Despite current technological advances, many cybercriminal groups keep resorting to old tricks to scam their victims, simply adding some variants to their attacks. On this occasion, a cybersecurity firm has released a report on a new version of the classic scam known as “Law Enforcement Lock”.
In essence, the scam works as follows: Using the Chrome browser, threat actors look for a way to redirect visitors of some websites to other pages, which display a full-screen image containing a notice, supposedly issued by some local law enforcement agency. This message informs the user that their computer has been blocked as part of the investigation of any crime related to pornographic or child abuse content.
Subsequently, criminals inform victims that they can unlock their devices immediately by paying a credit card fine. According to cybersecurity experts, criminals include links to legitimate law enforcement agency sites, official logos and even known legal terms to make this charade more convincing.
Needless to say, the device is not actually locked, but only the message is displayed in full screen. Although it seems like an ineffective attack method, it is surprising to find the high numbers of users who have fallen into this trap, cybersecurity firms say.
The message shown to users varies depending on the country, although it broadly mentions: “According to the law of (country of origin of the victim), your browser has been blocked due to the viewing and dissemination of pornography, pedophilia or bestiality content. To unlock your device, you should pay (specified amount) with your Visa or MasterCard”.
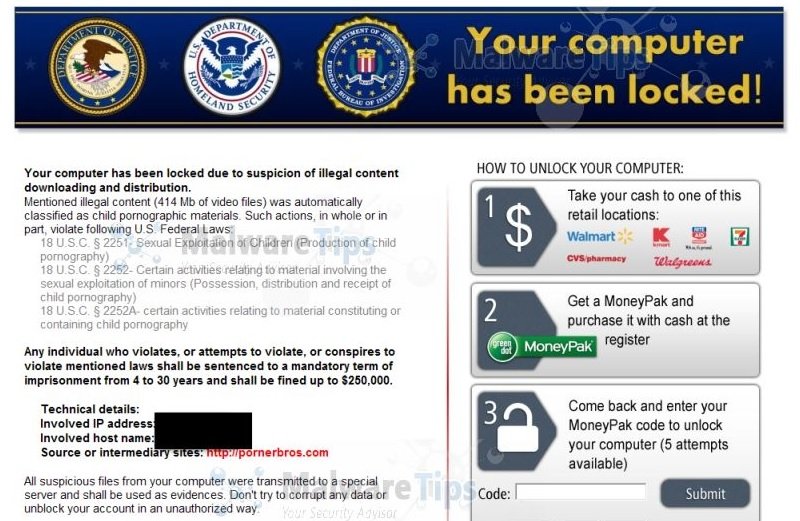
SOURCE: MalwareTips
In addition, the message ensures that, in case victims do not pay the fine or attempt to unlock the device by other means, the alleged illegal material will be sent to local law enforcement agencies, which would initiate legal proceedings against the victim of the scam.
The perpetrators of these attacks not only get money transfers, but sell victims’ information through hacking forums on dark web, so the attack can bring disastrous consequences. The International Institute of Cyber Security (IICS) reports that, because criminals usually do not master the language in which they write these threatening messages, verifying grammar and writing can be critical to avoid falling into the scam.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











