This has been a busy week for Cisco’s vulnerability testing team. A few hours ago, the company announced to its users that some of its Small Business Switch devices, widely used in small and medium-sized businesses, have some vulnerabilities considered critical; if exploited, these flaws could allow the exposure of sensitive information and the deployment of denial of service (DoS) attacks.
Cisco received the report of these vulnerabilities (tracked CVE-2019-15993 & CVE-20203149) from an information security firm. Flaws affect the web management interface of compromised devices and can be exploited by unauthenticated remote users.
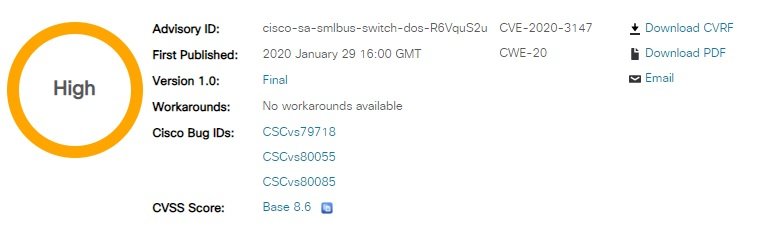
In its vulnerability testing report, Cisco mentions that the potential leak of sensitive information exists due to the absence of adequate authentication controls, plus, all that a threat actor requires to exploit the flaw is send specially crafted HTTP requests to the switch’s web management interface.
Regarding the DoS vulnerability, Cisco mentions that it exists due to incorrect validation on requests sent to the switch web interface. The flaw can be exploited to cause the target device to reload and enter a DoS condition with sending malicious requests. The DoS vulnerability affects the following Cisco products as long as they are running a firmware version earlier than 1.3.7.18:
- 200 Series Smart Switches
- 300 Series Managed Switches
- 500 Series Stackable Managed Switches
The Cisco vulnerability testing team mentions that both security bugs have already been addressed, and cases of active exploitation in the wild are still unknown. So far, there are no functional workarounds, so administrators of affected products are advised to install updates as soon as possible.
This is the third time in less than a week that Cisco has released security updates for some of its products. Just a couple of days ago, the International Institute of Cyber Security (IICS) reported a vulnerability in Webex that could be exploited to access any video conferencing session without the need for a password; the flaw promptly corrected, although it is likely to have been exploited prior to the release of the security patch.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










