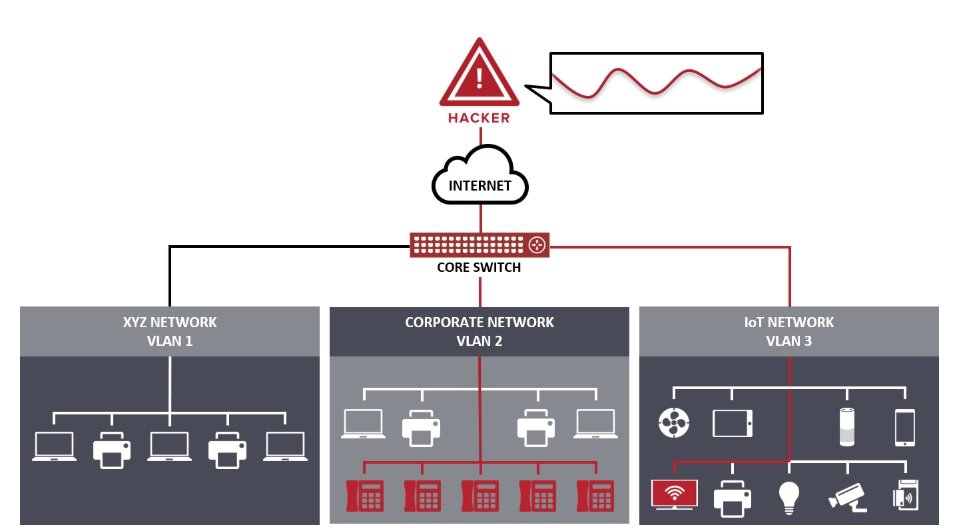
According to Ben Seri, from the network security firm Armis, the flaws originate, ironically, from the implementation of a network security strategy known as segmentation, which consists in isolating different parts of a network to avoid large extent problems: “The segmentation of a network is key to its protection, although exploitable security holes are sometimes created, which can be beneficial for groups of threat actors,” he says.
Vulnerabilities specifically reside in Cisco Discovery Protocol (CDP), a mechanism that allows company products to transmit their identities to each other within a private network. All network devices employ similar mechanisms, although CDP is a patent owned by Cisco.
SOURCE: Armis
Although using CDP facilitates some network features, it also represents an easy access point for threat actors. To make matters worse, these vulnerabilities can be exploited to attack dozens of devices simultaneously or to take control of critical devices on the compromised network, the network security firm report mentions.
In total, Armis experts detected five vulnerabilities, which were reported to Cisco at the end of 2019. Since then, the tech company has been releasing security updates for potentially affected products, a complex task because the CDP mechanism is not fully identically implemented in all Cisco developments.
According to the International Institute of Cyber Security (IICS), this arduous work not only involves the automatic installation of security updates, as many of the affected devices will need to be manually updated to mitigate exploitation risks, so months of work remains ahead for IT areas in the companies that use these products.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











