A couple days ago, multiple cybersecurity firms reported that a group of hackers, allegedly from Saudi Arabia, took control of the Twitter accounts of half of National Football League (NFL) teams.
Although the administrators of these accounts managed to regain control, it appears that these hackers’ campaign is not over, as multiple users began reporting anomalous activity on various ESPN-controlled Twitter and Instagram accounts. The compromised accounts were @ESPN (the main media network account), @SportsCenter and @NBAonESPN, from where hackers posted some tweets that have already been deleted.
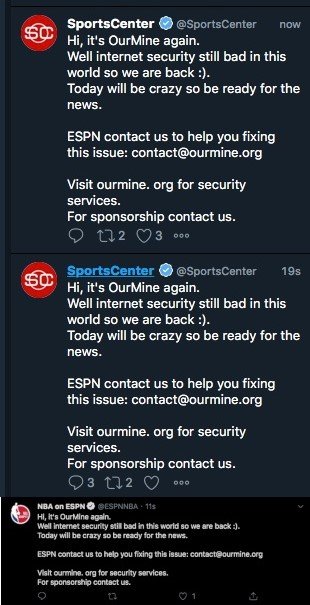
Doha Madani, NBC News reporter, was the first to attribute the incident to the Saudi hacking group, known as OurMine: “Someone contacted us via email; apparently, the email account was operated by OurMine. Alleged hackers mentioned that, in 2017, they had to stop their activities, although they have now returned,” she said. In addition, NBC News mentions that, in their message, hackers assured that they choose their targets randomly, although they did not reveal the process they used to compromise the NFL Twitter accounts.
While more details about the incident are unknown, ZDNet cybersecurity experts say all this has to do with a security incident in Khoros, a digital marketing and public relations application. Multiple companies, including NFL teams, use this tool, linking it to their social media accounts. ZDNet’s theory is that Khoros’ security has been compromised.
However, a Khoros spokesperson denied that a cybersecurity incident has occurred on the platform: “Right now we’re helping a customer with an access issue not to authorize their accounts.” The firm did not mention the name of the affected customer, although it is most likely the NFL and its teams.
While this incident is resolved, there is still an investigation into what happened in ESPN accounts; normal activities in the compromised accounts have already been restored. The International Institute of Cyber Security (IICS) believes that both attacks have most likely been perpetrated by the same hacker group, although it is still investigating whether OurMine has actually reappeared, or if they are threat actors taking the name of a group of hackers renowned in the past.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











